
personal achievement: [h-index 5 unlocked]
13.05.2025 07:04 — 👍 6 🔁 0 💬 0 📌 0
personal achievement: [h-index 5 unlocked]
13.05.2025 07:04 — 👍 6 🔁 0 💬 0 📌 0📢 Excited to announce that the results on BaseBridge, our project on improving cellular baseband emulation, are going public this week. Dyon will present at IEEE S&P on Monday 3pm, while David and I will be on stage at @offensivecon.bsky.social on Saturday 11am with even more details! 1/6
11.05.2025 10:23 — 👍 14 🔁 7 💬 1 📌 1
design inspired by the great usgraphics website and font is of course the one and only Berkeley Mono.
to search for and fetch recent papers I use AI2's semantic scholar and ExaAILabs` APIs.

recently, the google scholar feed I used to explore new work in my fields of interest was removed.
so I built my own paper discovery website:
a minimalistic design with high information density and full control over search terms.

okay deepwiki is pretty sweet.
just replace 'github' with 'deepwiki' in a repo's url and it will generate an architecture overview, explanations for components, flow diagrams etc.
I tried it on large code bases like afl++ and libafl and it's actually impressive
new CCS workshop on decompilation, reversing, root cause analysis, debugging, etc. 👀
28.04.2025 09:35 — 👍 3 🔁 0 💬 0 📌 0
the paper by Michael Chesser et al. is a good read in any case:
arxiv.org/pdf/2301.13346
Sogen Windows emulator: github.com/momo5502/sogen
icicle's main selling points are its support for a diverse set of architectures by emulating p-code and architecture-agnostic fuzzing instrumentation. I guess multi-arch support is not really needed for this project but its fuzzing focus might come in handy.
23.04.2025 19:16 — 👍 2 🔁 0 💬 1 📌 0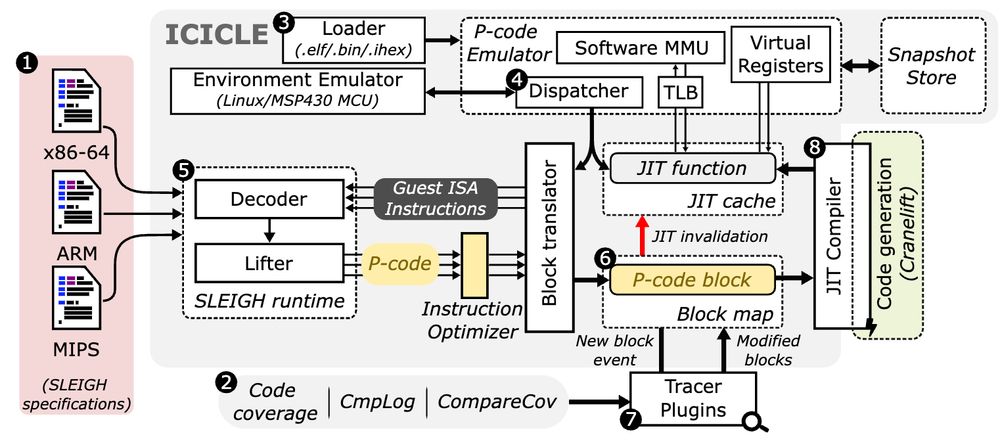
the guy who reversed the denuvo drm
@momo5502.bsky.social works on a high-perf windows emulator for security research.
I noticed that it supports icicle as a backend, a fuzzing-specific emulator. awesome to see academic work being continuously developed and making it into the real world
I thought USENIX was huge with like 300 accepted papers and 6 speaker tracks in parallel.
but man these ml conferences look kinda dystopian
the recording of my talk "Rethinking Emulation for Fu(zzi)n(g) and Profit: Near-Native Rehosting for Embedded ARM Firmware" is online!
I had an absolute blast speaking and being at
@re-verse.io, so many great talks and hallway discussions
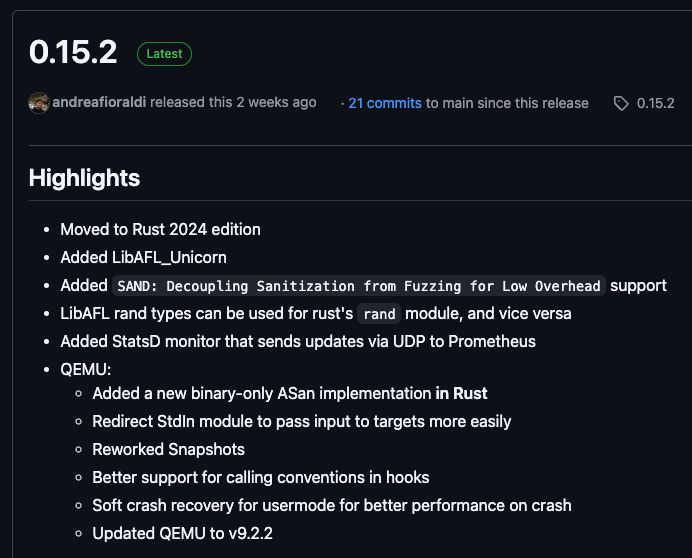
more exciting stuff coming to libAFL @aflplusplus.bsky.social , including a binary-only ASan implementation in Rust for QEMU and integration with the unicorn emulator!
reminds me of how @dmnk.bsky.social and I got the unicornafl rust bindings up and running to fuzz some basebands 5 years ago
some convenient features coming to binja, incl. auto-classification of embedded devices based on peripheral accesses
making firmware hacking maybe a little less painful
cc @stacksmashing.bsky.social
yea it's annoying.
the feed was never great to begin with imho, and then it keeps breaking.
i think it's what I dislike about bluesky the most, that discovery of people / stuff you don't directly follow is pretty hard

3.7 is both in api and in cursor just utterly disappointing.
when it does what it's supposed to, it's great, but man is it trying hard to misinterpret my intentions.
beautiful and incredibly interesting talk on reverse engineering the OG xbox by
@ret2systems.bsky.social's Markus, incl. building a custom interposer to upgrade the CPU
a deep dive into hardware hacking, an ode to hw engineering and a call for software-focused researchers to try new things
libAFL is a beast.
it has so many settings to tweak, different modes to select and the code can be quite scary at first.
but writing a target-specific custom fuzzer is super powerful!
to get started, Trail of Bits just published a nice primer:
appsec.guide/docs/fuzzing...
my google scholar's 'recommended articles' feed has been empty for weeks.
where is, it I miss it :/
anyone any recommendation for an alternative? some tunable feed of recent papers?
please do it :D
11.03.2025 11:49 — 👍 1 🔁 0 💬 1 📌 0
thank you so much Vector35, @psifertex.bsky.social et al. for a great conference!
also thanks to Binarly, it's always great to hang out with the team!
slides: t.co/gB0YWQYy9G
github: github.com/pr0me/SAFIRE...

I had a blast speaking and being at the RE//verse conference!
so many cool people and great discussions on firmware, fuzzing, ai and binary analysis
if you want to find out more about firmware rehosting or are an enjoyer of ascii diagrams, check out the slides to my talk below :)

today was blessed.
had a super fun day at Kennedy Space Center.
and then I got to witness my first rocket launch in person, a falcon 9 bringing Intuitive Machine's lunar lander into orbit.
my space-nerd heart is so happy.
excellent blog post on garbage collectors: "Memory Hell"
it addresses many of humanity's great questions:
- do we actually know how to do garbage collection?
- pointers, indices or handlers?
- and what are typesafe use-after-frees?

2024 was a significant year for decompilation, constituting a possible resurgence in the field. Major talks, the thirty-year anniversary of research, movements in AI, and an all-time high for top publications in decompilation.
Join me for a retrospective:
mahaloz.re/dec-progr...

Rehost embedded ARM firmware at near-native speeds! Lukas Seidel @pr0me.bsky.social introduces SAFIREFUZZ, achieving 690x fuzzing throughput with ARM Cortex-M firmware. Dive into instruction rewriting, emulation, and performance gains. https://re-verse.sessionize.com/session/784004 #REverse2025
28.01.2025 19:34 — 👍 4 🔁 2 💬 0 📌 1
nice work :)
btw are you intentionally (completely) gone from birdsite?

www.mdpi.com/1999-5903/17... by Zhou et al.
17.01.2025 16:52 — 👍 3 🔁 1 💬 0 📌 0
"IoT Firmware Emulation and Its Security Application in Fuzzing" is a great read to get started with rehosting firmware
it provides a taxonomy of nearly all the available approaches and discusses the most important concepts, such as peripheral modeling and fidelity trade-offs
Hooked on computer security, adversarial learning, or even both? 🤩
The BIFOLD Graduate School has 10 open PhD positions!
Join us in vibrant Berlin to work with top-notch researchers on machine learning, data management, and, of course, security!
🔗 mlsec.org/jobs.html#jobs