
This One Weird Trick: Multi-Prompt LLM Jailbreaks (Safeguards Hate It!) - SpecterOps
Using multiple prompts within the context of a conversation with an LLM can lead to safeguard bypasses. Learn about safeguards evaluations at scale.
Spoiler alert: Your AI safety measures might have a blind spot. 👀
When attackers use conversation context to bypass LLM safeguards, single-prompt evals just don't cut it anymore.
Dive into @atomicchonk.bsky.social's latest blog on multi-prompt attack detection. ghst.ly/47qJhzn
05.09.2025 16:30 — 👍 5 🔁 1 💬 0 📌 0

Potato exploits have been a cornerstone of local priv esc on Windows for years, but how & why do the inner starchy workings of the potatoes function?
Join @atomicchonk.bsky.social next week to understand Windows access tokens & their use in the Windows environment. ghst.ly/june-web-bsky
20.06.2025 16:55 — 👍 4 🔁 2 💬 0 📌 0
Sorry, Italian four cheese and cheddar jack supreme. My mind was still recovering from the abomination
05.06.2025 02:45 — 👍 1 🔁 0 💬 0 📌 0
Idk if it’s the Cheez It crust itself for me, or if it’s the fact that someone thought a Cheez It crust and an Italian Supreme flavor were a good mix
05.06.2025 02:45 — 👍 1 🔁 0 💬 0 📌 0

Tokenization Confusion - SpecterOps
Meta's Prompt Guard 2 aims to prevent prompt injection. This post looks at how much knowledge of ML we need to be effective at testing these LLM WAFs.
New blog post is up! Stepping out of my comfort zone (be kind), looking at Meta's Prompt Guard 2 model, how to misclassify prompts using the Unigram tokenizer and hopefully demonstrate why we should invest time looking beyond the API at how LLMs function. specterops.io/blog/2025/06...
03.06.2025 16:57 — 👍 5 🔁 1 💬 0 📌 1
You’re a real one, thank you 🙏🏼
29.05.2025 22:30 — 👍 1 🔁 0 💬 1 📌 0

It's potato harvest season! 🥔
Join our upcoming webinar w/ @atomicchonk.bsky.social as he breaks down the starchy workings of potato exploits — from Windows access tokens to technical walkthroughs of Rotten, Juicy, and Rogue potatoes.
Register at ghst.ly/june-web-bsky
29.05.2025 21:20 — 👍 5 🔁 1 💬 0 📌 1
Just wrapped up a blog post on understanding BadSuccesor from a DACL abuse aspect and mitigating it from a DACL abuse perspective.
Also added some PowerShell on my GitHub to create and remove the mitigations.
27.05.2025 21:32 — 👍 14 🔁 2 💬 1 📌 0
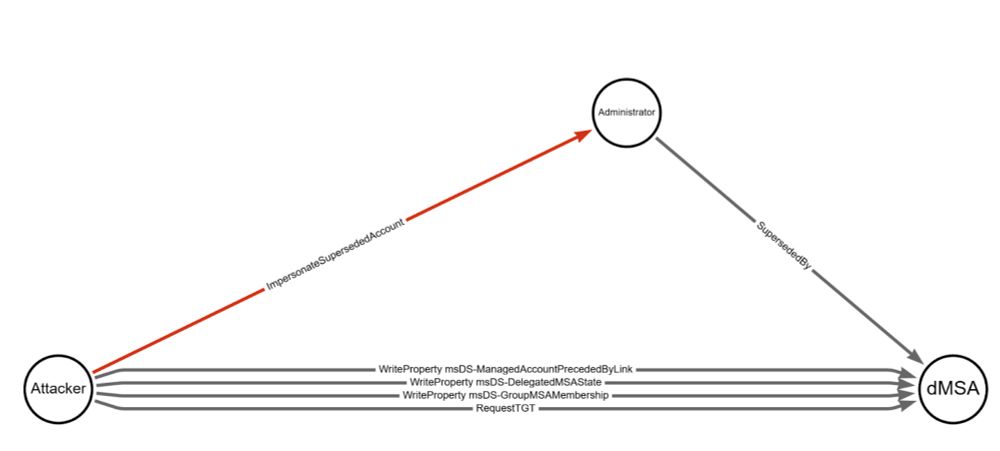
Understanding & Mitigating BadSuccessor - SpecterOps
Understanding the impact of the BadSuccessor AD attack primitive and mitigating the abuse via targeted Deny ACEs on Organizational Units.
BadSuccessor is a new AD attack primitive that abuses dMSAs, allowing an attacker who can modify or create a dMSA to escalate privileges and take over the forest.
Check out @jimsycurity.adminsdholder.com's latest blog post to understand how you can mitigate risk. ghst.ly/4kXTLd9
27.05.2025 21:11 — 👍 16 🔁 9 💬 0 📌 1
If you haven’t read the BadSuccessor blog post, woo boy: www.akamai.com/blog/securit...
24.05.2025 02:40 — 👍 2 🔁 0 💬 0 📌 0
Ok I’ve been enlightened further; they don’t collide if you tweak the command just slightly :pain:
22.05.2025 15:43 — 👍 1 🔁 0 💬 0 📌 0

a rainbow and a star with the words " make you know " on it
ALT: a rainbow and a star with the words " make you know " on it
I’m convinced most learning happens when you’re doing what I call “smacking into something;” failing repeatedly, figuring out why it failed, and proceeding to the next step where you rinse and repeat until you achieve your ultimate objective. TIL: docker and podman dependencies collide.
22.05.2025 15:24 — 👍 1 🔁 0 💬 1 📌 0
Congratulations!
21.05.2025 23:02 — 👍 1 🔁 0 💬 0 📌 0

Black Hat USA 2025
Beyond hyped to be presenting with @anam0x.bsky.social and the rest of my team at Arsenal at BHUSA 2025! app.ingo.me/q/0x9xn
20.05.2025 16:14 — 👍 6 🔁 0 💬 0 📌 0

It was an absolute pleasure to speak at @cackalackycon.bsky.social today and share my love of potatoes. Thank you to @specterops.io for fueling me to always go a layer deeper in learning and motivating me to chase my passions 🥔
18.05.2025 17:10 — 👍 7 🔁 2 💬 1 📌 0
What do potatoes have to do with privilege escalation on Windows? Come find out at Max Andreacchi’s session, “Tater Tokens: Introduction to Windows Access Tokens and Their Role in PrivEsc” on May 18th!
17.05.2025 21:55 — 👍 2 🔁 1 💬 0 📌 0

Why do potato exploits work & how can we stop them?
Join @atomicchonk.bsky.social at @cackalackycon.bsky.social this weekend for a walkthrough of Windows access token manipulation and get the answer. ghst.ly/4jzjlnI
12.05.2025 21:28 — 👍 5 🔁 2 💬 0 📌 0
Immaculate Rick Roll placement
11.05.2025 23:10 — 👍 2 🔁 0 💬 1 📌 0
Great work getting it done!
06.05.2025 21:13 — 👍 1 🔁 0 💬 0 📌 0

Always enjoy the views in Seattle! Spent excellent quality time with teammates and received amazing training. Now for a weekend of running and resting back home before new travels next week ✈️
02.05.2025 23:18 — 👍 1 🔁 0 💬 0 📌 0

Don't let threat actors mash your Windows security! @atomicchonk.bsky.social’s @cackalackycon.bsky.social talk breaks down potato exploits from token mechanics to defensive implementations.
Learn more ➡️ ghst.ly/4jzjlnI
28.04.2025 16:00 — 👍 4 🔁 2 💬 0 📌 0
Fulltime Win Graphic: NC Courage 3-2 KC Current.
NC BABYYY 💙
27.04.2025 01:07 — 👍 68 🔁 16 💬 1 📌 10

I’ve had to beat stubbornness out of my training. When I ran 10+ yrs ago I’d just hard-head my way forward but wind up injured. This time I’m focused on the goals ahead; nagging aches mean a rest day tomorrow so I can live to run later this week and keep this train moving to Oct (and beyond)
24.04.2025 05:22 — 👍 3 🔁 0 💬 0 📌 0

Understanding Windows access tokens could be your best defense. At @cackalackycon.bsky.social, @atomicchonk.bsky.social will be peeling back the layers on potato exploits that threat actors use for privilege escalation.
Check out the schedule to learn more ➡️ ghst.ly/4jzjlnI
18.04.2025 16:33 — 👍 6 🔁 3 💬 0 📌 0
Just pushed a new versions for #AADInternals and AADInternals-Endpoint modules! Some bug fixes plus support for:
1️⃣ Microsoft Authentication Library (MSAL)
2️⃣ Token Protection
3️⃣ Continuous Access Evaluation (CAE)
18.04.2025 12:10 — 👍 16 🔁 5 💬 1 📌 0

DPRK IT Workers in Open Source and Freelance Platforms
A cluster of actors discovered in onlyDust.com freelancer platform and beyond
The Ketman Project has published a list of names and GitHub profiles they believe may be North Korean rogue IT workers posing as open-source developers and freelancers, and seeking employment at Western software companies
www.ketman.org/dprk-it-work...
17.04.2025 13:27 — 👍 8 🔁 6 💬 0 📌 0
Initial stab at using Chris Hayuk's mcp-cli tool to pair roadrecon_mcp_server with a locally-hosted model (in this case, mistral-small3.1). Note that running this query took over 300s so YMMV depending on several factors. Will update GH this week with instructions on replicating this.
16.04.2025 01:53 — 👍 2 🔁 0 💬 0 📌 0
We're the Electronic Frontier Foundation. We're a nonprofit that fights for your privacy and free speech online. Find all of EFF's social media accounts at eff.org/social.
// Somehow a CTO
// JHU SAIS @alperovitch.institute adjunct
// @istorg.bsky.social adjunct sr tech advisor
// Former USCYBERCOM/CNMF
// Retired US Marine Corps
// Personal views and invective
A pop-up, virtual hacker / #infosec con. PancakesCon 6 is September 21, 2025. details on past and future events are on our website, https://www.pancakescon.com
Our online store:
https://ko-fi.com/builtbybittle
Singer, Actress and Philanthropist.
www.lyndacarter.com
NPC Bodybuilder
SW-7503-0119-6711
PSN: TigerPanda69
IG: toniotoni831
busy writing sketches about problems I can’t solve
Films, painting and photography
Yeah I did all that
Thief of Joy: A Comedy Special NOW ON YOUTUBE
Host of The Downside Podcast
If I have to post on another one of these things I’m gonna kms
Philadelphian in Cascadia. Vociferous champion for Oxford commas, two spaces after a period, and ellipses. I break into buildings. 🔓
"Even if the world were ending tomorrow, I would still plant a tree." 🌲
(he/they)
The largest collection of malware source code, samples, and papers on the internet.
Password: infected
(unofficial, this is a bot! Maintained by @yjb.bsky.social, the bot can't handle retweets, video, and maybe a few other things)
freelance illustrator, digital and traditional media
#art | #sketch | #commissions
open for commissions! more info on my website.
scherville.com | scherville.art@gmail.com
The Trans Handy Ma'am
https://linktr.ee/MercuryStardust
Skytalks is a ‘sub-conference’ that gives a unique platform for researchers to share their research, for angry hackers to rant about the issues of their industry, and for curious souls to probe interesting issues, all off-the-record https://skytalks.info/
Certified Run Coach, Elite Personal Trainer, Strength & Conditioning Specialist, Nutrition Coach, and Travel Advisor.
Links/Discounts: https://MikeGiven.com
Run Coaching: https://RunCoachMike.com
Travel Advising: https://CruisePlanTravel.com
Doing stuff in #cybersec i suppose ... #CTF 1dl3 for mushd00m
IT geek | Cybersec professional | Human first
Pansexual polyamorous lover, not fighter (usually). I am me. Deal with it. (I may also be a unicorn🦄)
🏳️⚧️ally, I stand with 🇵🇸
Wife to @Kimmy.zip
Partner to @deviantollam.bsky.social
Girlfriend to @justwes.info
https://linktr.ee/InclusiveLittleUnicorn
Long time dumpster fire connoisseur.
Minnesota Stan.
MN and IN CCDC Red Team Lead.
Associate AdSim Consultant at SpecterOps.
Opinions are my own, not of any other entity.















