
The Tianfu Cup is back this year. See the analysis of the event by Eugenio @euben.bsky.social published today on Natto Thoughts.
www.nattothoughts.com/p/the-tianfu...

The Tianfu Cup is back this year. See the analysis of the event by Eugenio @euben.bsky.social published today on Natto Thoughts.
www.nattothoughts.com/p/the-tianfu...

We continue exploring provincial level’s involvement in cyber operations. See details in analysis by @euben.bsky.social
www.nattothoughts.com/p/provincial...

Intense competition, rapid innovation, and strong state involvement define the overall trends in China’s cybersecurity industry for 2025. See our latest analysis
nattothoughts.substack.com/p/chinas-202...

In this post, @euben.bsky.social and the Natto Team assess that provincial bureaus of the Chinese Ministry of State Security likely operate with their own tasking priorities, resources, and local ecosystems for cyber operations.
nattothoughts.substack.com/p/the-many-a...

Researcher @sick.codes found a vulnerability in TCL TVs and reached out to TCL. What happened next?
New analysis from Natto Thoughts - how a single disclosure reshaped China’s approach to cybersecurity and control.
nattothoughts.substack.com/p/what-a-nar...

The Natto Team explores how APT27, HAFNIUM, and Silk Typhoon highlight the complexities of tracking threat actors and their real-world identities and why understanding the humans behind the keyboard matters.
nattothoughts.substack.com/p/beyond-the...

Our latest analysis digs into newly identified Salt Typhoon-linked companies, revealing the murky ecosystem of front firms and legitimate businesses that prop up Chinese state cyber operations.
A beacon of clarity? Or just more questions in the storm?
nattothoughts.substack.com/p/salt-typho...

@euben.bsky.social Eugenio’s research explains the elite cyber talent paradox in China - “all people are soldiers” vs “extremely lean.”
#Cybersecurity #TalentPipeline #CyberOperations
nattothoughts.substack.com/p/few-and-fa...

Microsoft is probing whether a MAPP leak let Chinese hackers exploit a SharePoint vuln pre-patch.
In this new piece for Natto,
@dakotaindc.bsky.social, @meidanowski.bsky.social & I dig into:
🏛️ China's vuln reporting rules
📉 Which firms joined/left MAPP since 2018
⚠️ The risks today’s members pose
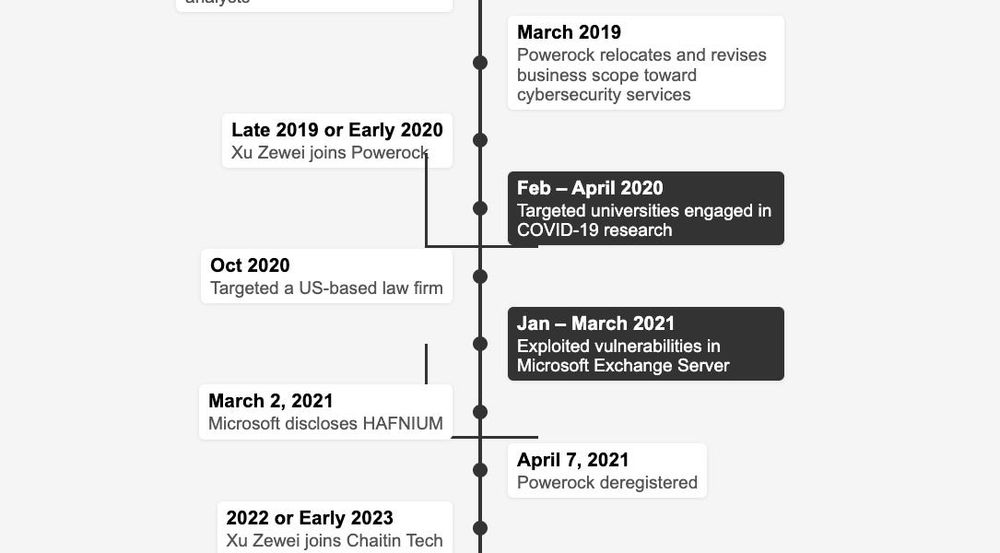
Natto Thoughts examines HAFNIUM-linked hacker Xu Zewei and reveals ties between China’s state security agencies, cybersecurity firm and strategic industries.
nattothoughts.substack.com/p/hafnium-li...

What does China’s top vulnerability mining platform’s white hat elite growth system like? What are the capabilities needed to be an expert white hat hacker?
nattothoughts.substack.com/p/butian-vul...

To defend, one must first know how to attack” (未知攻,焉知防). This mindset, popularized by a Taiwanese hacker Lin in the 1990s, spread from China's red hackers to CTF teams. Today, it powers China's cyber industry.
New piece for @nattothoughts.bsky.social
nattothoughts.substack.com/p/defense-th...

The Natto Team explores the development of China's vulnerability research and discovery skills, starting from the vocational college level.
Thanks to @euben.bsky.social @dakotaindc.bsky.social Kristin Del Rosso for their previous research on the topic
nattothoughts.substack.com/p/when-a-voc...

The Natto Team continues finding stories of Chinese hackers fascinating as they reveal the motivations behind cyber operations and the evolution of China's information security industry.
nattothoughts.substack.com/p/stories-of...
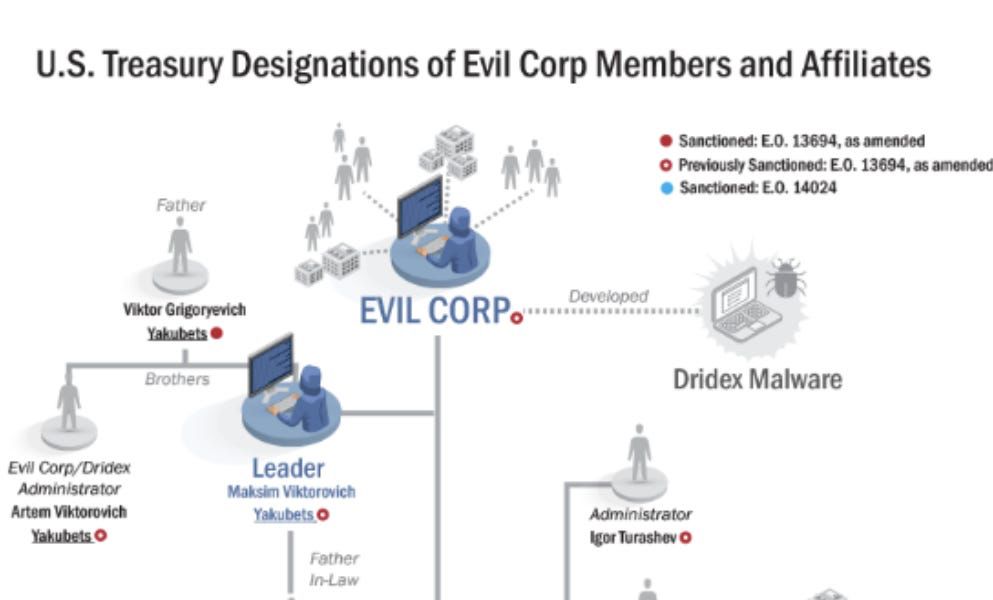
This Natto Thoughts analysis was originally published last October. With new notes and updates added, we thought it is still relevant today to understand Russian ransomware actors and Russian political culture.
nattothoughts.substack.com/p/ransom-war...

In this piece with @nattothoughts.bsky.social's @meidanowski.bsky.social, we dug into China’s two naming-and-shaming campaigns over the past 30 days—targeting alleged Taiwanese and U.S. hackers amid escalating geopolitical tensions.
nattothoughts.substack.com/p/wars-witho...
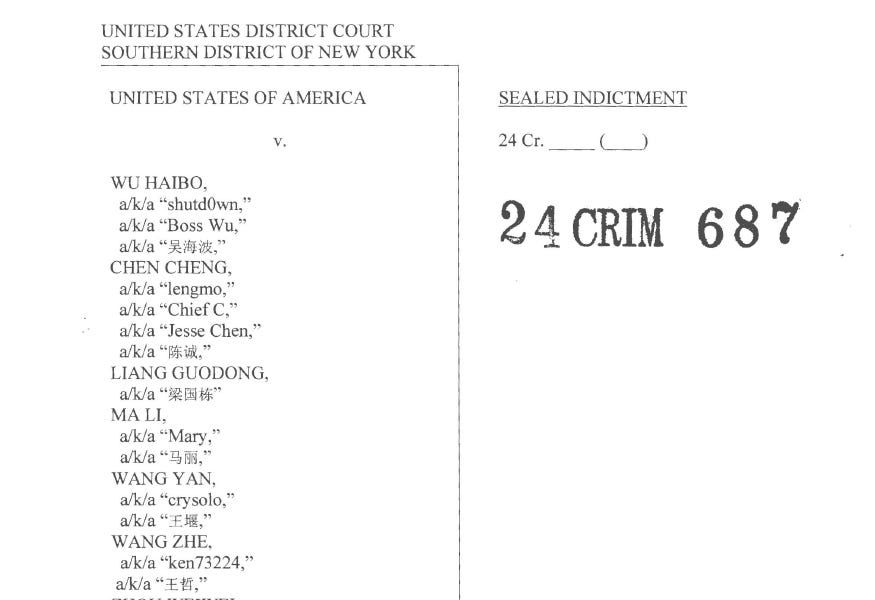
A case study of the i-SOON indictment and leaks reveals that source information may vary but it is important to compare and evaluate information for unique insights.
nattothoughts.substack.com/p/indictment...
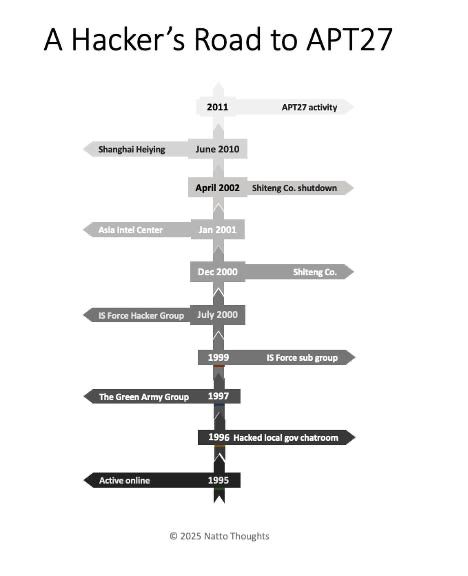
A recent research from Natto Thoughts about US-sanctioned, allegedly APT27-associated actor. #apt27
nattothoughts.substack.com/p/zhou-shuai...

As the Natto Team was going to publish this piece, US Department of Justice unsealed an indictment charging eight i-SOON employees and highlighting the importance of companies like i-SOON in China's cyberthreat landscape.
nattothoughts.substack.com/p/where-is-i...
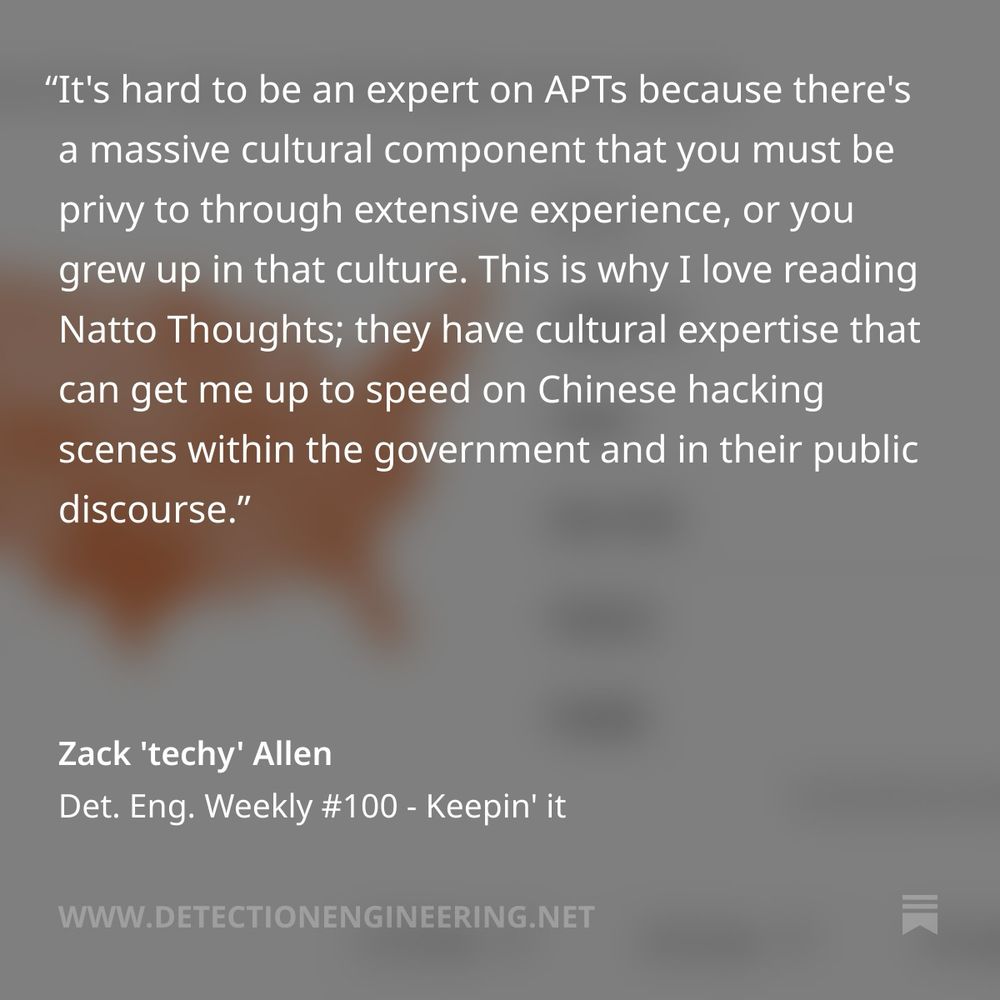
We appreciate that more and more threat intelligence researchers value the importance of cultural component in APT research. @techy.detectionengineering.net
28.02.2025 03:05 — 👍 6 🔁 2 💬 0 📌 0
One year after the I-SOON leaks, we still found more things that were not clear to us before. @euben.bsky.social ‘s Pangu team analysis gives more insights into China’s cyber operations.
nattothoughts.substack.com/p/the-pangu-...

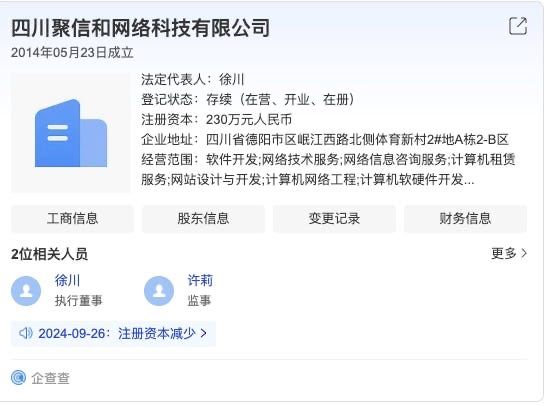
We are glad to see that some curious minds like us want to find out more about Chinese APTs associated companies in reality. They actually paid a visit to them.
substack.com/home/post/p-...

Even before DeepSeek's debut sparked pride among Chinese netizens, US sanctions on Sichuan Silence developer Guan Tianfeng triggered online vows to "march forward" in cyberpower competition.
nattothoughts.substack.com/p/sichuan-si...
The other shoe has finally dropped, but we still need more intrusion details to defend against the threats.
#salttyphoon #apt
nattothoughts.substack.com/p/salt-typho...
No, it doesn’t look like
17.01.2025 20:16 — 👍 1 🔁 0 💬 0 📌 0Can I have some rest on the weekend? 😊
17.01.2025 20:15 — 👍 1 🔁 0 💬 1 📌 0
It is Sichuan not Chengdu
17.01.2025 19:47 — 👍 2 🔁 0 💬 1 📌 1
Kick off 2025 with a spicy hotpot - why has Chengdu become a hub for hacking?
nattothoughts.substack.com/p/chengdu-te...

1000 subscribers. You did it. Natto Thoughts has its first thousand subscribers. Nattothoughts.substack.com
Thank you for your support. The Natto Team appreciates it.
17.12.2024 15:31 — 👍 7 🔁 2 💬 0 📌 2