
#NoKings in Munich, Germany.
14.06.2025 19:51 — 👍 1 🔁 0 💬 0 📌 0@uchi-mata.bsky.social
Infosec Enthusiast & Practitioner. Opinions are my own. Pentest→Research→Leading→Security Engineering. Love Martial Arts, Outdoors, Dogs. infosec.exchange/@uchi_mata www.rational-security.io

#NoKings in Munich, Germany.
14.06.2025 19:51 — 👍 1 🔁 0 💬 0 📌 0Regarding U2F: It is a small detail, but I learned to love the pattern of requiring additional verification for truly sensitive actions. Drastically reduces admin ATO impact.
04.06.2025 13:01 — 👍 0 🔁 0 💬 1 📌 0Not from the US, but is that this “why did the chicken cross the road” thing?
29.05.2025 06:19 — 👍 0 🔁 0 💬 0 📌 0
Well well well...
It's all starting to make sense now!
#TACO started by @megancnbc.bsky.social - and she has way too few followers for that, let’s change that.
29.05.2025 06:12 — 👍 0 🔁 0 💬 0 📌 0TACO.
29.05.2025 02:20 — 👍 11952 🔁 1468 💬 472 📌 93
If you read the post about O3 finding a SMB bug in the Linux Kernel, I did a few tests and I what I suspected looks true: Gemini 2.5 PRO can more easily identify the vulnerability. My success rate is so high that running the following prompt a few times is enough: gist.github.com/antirez/8b76...
25.05.2025 10:06 — 👍 33 🔁 6 💬 3 📌 0It’s funny that you can go through 20 years of schooling without ever seeing the idea that writing is a tool for thinking.
20.05.2025 14:31 — 👍 64 🔁 9 💬 8 📌 1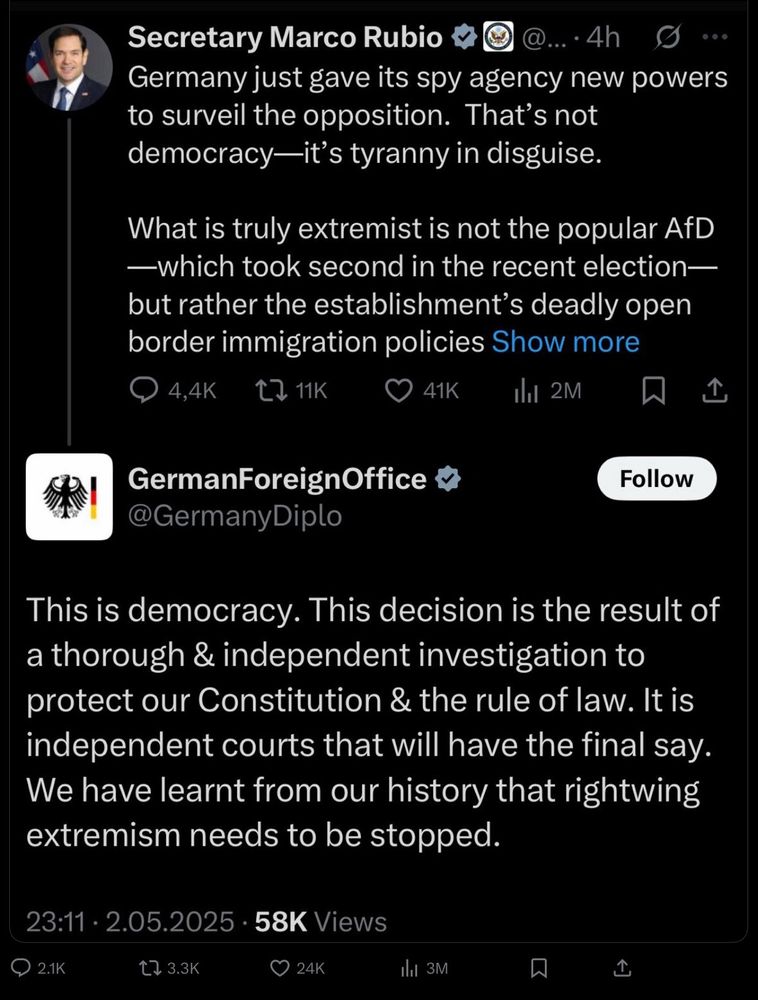
YES!
03.05.2025 02:37 — 👍 468 🔁 95 💬 28 📌 7 30.04.2025 12:14 — 👍 2 🔁 1 💬 0 📌 0
30.04.2025 12:14 — 👍 2 🔁 1 💬 0 📌 0
Most companies are getting AI implementation wrong.
They’re focused on using it to *replace* humans rather than *enhance* humans.
The ones that recognize this now will gain a massive lead in this race.
I wrote up some more information on the differences between adding SYS_ADMIN and CAP_SYS_ADMIN to pods in Kubernetes. It highlights some new things I learned about how the CRI you use can affect how pods are run. raesene.github.io/blog/2025/04...
23.04.2025 10:43 — 👍 5 🔁 2 💬 0 📌 0
Trustworthy and Responsible AI....it's a real thing!
www.youtube.com/watch?v=fhcY...

I didn't even think about this yet, but linting file- and directory names in project structures makes a lot of sense - and there is of course a tool for it:
ls-lint.org
Alright AKS, pick a lane:
Kubenet: Pods receive IP from an overlay network. Retires March 2028
Azure CNI Standard: Pods receive IP from VNET
Azure CNI Overlay: Pods receive IP from an overlay network.
Great article on using GitHub as a workflow platform:
github.blog/engineering/...
Can absolutely recommend for security workflows and management as well!
Quick note on exploits trying to use `nginx.ingress.kubernetes.io/server-snippet`: That annotation has been identified as an issue before and has been disabled to mitigate CVE-2021-25742.
31.03.2025 08:40 — 👍 0 🔁 0 💬 0 📌 0
Quite some #IngressNightmare #CVE-2025-1974 PoCs on GitHub now that look good at a cursory review:
github.com/hakaioffsec/...
github.com/yoshino-s/CV...
github.com/Esonhugh/ing...
github.com/hi-unc1e/CVE...
github.com/lufeirider/I...
github.com/zwxxb/CVE-20...
github.com/rjhaikal/POC...
 30.03.2025 02:25 — 👍 185 🔁 24 💬 3 📌 1
30.03.2025 02:25 — 👍 185 🔁 24 💬 3 📌 1

I wrote up some details on exploiting #IngressNightmare #CVE-2025-1974:
www.averlon.ai/blog/kuberne...
Where are we at with releasing a full PoC?

Great #IngressNightmare CVE-2025-1974 write-up:
securitylabs.datadoghq.com/articles/ing...
Key point missing from many other sources: Exploitation from Internet is non-default and unlikely, but privilege escalation within cluster is by default possible.

Last week we launched a free webapp that shows the tens of thousands of UK companies whose ownership is being hidden, in most cases unlawfully.
It's now easier to use, faster, and has way more features. Quick thread.
TIL that because the FFmpeg project has gained so much experience in hand-writing assembly code to provide huge speedups, they now are putting together a series of lessons for learning assembly:
Vibe coding is fun and all, but this is probably a better use of time!
github.com/FFmpeg/asm-l...

Wow, GitHub not supporting IPv6 for Webhooks:
docs.github.com/en/webhooks/...
In an effort to bring here what little of value is still on the birdsite, allow me to present some absolutely bonkers corporate espionage, in which Deel's execs had a spy at rival Rippling. The complaint is a gripping must-read! rippling2.imgix.net/Complaint.pdf
17.03.2025 19:19 — 👍 33 🔁 4 💬 4 📌 1
I updated my #Kubernetes resource exhaustion testing tool to include inode exhaustion:
github.com/uchi-mata/do...
 26.02.2025 02:19 — 👍 277 🔁 41 💬 10 📌 2
26.02.2025 02:19 — 👍 277 🔁 41 💬 10 📌 2
Trump vs Gov of Maine.
Watch this
German elections on Sunday as well, we might well join you in that sentiment 😅
20.02.2025 16:03 — 👍 2 🔁 0 💬 0 📌 0