It's best for everyone if you send us out of the room during movie hacking
03.07.2025 18:46 — 👍 1 🔁 0 💬 0 📌 0Danny Quist
@dannyquist.bsky.social
Reverse engineer. Malware enthusiast.
@dannyquist.bsky.social
Reverse engineer. Malware enthusiast.
It's best for everyone if you send us out of the room during movie hacking
03.07.2025 18:46 — 👍 1 🔁 0 💬 0 📌 0Hacking in movies is awful though
03.07.2025 18:12 — 👍 1 🔁 0 💬 1 📌 0Bob came in at about 20%, he’s now at 93%
26.04.2025 15:22 — 👍 1 🔁 0 💬 0 📌 0
"Every generation re-invents the hash table" something @troutgirl.bsky.social said, two hash-table-inventions ago www.wired.com/story/underg...
17.03.2025 19:42 — 👍 3 🔁 0 💬 1 📌 0Ungarble: Deobfuscation of Go's garbled binaries. Nice work @invokereversing.bsky.social invokere.com/posts/2025/0...
12.03.2025 00:00 — 👍 1 🔁 0 💬 0 📌 0
OpenRakis/Spice86 name checks out ✅ x86 emulation framework ✅ 16-bit only?!?!! It's another game hacking platform github.com/OpenRakis/Sp...
20.02.2025 17:12 — 👍 0 🔁 0 💬 0 📌 0
holy fucking shit
AMD: Microcode Signature Verification Vulnerability
github.com/google/secur...
CactusCon 13 is here in Mesa, Arizona. See you all there.
27.01.2025 17:24 — 👍 1 🔁 0 💬 0 📌 0Two industries that are pretty much the same: Video game copyright protection software and malware ssno.cc/posts/revers...
22.01.2025 15:32 — 👍 1 🔁 0 💬 0 📌 0
He penetrated the top ranks of prominent right-wing militias & devised elaborate ruses to gather evidence of ties to high-ranking law enforcement officials.
He was so successful, he became a militia’s top commander in Utah.
The latest must-read from @josh-kaplan.bsky.social @propublica.org
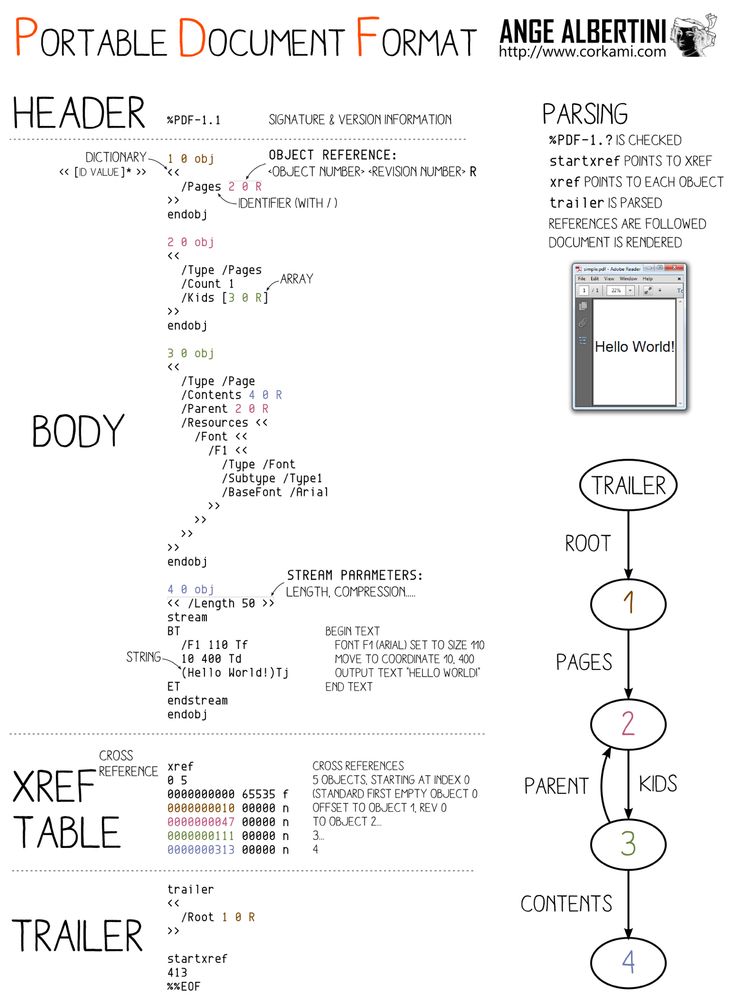
A dissection of a PDF file, showing the signature, objects tree, xref, trailer…
The poster is at github.com/corkami/pics/
04.01.2025 21:02 — 👍 2 🔁 1 💬 0 📌 0I meant it as a complement
31.12.2024 16:40 — 👍 2 🔁 0 💬 1 📌 0
Fearsome File Formats by @angealbertini.bsky.social This is 99% about file formats, and 1% how to present file formats to an audience speakerdeck.com/ange/fearsom...
30.12.2024 16:45 — 👍 2 🔁 1 💬 1 📌 0
Commandments of a good file format: Magic at offset zero. Fast identification, no bypass Up-to-date specs Reflect reality Clear chunk structure forward compatibility, easy parsing/cleanup Samples set Theory isn't enough Version number Forward thinking Extensibility Your format will evolve in unknown ways No duplicity Duplicity -> discrepency (skull emoji) Keep the spirit Don't reuse formats for different intent without trivial distinction No "constant" variables Ossification -> hardcoding Perfect is the enemy of good Shortcuts will be taken to avoid over-complexity
In your forward engineering career if you ever have the chance to design a new file format, please listen to the advice from Ange Albertini's 2024 38C3 talk
30.12.2024 16:30 — 👍 2 🔁 0 💬 0 📌 0Oh! @raspberrypi.com RP2350 gotcha detailed at CCC. Does he win the prize?? events.ccc.de/congress/202...
28.12.2024 18:08 — 👍 4 🔁 1 💬 0 📌 0
The real enemy is token ring. Truer words have never been said Taylor youtu.be/f8PP5IHsL8Y
28.12.2024 03:52 — 👍 2 🔁 0 💬 0 📌 0Cognitive load is what we fight with in reverse engineering too. Obfuscation is cognitive load
Reverse engineers try to find patterns to reduce load
Forward engineers try to reduce complexity
minds.md/zakirullin/c...
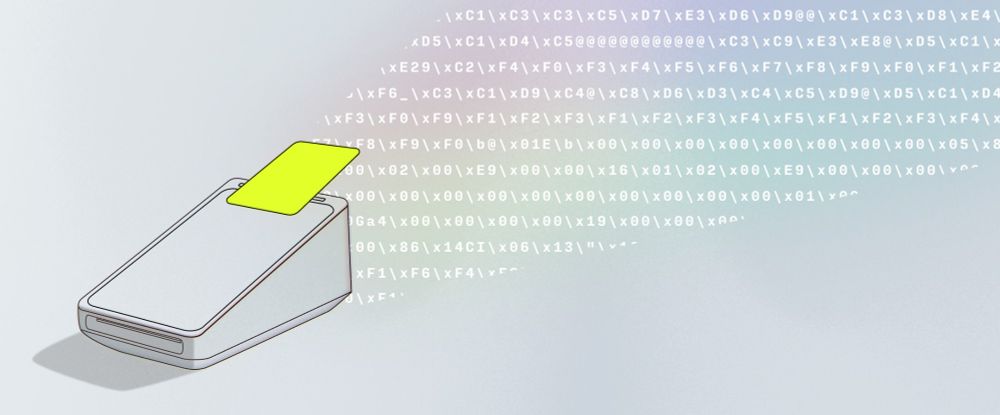
ISO-8583, you old boot. Credit card protocols, how do they work? I love articles that are basically a side-lesson in how to effectively visually communicate a boring protocol increase.com/articles/iso...
19.12.2024 16:30 — 👍 1 🔁 1 💬 0 📌 0 17.12.2024 16:15 — 👍 128 🔁 18 💬 2 📌 1
17.12.2024 16:15 — 👍 128 🔁 18 💬 2 📌 1

Evading EDR by @matterpreter.bsky.social is one of the best books ever published by NoStarch. If you enjoyed the original Rootkits book check this out nostarch.com/evading-edr
17.12.2024 16:22 — 👍 4 🔁 0 💬 1 📌 0Excellence in radio
www.camras.nl/en/blog/2024...
Sean is damn right: C++ structs are tricky. Decompilers universally work better once you fill out structs and types.
02.12.2024 21:58 — 👍 2 🔁 0 💬 0 📌 0
View of a Javelina trail descent, South Mountain, Phoenix Arizona
Trail ratings are good intentions, half truths, and lies
24.11.2024 21:28 — 👍 1 🔁 0 💬 0 📌 0It has been zero days since someone has had the idea to standardize malware names. This has all happened before and it will happen again
24.11.2024 03:27 — 👍 4 🔁 0 💬 0 📌 0Free tendon in every box!
22.11.2024 22:20 — 👍 1 🔁 0 💬 0 📌 0Love love love when people first find packers x.com/mhicroibin/s...
19.11.2024 17:30 — 👍 1 🔁 0 💬 0 📌 0
Sure you can chew the air but the sunsets are nice
17.11.2024 03:31 — 👍 4 🔁 1 💬 0 📌 0
Every problem can be solved with reverse engineering.
26.09.2023 23:59 — 👍 3 🔁 0 💬 0 📌 0