Breaking Pokémon Go Anti-Cheating System - Part 2
Overcoming Niantic's Anti Cheating Mechanism
Breaking 'Em All!
The blog posts going deeper into hacking Pokemon Go that accompany my #DEFCON talk are live on my blog!
taltechtreks.com/2024/04/06/H...
taltechtreks.com/2025/08/09/H...
Happy to get questions on the research!
09.08.2025 20:19 — 👍 5 🔁 1 💬 0 📌 0

DEFCON_DCTV_Three - Twitch
DEFCON TV Channel 3: Track 3 Talks
Talking in an hour at #DEFCON about Pokemon Go on track 3. Couldn't be more excited!
I've worked on it multiple nights in the past months, and I hope you'll enjoy it!
If you're not here in person, you can catch the talk live at www.youtube.com/live/fzbrrKP...
or www.twitch.tv/defcon_dctv_...
09.08.2025 17:24 — 👍 4 🔁 1 💬 0 📌 0


Giving a talk on Pokemon Go, I just had to convert myself to a Pokemon trainer.
The amazing Ryan Rockenbaugh surprised me with a limited edition sticker of Trainer Tal
Sticker wall at #DEFCON got 2, and I will be giving what's left tomorrow at my talk
Breaking 'Em All! 11:30 Track 3. See you!
09.08.2025 02:53 — 👍 4 🔁 0 💬 0 📌 0

Excited and humbled to speak once again in DEF CON.
Talk is on Saturday at 11:30, track 3.
I'll be in the conf till Sunday, hit me up if you want to chat over the talk or any other project.
07.08.2025 22:24 — 👍 2 🔁 0 💬 0 📌 0

The #DEFCON 33 schedule is live and I'm excited to announce I'll be giving a talk this year on unique research I was a part of a few years back!
"Breakin 'Em All – Overcoming Pokémon Go's Anti-Cheat Mechanism"
Join me on stage - Sat, 11:30 AM, Track 3
defcon.org/html/defcon-...
22.07.2025 15:17 — 👍 1 🔁 1 💬 0 📌 0

Looks like I'll be at Hacker Summer Camp this year!
Exciting #DEFCON33 ☺
11.06.2025 15:19 — 👍 6 🔁 0 💬 0 📌 0
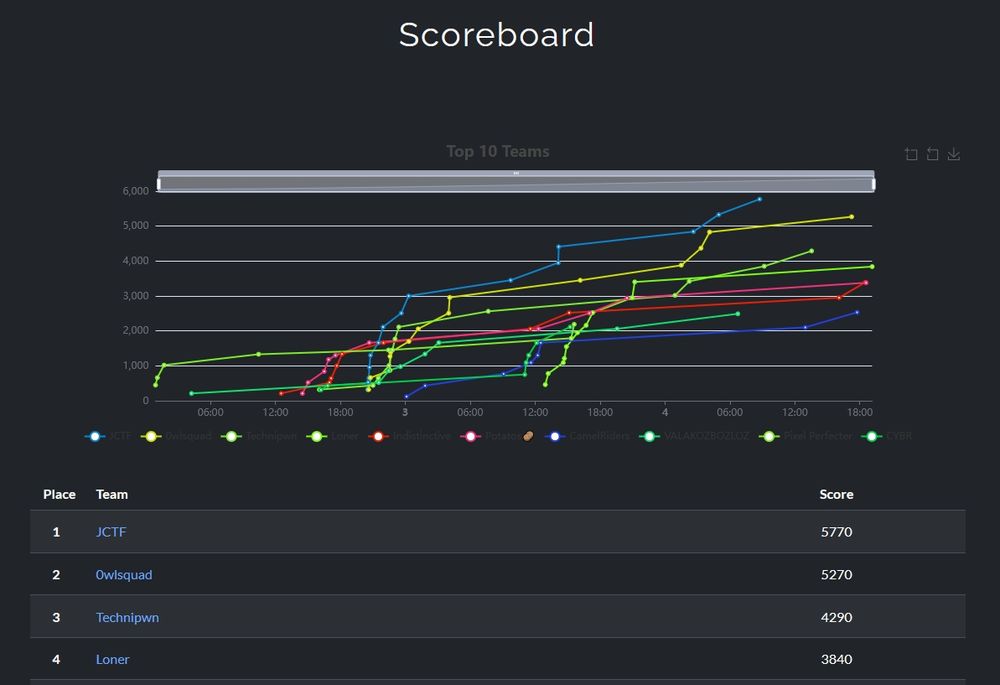
AppSec IL 2025 CTF - Writeup
A writeup on all challenges I solved in the 2025 OWASP CTF
Just got back from #AppSecIL2025!
Ended up 4th place in the #CTF 🎉
Solved 12/15 challenges alone - Android pwn, JS sandbox escapes, cache poisoning, XSS bypasses. The usual suspects: SQLi, LDAP injection, XXE.
Had a blast!
Looking forward to the next one.
Writeup: taltechtreks.com/2025/06/04/a...
06.06.2025 11:48 — 👍 2 🔁 1 💬 0 📌 0
I'm building something cute and new, but as opposed to my normal ways, this time I'm using #Cursor heavily and the flow blows my mind.
Although I'm certain that without prior good knowledge of coding it wouldn't work that well.
20.05.2025 17:38 — 👍 0 🔁 0 💬 0 📌 0

Excited to present my research tomorrow at #RSAC!
Come by to hear John and me share conclusions and insights on the first publicly available report on Non-Human identity security!
See you there,
May 1, 10:50 am at Moscone West 3004!
01.05.2025 01:03 — 👍 3 🔁 0 💬 0 📌 0

The Largest Sofa You Can Move Around a Corner | Quanta Magazine
A new proof reveals the answer to the decades-old “moving sofa” problem. It highlights how even the simplest optimization problems can have counterintuitive answers.
For today, a bit Friends content! Or, uhh, actually, computer science!
What’s the largest sofa you can pivot around a corner?
Heard about this problem in the past, but I thought it's one of those we will never be able to prove. (At least until quantum computers arrive to solve some NP problems)
23.04.2025 08:39 — 👍 1 🔁 0 💬 0 📌 0
Took a bit of hiatus from posting here, was quite busy the past few months (CFP season amiright…)
But I do have more cool stuff ready for sharing as well as writing 2 blog posts about projects I worked on lately.
Looking forward to sharing with you all
17.04.2025 06:57 — 👍 1 🔁 0 💬 0 📌 0

Great time presenting OWASP NHI Top 10 at #SnowFROC!
If you're here, come say hi!
14.03.2025 20:20 — 👍 0 🔁 0 💬 0 📌 0
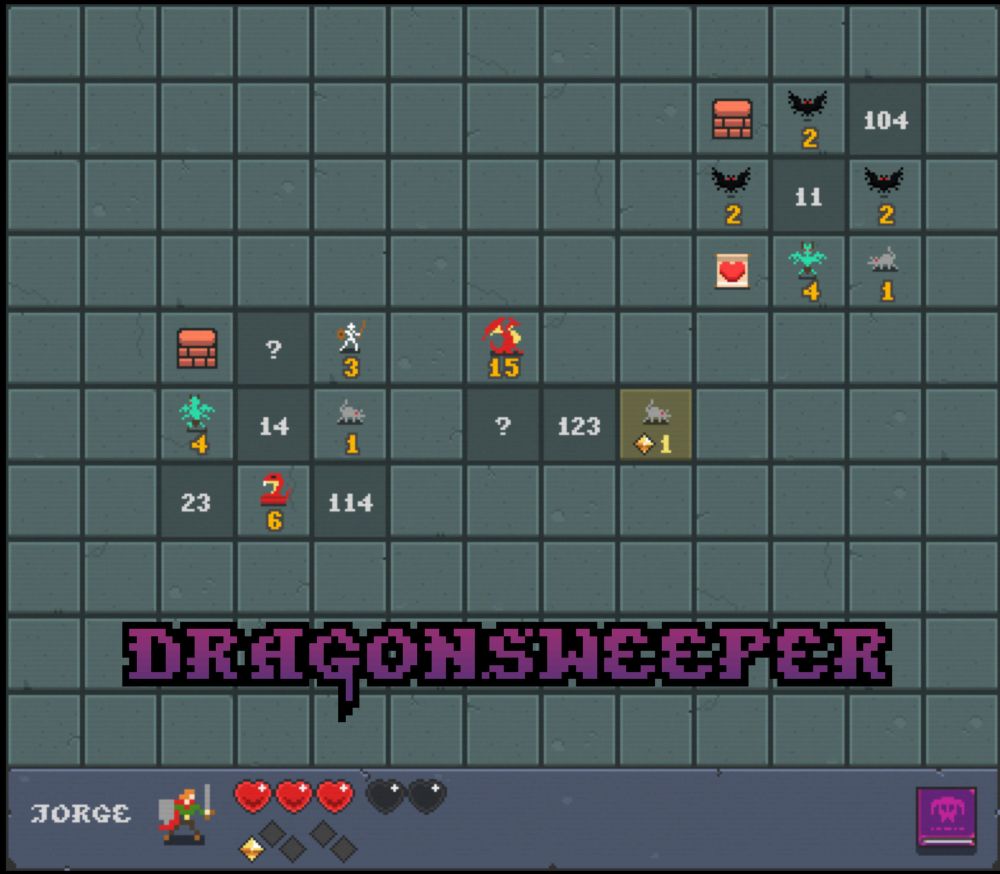
Dragonsweeper by Daniel Benmergui
A roguelike minesweeper adventure
Well, that was an hour of my life well spent.
An amazing adaptation of minesweeper to include old-school RPG elements.
UPDATE: Had to go back and play, another 4 hours to achieve a perfect clear. Incredible game!
08.03.2025 00:03 — 👍 1 🔁 0 💬 0 📌 0
Great thread on the emerging new details on the ByBit breach
06.03.2025 23:59 — 👍 0 🔁 0 💬 0 📌 0
Every HTML Element
A cute post showcasing the basis of every website - HTML! The site goes over (almost) all HTML tags, by using them.
Seeing this, it’s unfortunate that text inputs in websites don't allow most tags but rather encapsulate how the final result is displayed for users. Give us more, please!
28.02.2025 00:31 — 👍 1 🔁 0 💬 0 📌 0
Managed to squeeze in 2 talk submissions to #fwd:cloudsec just before the first round CFP closes.
Hoping for good news, will be the perfect reason to finally attend in person!
27.02.2025 17:39 — 👍 0 🔁 0 💬 0 📌 0
No screen, no controller, and absolutely no sense, just a power button and a USB port.
Brick your Steam Deck - one way or another…
Check out this wild project: #Steam #Brick.
The author transformed the Steam Deck to a brick that still connects to screens or VR while reducing size by a third
Projects like this (author used steam-provided data) are a great example of "right-to-own", critical to enhance electronics sustainability
24.02.2025 21:58 — 👍 1 🔁 0 💬 0 📌 0
Thanks for the shout-out!
Happy to see the starterpack in use 😁
24.02.2025 10:47 — 👍 1 🔁 0 💬 0 📌 0
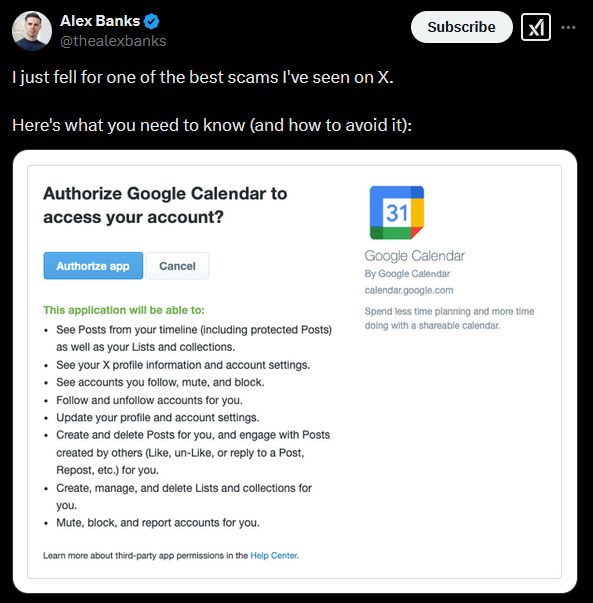
#OAuth #phishing apps are coming to get you - now on #X!
It's annoying to see yet another case of how easy it is to fake consent screens that look identical to real companies.
Why we still lack mandatory verification processes for new OAuth apps is beyond me.
x.com/thealexbanks...
21.02.2025 09:27 — 👍 2 🔁 0 💬 0 📌 0
This researcher found a clever persistence trick: create a rogue #OIDC provider mimicking an existing one, then silently tweak the conditions.
Easy to miss, but it lets an attacker retain access to a compromised account.
How many orgs actually audit their OIDC roles? Feels like a blind spot.
20.02.2025 20:16 — 👍 0 🔁 0 💬 0 📌 0

OAuth Non-Happy Path to ATO
Learn how small errors in OAuth implementation can lead to significant security vulnerabilities like one-click account takeover in web applications
So, #OAuth implementations seem to always have some edge case or quirk making it vulnerable in odd ways.
This particular exploit leveraged an open redirect in an app's OAuth callback, combined with #Google OAuth's quirks to steal authorization codes on visiting a malicious website.
17.02.2025 21:16 — 👍 7 🔁 4 💬 0 📌 0

DeepSeek My User Agent
DeepSeek My User Agent
#DeepSeek roasts me based on my #UserAgent:
Your browser history is so bare even your referrer ghosted you, your 2560x1440 screen is just compensating for how bland Firefox 134 on Windows 10 is, and 16 CPU cores in Tel Aviv? Congrats, you’re the NPC overclocking spreadsheets in the Silicon Wadi.
15.02.2025 14:23 — 👍 2 🔁 1 💬 0 📌 0

Why is Git Autocorrect too fast for Formula One drivers?
Why does Git's autocorrect wait 0.1s before executing a mistyped command? Let's dig in.
Cute bit of #internet history, this post shows why #Git gives you 0.1 seconds to decide if it runs a fixed command.
Turns out, backwards compatibility in code is hard, especially if the code is distributed widely, and can lead to these kind of funny instances (and other that can cause real damage)
14.02.2025 14:04 — 👍 0 🔁 0 💬 0 📌 0
The author created a CPU #JTAG breakout and by inserting it between the balls and the CPU—manages to successfully debug the Xbox and extract the holy grail—a secret 512-byte boot ROM.
This ROM was originally extracted in other methods which allowed #Jailbreaking the #Xbox in the first place.
12.02.2025 21:28 — 👍 0 🔁 0 💬 0 📌 0
Of course, it can't that simple. #Microsoft took a straightforward but effective countermeasure—grounding the #TRST pin, effectively locking out #JTAG access on retail consoles.
Additionally, the #CPU is soldered on a ball-grid-array, making direct patching nearly impossible. But - there’s a way!
12.02.2025 21:28 — 👍 0 🔁 1 💬 1 📌 0

JTAG 'Hacking' the Original Xbox in 2023
Released in November 2001, the original Xbox was Microsoft’s first venture into the game console industry. With its hardware closely resembling a cheap but v...
I love #hacking #embedded systems, and also #gaming when time permits.
Imagine my delight seeing a post that blends both! Two decades after its release, someone revisits the idea of “just” using the original #Xbox CPU's #JTAG connector to debug it.
12.02.2025 21:28 — 👍 4 🔁 0 💬 1 📌 0
PhysicsForums and the Dead Internet Theory
An exposé no one will read, about the widespread falsification of user posts in PhysicsForums, a scientific community founded in 2001. This is a microcosm of the death of the human-written Internet.
The Dead Internet Theory is just a meme, right?
Well…something strange happens over at PhysicsForums. Once an active forum for physics students, now a quieter place.
A year ago, posts appeared, made by users long after their last login. LLM-generated replies back-inserted into the DB
Must read!
09.02.2025 19:45 — 👍 2 🔁 0 💬 0 📌 0
Hey, Erica! :) Glad to have you over here too.
09.02.2025 10:11 — 👍 1 🔁 0 💬 1 📌 0
An independent research lab exploring the future of tools for thought.
We envision a new computer that amplifies human intelligence. A system that helps you think more clearly, collaborate more effectively, and is available anywhere and anytime.
We improve the security of apps with community-led open source projects, 260 local chapters, and tens of thousands of members worldwide. Famous for OWASP Top 10
👀 Tracking all things Valve and Steam.
ℹ️ We are not affiliated with Valve in any way.
🦋 By @xpaw.me 🌐 https://steamdb.info/
Tech lead for workers.cloudflare.com
Also made: capnproto.org, lanparty.house, sandstorm.io
@KentonVarda on Twitter.
Director of Research at @portswigger.net
Also known as albinowax
Portfolio: https://jameskettle.com/
I teach cryptography at Johns Hopkins. https://blog.cryptographyengineering.com
Best-selling author of Alice and Bob Learn Secure Coding & Alice and Bob Learn Application Security. Secure Code Trainer - Nerd @Semgrep #AppSec she/her
https://shehackspurple.ca 🌻
Creator of Darknet Diaries.
Verification: https://twitter.com/JackRhysider/status/1675298532406984707
Loves Jesus, loves others | Husband, father of 4, security solutions architect, love to learn and teach | Microsoft MVP | @TribeOfHackers | 🐘infosec.exchange@nathanmcnulty
Cybersecurity Reporter, Ars Technica: https://arstechnica.com/author/dan-goodin/ Hungry for tips. Text me on Signal: DanArs.82. "The world isn’t run by weapons anymore, or energy, or money. It’s run by little 1s and 0s, little bits of data."
Security editor, TechCrunch
Signal: zackwhittaker.1337
My stories: techcrunch.com/author/zack-whittaker
My weekly cyber newsletter: this.weekinsecurity.com
Cyber guy. Former NSA cybersecurity director and chief of TAO. Lover of memes. Warning - occasional outrageous Christmas light content.
independent writer of citationneeded.news and @web3isgoinggreat.com • tech researcher and cryptocurrency industry critic • software engineer • wikipedian
support my work: citationneeded.news/signup
links: mollywhite.net/linktree
senior researcher at @citizenlab.ca
Award-winning #cybersecurity and #AI keynote speaker, writer, podcaster | Host of @theaifix.show and @smashingsecurity.com podcasts
❤️ #DoctorWho, #Beatles, #Chess
🌐 https://grahamcluley.com
🎙️ https://theaifix.show
🎙️ https://www.smashingsecurity.com
Breaker of software, responder of incidents, IANS Faculty, VP R&D Hunter Strategy, Supreme Allied Commander of ANTIFA.
cyber, dogs, sports, memes. she/her. podcaster. "bluesky's humblest resident nailfluencer 💅" - Jerry
my heart is in the west 🌵🌊
Every day I write about #osint (Open Source Intelligence) tools and techniques. Also little bit about forensics and other cybersecurity related themes
Ageing hacker, long time documentary photographer. Black Hat Review board. Now sitting on numerous government cyber security boards so I guess that means I’ve grown up right?