
Three open purple-pink poppy blossoms on long stems with four seedheads on stems behind on a cream background
'Wild Poppies' by Colleen Parker, contemporary artist and illustrator #womensart
06.07.2025 07:46 — 👍 4521 🔁 475 💬 0 📌 22@raj2569.bsky.social

Three open purple-pink poppy blossoms on long stems with four seedheads on stems behind on a cream background
'Wild Poppies' by Colleen Parker, contemporary artist and illustrator #womensart
06.07.2025 07:46 — 👍 4521 🔁 475 💬 0 📌 22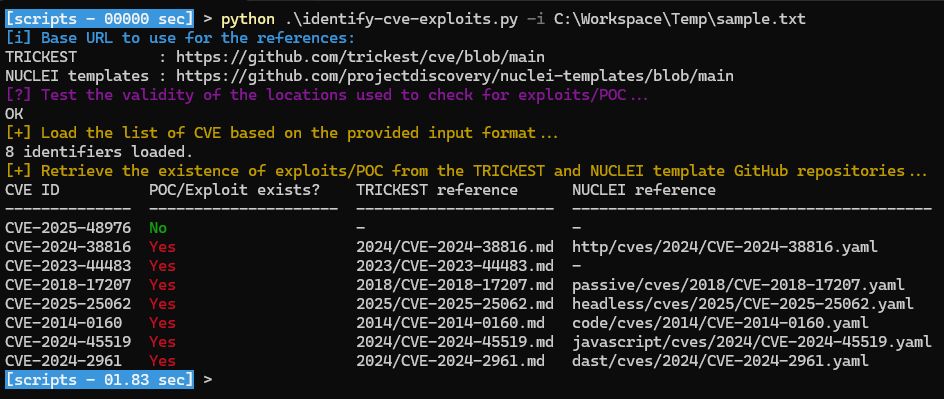
🔬 When I perform a secure code review, I also check whether the external components used are affected by public vulnerabilities (CVE). Recently, after a advice from my manager on this subject, I tried to go further and check whether the CVEs identified had a POC/Exploit.
#appsec #appsecurity #cve

Garden flowers of many colours, painting.
🖼️ Katherine Bilokur
05.07.2025 13:48 — 👍 212 🔁 35 💬 2 📌 0
Scattered Spider Upgraded Their Tactics to Abuse Legitimate Tools to Evade Detection and Maintain Persistence
05.07.2025 11:36 — 👍 1 🔁 1 💬 0 📌 0
A digital drawing featuring a page full of abstract shapes and stylised flowers and leaves, in vibrant colours.
flower time!!
#art #illustration

Jeff Caruso: Inside Cyber Warfare thehackermaker.com/j...
05.07.2025 15:18 — 👍 0 🔁 1 💬 0 📌 0
10 Best Free Malware Analysis Tools To Break Down The Malware Samples – 2025
30.06.2025 11:47 — 👍 3 🔁 1 💬 0 📌 0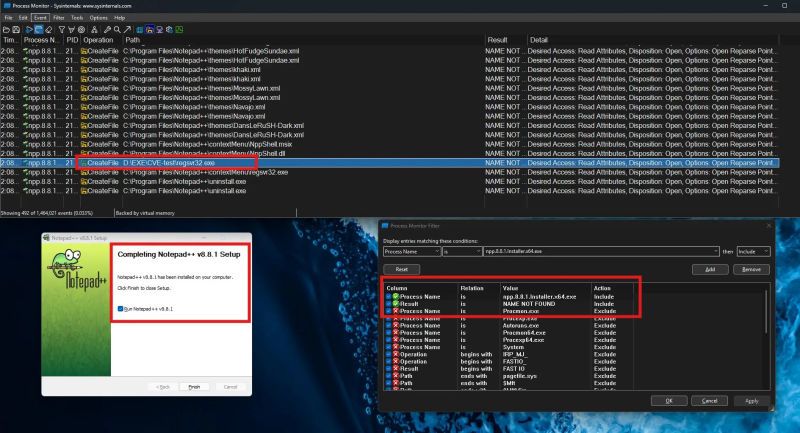
Notepad++ Vulnerability Let Attacker Gains Complete System Control – PoC Released
24.06.2025 02:44 — 👍 5 🔁 2 💬 0 📌 0
Very interesting blog post from a secure code review perspective. I discovered it thanks to @pentesterlab.com
"Unexpected security footguns in Go's parsers"
#go #appsec #appsecurity
blog.trailofbits.com/2025/06/17/u...

NIST Released 19 Zero Trust Architecture Implementations Guide – What’s New
14.06.2025 09:36 — 👍 14 🔁 4 💬 0 📌 0
Hello, friends! I'm thrilled to announce that The Homelab Almanac, v3.0 has officially launched! There is a **ton** of new stuff in this version, including:
- Proper DNS
- PKI
- Automatic signed certificates
- New secrets management
- Proxmox clustering
- Cloud integration

Want to contemplate time, the calendar and its intricacies, try this terrific read. bookshop.org/p/books/the-...
01.05.2025 02:49 — 👍 2 🔁 1 💬 0 📌 0Hasherezade just unveiled another process injection method. There are probably 20 or 30 different process injection methods now, and nerds are still using CreateRemoteThread like it's 2005
14.04.2025 21:57 — 👍 25 🔁 1 💬 0 📌 0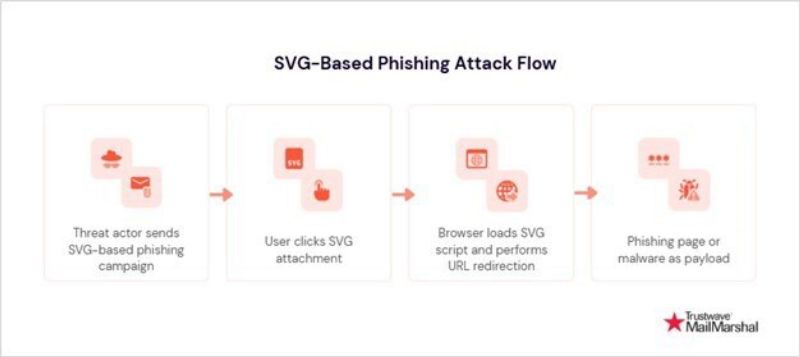
SVG Phishing Surge: How Image Files Are Being Weaponized to Steal Credentials
13.04.2025 04:15 — 👍 1 🔁 3 💬 0 📌 1Mangoes are never overrated... They deserve every single rating and more
13.04.2025 14:06 — 👍 0 🔁 0 💬 0 📌 0
Malware Persistence: How Hackers Stay Alive on Your System (And How to Stop Them)
12.04.2025 11:26 — 👍 1 🔁 2 💬 0 📌 1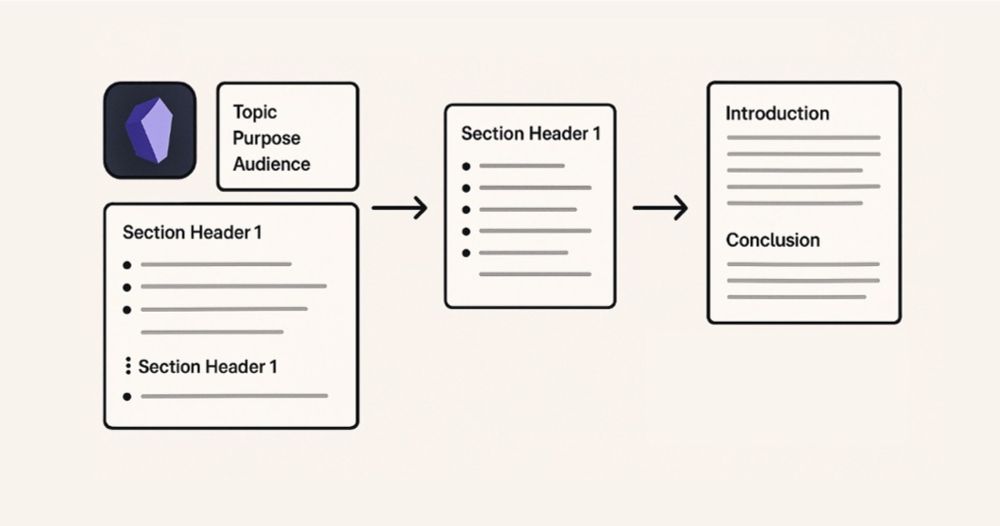
I often get asked: How did I start writing? Why do I write? Who do I write for? What's my process?
I procrastinated on this because, honestly, who cares about my writing process? But after repeatedly answering the same qns, I finally wrote this.
eugeneyan.com/writing/writ...
du -hs *|sort -h
I am typing from memory
du -hs *
01.04.2025 11:10 — 👍 6 🔁 0 💬 1 📌 0
Screenshot of the paper File Systems Unfit as Distributed Storage Backends: Lessons from 10 Years of Ceph Evolution https://dl.acm.org/doi/pdf/10.1145/3341301.3359656
Conventional wisdom says standing on the shoulders of giants—leveraging battle-tested technologies. However, it's worth re-evaluating that decision when prior art becomes a substantial blocker. Sometimes, you need a clean-slate approach. This paper shows a good example: why/how Ceph built BlueStore.
30.03.2025 19:20 — 👍 17 🔁 2 💬 1 📌 0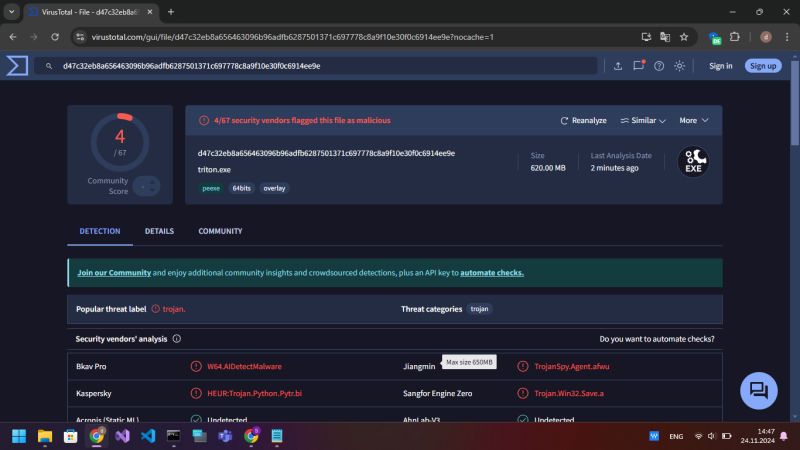
Python-Powered Triton RAT Exfiltrates Data via Telegram and Evades Analysis
31.03.2025 02:20 — 👍 4 🔁 3 💬 0 📌 0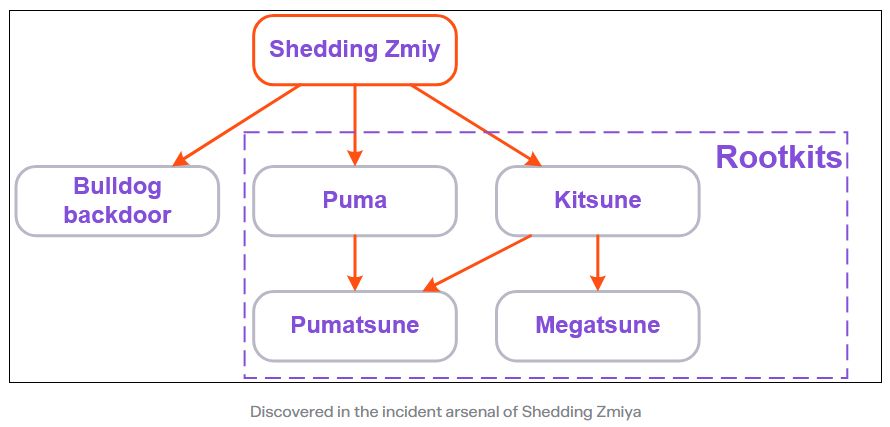
Rostelecom discovered new malware operated by Shedding Zmiy, a pro-Ukrainian espionage group made up of former members of the Cobalt cybercrime group.
The new malware includes four new Linux rootkits (Puma, Pumatsune, Kitsune, and Megatsune) and the Bulldog backdoor.
rt-solar.ru/solar-4rays/...

Zscaler has spotted a new malware loader named CoffeeLoader, used in the wild since September of last year. The malware was used together and appears to bear similarities with SmokeLoader.
www.zscaler.com/blogs/securi...

Metacurity is pleased to offer our free and premium subscribers a weekly digest of the best long-form (and longish) infosec-related pieces we couldn't properly fit into our daily news crush.
www.metacurity.com/best-infosec...
The Firewall Project is now open-source: www.thefirewall.org
Read the announcement here: old.reddit.com/r/cybersecur...
The code is on GitHub: github.com/TheFirewall-...
New Sophisticated Malware CoffeeLoader Bypasses Endpoint Security to Deploy Rhadamanthys Shellcode
27.03.2025 15:24 — 👍 3 🔁 1 💬 0 📌 0
Someone has done an excellent job collecting RATs and documenting them by version. They also included images.
A+ work. This is amazing (we're going to ingest this eventually)
github.com/Cryakl/Ultim...