Cool! It looks like this parallelizes well, you say you can execute joint Pauli measurements. Does this work equally well if there is a lot of overlap in the support of the logical Paulis?
12.12.2025 22:20 — 👍 1 🔁 0 💬 1 📌 0


We don’t talk often enough about the Superman issue where, fed up with pedestrian deaths from car collisions, he sets out to try and destroy every car in the city.
21.07.2025 01:20 — 👍 505 🔁 159 💬 14 📌 17

Photo of a piece of cardboard with a hexagonal grid, rules handwritten on looseleaf, cardboard pieces, and a box of mini wheats labelled "Settlers of Catan"
Photo memory: a bootleg version of settlers of Catan I made from memory during summer fieldwork in 2012
28.11.2025 13:37 — 👍 3 🔁 0 💬 0 📌 0
YouTube video by Oh The Urbanity!
How This Small City Built Light Rail For Cheap
I love my city youtu.be/uttoyAX4ntc?...
24.09.2025 23:10 — 👍 7 🔁 0 💬 0 📌 0
MenezesFest 2025
MenezesFest brings together researchers, colleagues, and friends to celebrate the career and impact of Alfred Menezes.
The impact of Alfred Menezes in cryptography is profound. Francisco RH and I are organizing an afternoon session in Latincrypt to celebrate Alfred's career:
menezesfest.info
If you're coming to Medellín, consider attending!
18.09.2025 06:17 — 👍 12 🔁 6 💬 1 📌 0
Nice! Now (to steal Luca's joke) it's only 11 more factors of 2 to go for SQISign to be faster than MLDSA?
13.09.2025 20:57 — 👍 2 🔁 0 💬 2 📌 0

Screenshot of comments in code. They say: Dear programmer: when I wrote this code, only God and I know how it worked. Now, only God knows it! Therefore, if you are trying to optimize this routine and it fails (most surely), please increase this counter as a warning for the next person. Total hours wasted here = 254
04.09.2025 16:14 — 👍 0 🔁 0 💬 0 📌 0
This is a valid signature for user i. Then when the adversary presents a forgery (w*,c*,z*) against user j, just subtract cr_j from z* and it's a forgery for your challenger. This works... but only because the public key was not hashed into the challenge! Very bad idea!
03.09.2025 17:38 — 👍 1 🔁 0 💬 0 📌 0
Your challenger's public key is xP, so all the users you simulate for the multi-user adv can use PK_i=(x+r_i)P for some random r_i. If the adversary requests a signature on m from user r_i, you can send m to your challenger and get (w,c,z)=(yP,H(w||m),y+cx). Set z'=z+cr_i and return (w,c,z').
03.09.2025 17:38 — 👍 1 🔁 0 💬 1 📌 0
Always bothers me when you lose the 1/N factor in a multi-user security proof. Was thinking about how to dodge it; consider this for Schnorr signatures: you are an active adversary against a single challenger, with access to a multi-user adversary.
03.09.2025 17:38 — 👍 2 🔁 0 💬 1 📌 0

Ursula K. LeGuin on technology
13.01.2025 13:53 — 👍 7415 🔁 2003 💬 115 📌 153
I was way miscalibrated at the time and thought the extra Toffoli count would end up using more space in the end thanks to state distillation. Not sure how typical my perspective was
Important lesson in scientific celebrity culture nonetheless
31.07.2025 23:28 — 👍 3 🔁 0 💬 0 📌 0
I've been reading "Burdens of proof", which makes an interesting point on this: law wants to operate on a vastly longer time scale than most file formats, for good reason.
22.07.2025 01:40 — 👍 0 🔁 0 💬 0 📌 0
So we have an adversary that can decrypt c to a different message with a different key? They can just compute their own tag of this other key and message, hash it, and replace the "T" part of the ciphertext?
08.07.2025 00:59 — 👍 0 🔁 0 💬 1 📌 0
Reasonable! When I read the screenshot you took, I see a lot of technical terms I can't contextualize. How meaningful is a "2 star relationship"? I can't tell but an expert in the field could.
Then again, scientists asked for quotes can absolutely give a rushed take and get things wrong.
03.07.2025 16:03 — 👍 0 🔁 0 💬 1 📌 0
It's normal and good for journalists to talk to scientists in the same field but not associated to the research, as they can offer an informed but less biased take
03.07.2025 15:39 — 👍 2 🔁 0 💬 0 📌 0
My current model of agriculture is we generally optimize for high yield at low labour, and there's room for high-yield and sustainable if we accept high labour inputs. Is this a plausible and useful perspective?
03.07.2025 15:36 — 👍 0 🔁 0 💬 0 📌 0
Oh of course not, it would be a tourist attraction. Maybe a quirky hotel
21.06.2025 17:34 — 👍 0 🔁 0 💬 0 📌 0

Graph of physical qubits vs. year. There is a cluster of points in the middle, with 3 lines trying to extrapolate forward, but with wide error margins.
I wouldn't say steady: arxiv.org/abs/2009.05045 tries to extrapolate and the data looks really noisy. E.g., fig. 8. If we put today's devices on this, the best would maybe on the orange line
20.06.2025 20:55 — 👍 3 🔁 0 💬 1 📌 0
Probably closer to 13 doublings if we look at chips with all the good properties we want. There hasn't been a consistent exponential growth yet.
20.06.2025 17:53 — 👍 1 🔁 0 💬 1 📌 0

Figure 14 from Gidney's paper showing a dense 3-d pipe diagram of a surface code layout of a lookup. Most of the 3-d space is used in some way.
Craig Gidney's work tackles that question: arxiv.org/abs/2505.159.... Check out the figures in the appendix: the physical qubits are used quite densely!
20.06.2025 00:40 — 👍 0 🔁 0 💬 0 📌 0
If I get what you're talking about: a different technique (arxiv.org/abs/1905.100...) compresses the output bits, which is incompatible (if you compress input as well, you can factor with a classically simulatable # of qubits: likely impossible).
20.06.2025 00:05 — 👍 0 🔁 0 💬 1 📌 0
And on a network of quantum computers, you'd have to re-optimize the algorithm, which would push the resource estimates back up
19.06.2025 23:23 — 👍 0 🔁 0 💬 0 📌 0
To be clear there is no 2100 qubit device! Maybe I should rewrite that part :) but the estimates assume one device. There are known methods to network quantum devices together, but the tech is lagging behind a bit compared to the speed and quality of of one device
19.06.2025 23:23 — 👍 0 🔁 0 💬 1 📌 0
A 20x improvement warrants an "extra"!
19.06.2025 22:12 — 👍 2 🔁 0 💬 0 📌 0
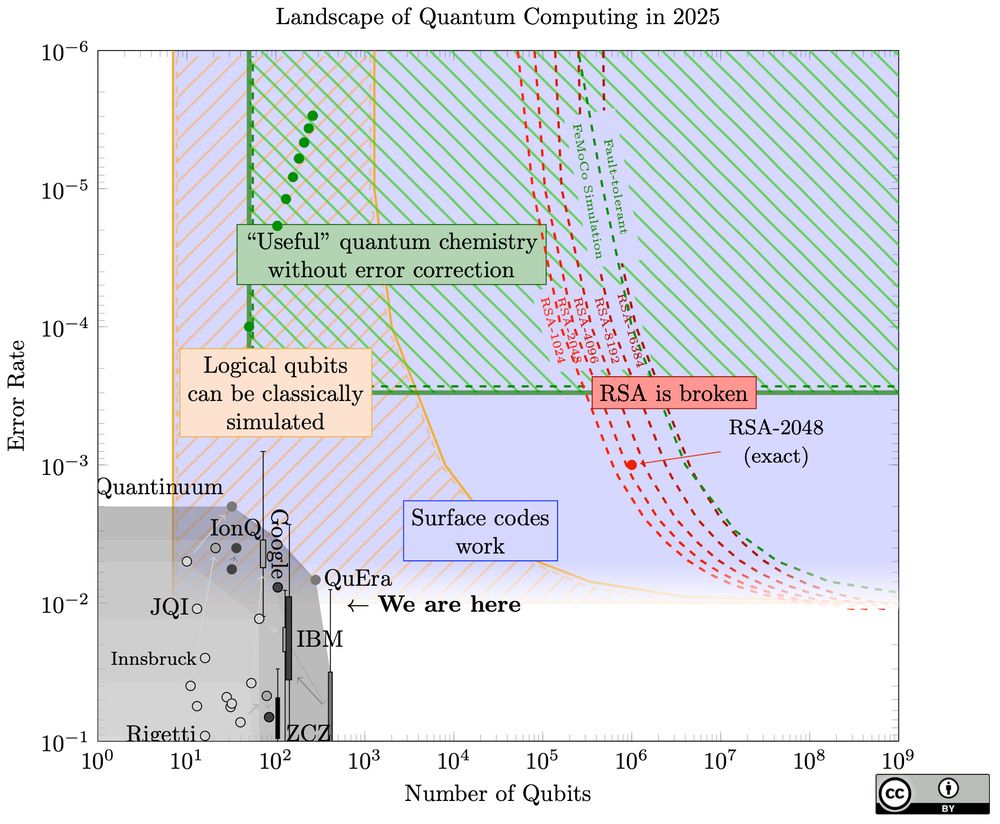
A chart for quantum computers, of number of qubits versus error rate, on a logarithmic scale. Broadly it shows a large gap between current quantum computers in the bottom left, and a curve in the top right of the resources they need to break RSA.
An out-of-schedule update to my quantum landscape chart: sam-jaques.appspot.com/quantum_land..., prompted by
@craiggidney.bsky.social 's new paper: arxiv.org/abs/2505.15917.
A startling jump (20x) in how easy quantum factoring can be!
Also: much improved web design!
19.06.2025 18:52 — 👍 61 🔁 26 💬 3 📌 0
That'd be a killer bsky bio
15.06.2025 20:31 — 👍 0 🔁 0 💬 0 📌 0
Though, I don't think she has enough theory of mind to understand that I don't have night vision, so to her it was just a devastating snub
09.06.2025 23:15 — 👍 1 🔁 0 💬 0 📌 0
Master's student at ENS Paris-Saclay, interested in complexity theory, cryptography and quantum computing.
Assistant Professor @ Eurecom. I'm interested in formal methods for low-level security. https://leslyann-daniel.fr
“Interested in too many things and good at all of it”.
Pickle eater.
Pronouns: She/her
Thoroughly asymmetric since July 2, 2023
PhD, Post-Quantum cryptography.
https://error0024.github.io/
Quantum. Virginia Tech and Phasecraft.
PhD Student at UMD studying Cryptography
website: sasha.place
Formerly at Meta/Cornell
quantum stuff @ QuSoft, University of Amsterdam & CWI
Quantum physicist & sci commer | Quantum computing @OQC_Tech | PhD @UniofOxford | Outreach @qqq_iop | Founder @quantuminfosoc | Prev. @IBM @Qiskit @PhysicsWorld
Website https://cbcrypto.org
Fediverse https://ioc.exchange/@cbcrypto
Professor in #Cryptography at Aarhus University. Research interests: #MultipartyComputation #ZeroKnowledge #Blockchain
Building: Partisia Blockchain, Concordium.
Originally from Florence, Italy.
News/features about semiconductors from CRN Senior Editor Dylan Martin. Send tips to dmartin@thechannelco.com or dylanljmartin.81 on Signal. Find my articles here: https://www.crn.com/authors/dylan-martin
PhD candidate at Centrum Wiskunde & Informatica (CWI) and QuSoft | Designing quantum and classical algorithms for cryptanalysis of post-quantum cryptography 🔍
Cryptography professor at the University of Waterloo
https://www.douglas.stebila.ca/
Generalist civic technologist (& final year DPhil). Principal consultant. Norwich with a cargo bike. Greyhound pictures extra.
DC. political philosopher at Georgetown, editor at @hammerandhope.bsky.social, rhythm guitarist + vox for @femiandfoundation.bsky.social. #COYS
independent writer of citationneeded.news and @web3isgoinggreat.com • tech researcher and cryptocurrency industry critic • software engineer • wikipedian
support my work: citationneeded.news/signup
links: mollywhite.net/linktree
💗💜💙
UFW - fighting for farm workers since 1962. Sí Se Puede!®










