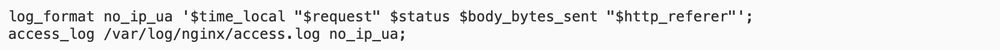Redmine is so much more practical than Jira. Especially for issue tracking and it even allows cascading subtasks. The only major downside I see is the Wiki because editing is not in-place. Also post-configuring the Postgres tables was needed for me (utf8mb4) to allow Emojis in issue texts
09.07.2025 13:26 — 👍 0 🔁 0 💬 0 📌 0
Now that Let's Encrypt stopped their notification mails I just swapped nginx for Caddy which automagically handles certificates
30.06.2025 12:31 — 👍 0 🔁 0 💬 0 📌 0
IMHO the best tool to organize source installations on Linux: GNU Stow (unless using an immutable distribution like NixOS...)
07.05.2025 08:39 — 👍 0 🔁 0 💬 0 📌 0
Running nginx with HTTP/3 is quite adventurous. I appreciate though that (the required) compiling from source allows me to use LibreSSL
07.05.2025 08:29 — 👍 0 🔁 0 💬 0 📌 0
I always create a function Main() (err error) that I call from main. Mostly out of convenience though to be able to just write "return" for error checking
21.04.2025 12:58 — 👍 0 🔁 0 💬 0 📌 0
Vulnerability websites with logos seem to have fully superseded CVE numbers by now
16.04.2025 16:26 — 👍 0 🔁 0 💬 0 📌 0
I don't like the clunkiness of Dependency Injection but every time I'm surprised how test coverage increases almost by itself
28.03.2025 08:37 — 👍 1 🔁 0 💬 0 📌 0
Underrated file system protocol: WebDAV
18.03.2025 07:03 — 👍 0 🔁 0 💬 0 📌 0
Self-hosting E-Mail has come a long way. That's my second attempt now, this time with Mox. A few months aren't really enough data points but at this point it's already more reliable than Protonmail
04.03.2025 14:16 — 👍 0 🔁 0 💬 0 📌 0
To create a systemd user service:
• service definition in /home/username/.config/systemd/user/
• using target default (multi-user won't work on boot)
• loginctl enable-linger username
• systemctl --user enable my.service
(Optionally systemctl --user daemon-reload with XDG_RUNTIME_DIR set)
17.02.2025 17:12 — 👍 2 🔁 0 💬 0 📌 0
I tried the Vault Secrets Operator recently and once the setup is done, it's really practical. Also automated secret rotation is quite something. #kubernetes #vault
11.02.2025 16:28 — 👍 0 🔁 0 💬 0 📌 0
Current versions of WebPageTest are quite practical. Apart from the usual performance insights it also has now carbon control and an accessibility check.
28.01.2025 10:51 — 👍 1 🔁 0 💬 0 📌 0
Google enforcing JS enabled browsers reminds me of a discussion I had 11 years ago on the PhantomJS mailing list asking whether it adheres to robots.txt.
The answer was no, also with the argument that it's not a bot and scriptable like a Browser.
I still find it quite an interesting perspective.
19.01.2025 17:09 — 👍 2 🔁 0 💬 0 📌 0
I'd also add regularly cleaning the nozzle (watch out, it's hot) before problems occur, just with Isopropyl alcohol and a paper towel. There are plenty of guides how to do this though.
14.01.2025 14:30 — 👍 0 🔁 0 💬 0 📌 0
I see, that's not ideal. (I somewhat liked the standardization effort of the Filesystem hierarchy though while it was current but I guess that's only a small bit of it.)
13.01.2025 19:19 — 👍 0 🔁 0 💬 0 📌 0

Linux Standard Base - Wikipedia
I cannot believe the Linux Standard Base has been abandoned. (Paradoxically Linux on the Desktop is as popular as never before.) #linux
13.01.2025 19:07 — 👍 0 🔁 0 💬 1 📌 0
Using runtime.LockOSThread() is a nice trick to prevent unpredictable results when using #cgo or doing syscalls in #golang
08.01.2025 11:22 — 👍 2 🔁 0 💬 0 📌 0
FLIPPYR.AM
How important is Rowhammer in the real world? Seems it'll be a bit more certain next year #38c3 flippyr.am
31.12.2024 13:25 — 👍 2 🔁 0 💬 0 📌 0
Happy holidays!
24.12.2024 09:23 — 👍 1 🔁 0 💬 0 📌 0
![Go example that imports a library with a vulnerable accept header parser function from 2020. It uses the reflect package to call it. Running govulncheck in binary mode results in finding 2 vulnerabilities.
Source code:
```
$ cat main.go
package main
import (
"golang.org/x/text/language" // v0.3.4 (2020)
"reflect"
)
func Main() {
language.ParseAcceptLanguage("00-t-0o")
}
func main() {
reflect.ValueOf(Main).Call([]reflect.Value{})
}
```](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:qazna4xgil7x3nedsqrjd7b7/bafkreich5bzlowxndlqbtebn5bl6riidon726usef4sjg7ykzgo7ddks2e@jpeg)
Go example that imports a library with a vulnerable accept header parser function from 2020. It uses the reflect package to call it. Running govulncheck in binary mode results in finding 2 vulnerabilities.
Source code:
```
$ cat main.go
package main
import (
"golang.org/x/text/language" // v0.3.4 (2020)
"reflect"
)
func Main() {
language.ParseAcceptLanguage("00-t-0o")
}
func main() {
reflect.ValueOf(Main).Call([]reflect.Value{})
}
```
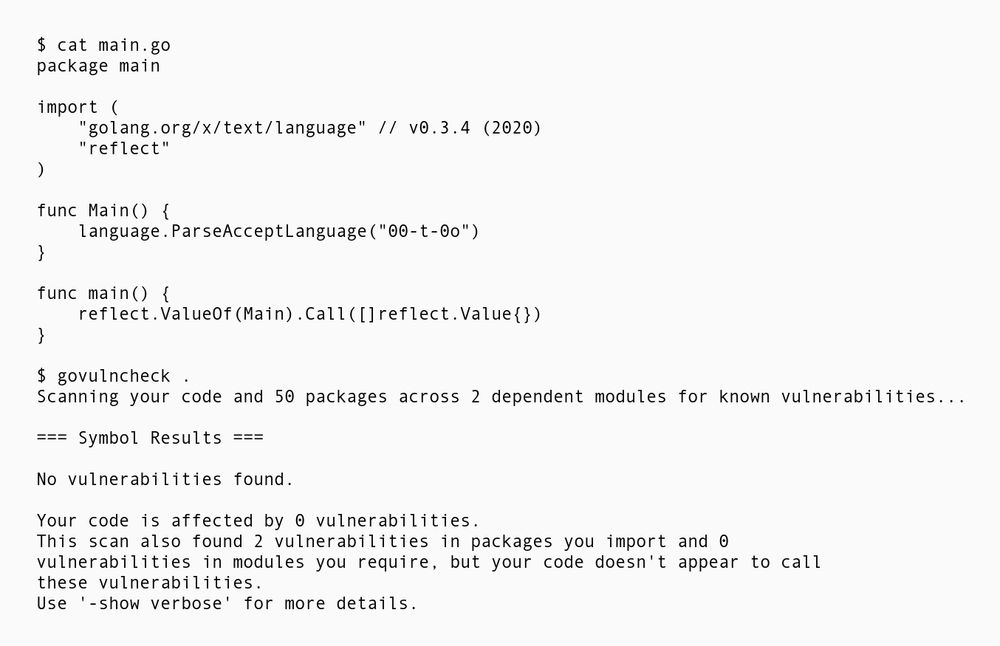
Again the same Go example calling a vulnerable function using reflect. This time govulncheck is called in source mode though, reporting:
No vulnerabilities found.
Your code is affected by 0 vulnerabilities.
This scan also found 2 vulnerabilities in packages you import and 0
vulnerabilities in modules you require, but your code doesn't appear to call these vulnerabilities.
govulncheck also has a binary mode to increase coverage for reflect based call chains #devsecops #golang
18.12.2024 16:26 — 👍 4 🔁 1 💬 0 📌 0
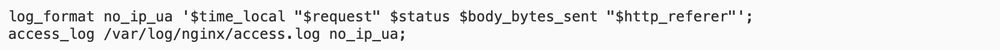
log_format no_ip_ua '$time_local "$request" $status $body_bytes_sent "$http_referer"';
access_log /var/log/nginx/access.log no_ip_ua;
Logging in nginx without IP and User-Agent when feasible
13.12.2024 07:46 — 👍 0 🔁 0 💬 0 📌 0
Keeping dependency count low and sticking to high quality dependencies at the beginning of a project has multiplier effects. Upgrading to recent versions is feasible when done consistently. Thus keeping security in check and preventing package archeology during migrations #devsecops #shiftleft
06.12.2024 10:32 — 👍 2 🔁 0 💬 0 📌 0
Microservices all the way 😀 I'm playing around with Next at the moment but I cannot decide yet. If anything more complex is needed Backend-wise, I rather put that into a separate service though
03.12.2024 19:59 — 👍 2 🔁 0 💬 0 📌 0
My favorite hosters are actually Hetzner and Scaleway. For instance Scaleway feels very round and I'm impressed that they use resource efficient adiabatic cooling in PAR2 which reduces water usage
02.12.2024 09:21 — 👍 6 🔁 0 💬 1 📌 0
Something random like UUID is definitely an advantage security-wise, e.g. to prevent enumeration attacks (definitely need to look into ULID, first time I hear about them)
28.11.2024 17:36 — 👍 2 🔁 0 💬 1 📌 0
I like just telling that "a password reset mail was sent to user@example.com" either way. Not disclosing whether that was actually successful. So legit users still have a reasonable UX and may even realize if they entered the wrong mail
Also it's possible to suggest more help (faq/contact)
26.11.2024 20:58 — 👍 1 🔁 0 💬 0 📌 0
Looking into 2FA for SSH with libpam-google-authenticator on a Debian server. What I notice:
• one factor must be password auth otherwise ineffective (3FA with Key Auth)
• ⚠️ will lock out root by default
• Ansible use tricky
Feels robust so far but planning for lock out scenario seems essential
25.11.2024 14:04 — 👍 2 🔁 0 💬 0 📌 0
Thanks! 🙏
21.11.2024 10:29 — 👍 1 🔁 0 💬 0 📌 0
Hi Andrei, would be awesome to get added as well!
21.11.2024 08:06 — 👍 1 🔁 0 💬 1 📌 0
I help building the .NET runtime at Microsoft. My tweets are my own opinions and/or shitposts, not the official party line.
Your favorite enterprise technology news vultures, flying high in the Bluesky – On the web since 1998 – More here: https://www.theregister.com/
Europe's empowering cloud provider 🚀
freelance full stack dev • tweets fr/en • crafting problem-solving solutions
Engineer, data wrangler, and martian photographer at NASA-JPL, Los Angeles. Curiosity Rover ECAM PUL. Saturn native, commutes to Jupiter. USMC vet. Opinions are mine https://apoapsys.com
Speed up your content with our next-generation CDN, Edge Storage, and Optimization Services. We're making the internet hop faster!
Die #GI setzt sich seit mehr als 50 Jahren für die Förderung der #Informatik in allen Lebensbereichen ein. #WirSindInformatik
Full of passionate intensity.
A brand new handheld video game system from Panic.
➡️ Available at https://play.date
💬 Need help? Go to https://help.play.date
Wir sind ARTE, die europäische Kulturplattform. En français findet ihr uns unter @artefr.bsky.social
Writing about freelancing, tech, and data.
IT Freelancer Starter Pack: https://go.bsky.app/FBCAKAg
Das Netzwerk für IT-Freelancer
A web developer, who loves solving problems
Building
- https://scrapersensei.com (Use AI to automate & scrape in your browser)
- https://bannerify.co (Automate image generation)
- https://correctify.ai (Grammarly alternative)
also made @xbot.an.cyou
I am a pixel artist working with Mugen, IKEMEN, Unity and Openbor coders.
Learn more about our projects.
👇👇👇
https://ko-fi.com/sailorstarsbeyond
Creativity. Tech. Words. ADHD. British-born. Naturalised German. Hyperlexic. Bendy. Adventure gamer. Married. Ally. Vegan. Idealist.
Green web dev. Copywriter. SEO. Translator. Designer. W3C Invited Expert.
Long covid survivor. I mask indoors.
Product @crunchydata previously MSFT/Citus/Heroku. Talk a lot about Postgres and startups. Why Postgres? https://www.crunchydata.com/why-postgres
Graphics/low-level/game programmer.
Made www.principle.app.
Former Apple Engineer.
https://danielchasehooper.com
Media artist based in Berlin, specializing in media scenography, projection mapping, site-specific installations, and generative abstraction
siewerski.com
Bridgy Fed (https://fed.brid.gy/) bot user for the fediverse. To bridge your Bluesky account to the fediverse, follow this account.
To ask a fediverse user to bridge their account, send their address (eg @user@instance) to this account in a chat message.…
 14.07.2025 20:04 — 👍 197 🔁 64 💬 6 📌 24
14.07.2025 20:04 — 👍 197 🔁 64 💬 6 📌 24


![Go example that imports a library with a vulnerable accept header parser function from 2020. It uses the reflect package to call it. Running govulncheck in binary mode results in finding 2 vulnerabilities.
Source code:
```
$ cat main.go
package main
import (
"golang.org/x/text/language" // v0.3.4 (2020)
"reflect"
)
func Main() {
language.ParseAcceptLanguage("00-t-0o")
}
func main() {
reflect.ValueOf(Main).Call([]reflect.Value{})
}
```](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:qazna4xgil7x3nedsqrjd7b7/bafkreich5bzlowxndlqbtebn5bl6riidon726usef4sjg7ykzgo7ddks2e@jpeg)