
The call for papers for PKC 2026 is out: pkc.iacr.org/2026/callfor...
25.09.2025 17:53 — 👍 6 🔁 9 💬 0 📌 0@kutasp89.bsky.social

The call for papers for PKC 2026 is out: pkc.iacr.org/2026/callfor...
25.09.2025 17:53 — 👍 6 🔁 9 💬 0 📌 0
Abstract. The long-term success of cryptocurrencies largely depends on the incentive compatibility provided to the validators. Bribery attacks, facilitated trustlessly via smart contracts, threaten this foundation. This work introduces, implements, and evaluates three novel and efficient bribery contracts targeting Ethereum validators. The first bribery contract enables a briber to fork the blockchain by buying votes on their proposed blocks. The second contract incentivizes validators to voluntarily exit the consensus protocol, thus increasing the adversary’s relative staking power. The third contract builds a trustless bribery market that enables the briber to auction off their manipulative power over the RANDAO, Ethereum’s distributed randomness beacon. Finally, we provide an initial game-theoretical analysis of one of the described bribery markets.
Bribers, Bribers on The Chain, Is Resisting All in Vain? Trustless Consensus Manipulation Through Bribing Contracts (Bence Soóki-Tóth, István András Seres, Kamilla Kara, Ábel Nagy, Balázs Pejó, Gergely Biczók) ia.cr/2025/1719
22.09.2025 00:46 — 👍 1 🔁 1 💬 0 📌 0TL;DR: we solve norm equations in a better way and get around a 2x improvement to IdealToIsogeny routines crucial in both SQIsign and PRISM.
12.09.2025 14:00 — 👍 12 🔁 5 💬 2 📌 01, I don't think that's true. 2, MLDSA is a lot worse in terms of public key+ signature size. So I am not sure that is a fair comparison. I think since Luca made this joke there has been several other speed-ups (as the joke was before the HD versions).
14.09.2025 10:43 — 👍 2 🔁 0 💬 0 📌 0
Abstract. The main building block in isogeny-based cryptography is an algorithmic version of the Deuring correspondence, called IdealToIsogeny. This algorithm takes as input left ideals of the endomorphism ring of a supersingular elliptic curve and computes the associated isogeny. Building on ideas from QFESTA, the Clapoti framework by Page and Robert reduces this problem to solving a certain norm equation. The current state of the art is however unable to efficiently solve this equation, and resorts to a relaxed version of it instead. This impacts not only the efficiency of the IdealToIsogeny procedure, but also its success probability. The latter issue has to be mitigated with complex and memory-heavy rerandomization procedures, but still leaves a gap between the security analysis and the actual implementation of cryptographic schemes employing IdealToIsogeny as a subroutine. For instance, in SQIsign the failure probability is still 2⁻⁶⁰ which is not cryptographically negligible. The main contribution of this paper is a very simple and efficient algorithm called Qlapoti which approaches the norm equation from Clapoti directly, solving all the aforementioned problems at once. First, it makes the IdealToIsogeny subroutine between 2.2 and 2.6 times faster. This signigicantly improves the speed of schemes using this subroutine, including notably SQIsign and . On top of that, Qlapoti has a cryptographically negligible failure probability. This eliminates the need for rerandomization, drastically reducing memory consumption, and allows for cleaner security reductions.

Image showing part 2 of abstract.
Qlapoti: Simple and Efficient Translation of Quaternion Ideals to Isogenies (Giacomo Borin, Maria Corte-Real Santos, Jonathan Komada Eriksen, Riccardo Invernizzi, Marzio Mula, Sina Schaeffler, Frederik Vercauteren) ia.cr/2025/1604
11.09.2025 16:14 — 👍 6 🔁 4 💬 0 📌 2I spent a semester here as a student, I really love Strasbourg and Alsace in general!
08.09.2025 18:57 — 👍 2 🔁 0 💬 0 📌 0Ok maybe someone should send them a message explaining the situation then. To be fair this list is not as useful as hoped as detecting a predatory journal is trivial and the list contains a lot of false positives (TCHES being a prime example).
03.09.2025 20:27 — 👍 0 🔁 0 💬 0 📌 0Can someone provide me with an explanation how TCHES ended up on some Norwegian list for predatory journals?
03.09.2025 15:30 — 👍 1 🔁 0 💬 1 📌 0
Proud moment at #CRYPTO 2025!
“KLPT²: Algebraic Pathfinding in Dimension Two and Applications” received the Best Paper Award. 🏆
Co-authored by COSIC’s Wouter Castryck & Thomas Decru (presenter).
Read it here: eprint.iacr.org/2025/372
Very sad news
31.07.2025 11:38 — 👍 1 🔁 0 💬 0 📌 0
This exactly. And it's not just theoretical, it can happen for real. "The Chinese state-sponsored cyberattack threat managed to infiltrate the "lawful intercept" network connections that police use in criminal investigations." www.darkreading.com/cyber-risk/s...
06.07.2025 13:52 — 👍 9 🔁 2 💬 0 📌 0Yessss!!!
16.06.2025 09:48 — 👍 4 🔁 1 💬 0 📌 0Reminder that the MSCA postdoctoral program exists. If you have a PhD and want to work in a European lab, you have until September to apply. Just contact them now.
ec.europa.eu/info/funding...
![Abstract. In this paper we study supersingular elliptic curves primitively oriented by an imaginary quadratic order, where the orientation is determined by an endomorphism that factors through the Frobenius isogeny. In this way, we partly recycle one of the main features of CSIDH, namely the fact that the Frobenius orientation can be represented for free. This leads to the most efficient family of ideal-class group actions in a range where the discriminant is significantly larger than the field characteristic p. Moreover, if we orient with a non-maximal order $\mathcal{O} \subset \mathbb{Q}(\sqrt{-p})$ and we assume that it is feasible to compute the ideal-class group of the maximal order, then also the ideal-class group of 𝒪 is known and we recover the central feature of SCALLOP-like constructions.
We propose two variants of our scheme. In the first one, the orientation is by a suborder of the form $\mathbb{Z}[f\sqrt{-p}]$ for some f coprime to p, so this is similar to SCALLOP. In the second one, inspired by the work of Chenu and Smith, the orientation is by an order of the form $\mathbb{Z}[\sqrt{-dp}]$ where d is square-free and not a multiple of p. We give practical ways of generating parameters, together with a proof-of-concept SageMath implementation of both variants, which shows the effectiveness of our construction.](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:fwa55bujvdrwlwlwgqmmxmuf/bafkreibqnnsbrycfnj6lxmqemiovkeexw3n3kfjoj7vw2oybinwvn4xeym@jpeg)
Abstract. In this paper we study supersingular elliptic curves primitively oriented by an imaginary quadratic order, where the orientation is determined by an endomorphism that factors through the Frobenius isogeny. In this way, we partly recycle one of the main features of CSIDH, namely the fact that the Frobenius orientation can be represented for free. This leads to the most efficient family of ideal-class group actions in a range where the discriminant is significantly larger than the field characteristic p. Moreover, if we orient with a non-maximal order $\mathcal{O} \subset \mathbb{Q}(\sqrt{-p})$ and we assume that it is feasible to compute the ideal-class group of the maximal order, then also the ideal-class group of 𝒪 is known and we recover the central feature of SCALLOP-like constructions. We propose two variants of our scheme. In the first one, the orientation is by a suborder of the form $\mathbb{Z}[f\sqrt{-p}]$ for some f coprime to p, so this is similar to SCALLOP. In the second one, inspired by the work of Chenu and Smith, the orientation is by an order of the form $\mathbb{Z}[\sqrt{-dp}]$ where d is square-free and not a multiple of p. We give practical ways of generating parameters, together with a proof-of-concept SageMath implementation of both variants, which shows the effectiveness of our construction.

Image showing part 2 of abstract.
Orient Express: Using Frobenius to Express Oriented Isogenies (Wouter Castryck, Riccardo Invernizzi, Gioella Lorenzon, Jonas Meers, Frederik Vercauteren) ia.cr/2025/1047
05.06.2025 16:36 — 👍 5 🔁 3 💬 0 📌 0Optimal KLPT would be amazing, I would love that for 2026. Then 2028 could be optimal KLPT^2 :)
18.05.2025 16:27 — 👍 3 🔁 0 💬 1 📌 0
Title of the PhD course: Advances in Cryptography and Codes - Part 1: SQIsign Lecturers: Andrea Basso (IBM Research Zurich, CH), Luciano Maino (University of Bristol, UK) The course in short: The course offers a comprehensive and rigorous introduction to SQIsign, an advanced isogeny-based digital signature scheme designed to resist attacks from quantum computers. The course will present the mathematical foundations on which SQIsign is based and the algorithmic background necessary to understand and evaluate the security of SQIsign and other isogeny-based protocols. Complementing the theoretical material, the course also includes a practical laboratory where students will use SageMath to study and implement various aspects of SQIsign. Where (in presence): Department of Mathematics, University of Trento (IT) Via Sommarive, 5, 38123, Trento (online): https://unitn.zoom.us/j/88902079708 (Passcode: 532383) When: From May 19, 2025 to May 28, 2025 Detailed Program: Monday 19/05 10:30 - 12:30 (Room A205) & 14:30 - 16:30 (Room A221) Tuesday 20/05 10:30 - 12:30 (Room A215) & 14:30 - 16:30 (Room A213) Wednesday 21/05 10:30 - 12:30 (Room A218) & 14:30 - 16:30 (Room A215) Thursday 22/05 10:30 - 12:30 (Room A209) & 14:30 - 16:30 (Room A220) Friday 23/05 10:30 - 12:30 (Room A215) & 14:30 - 16:30 (Room A215) Tuesday 27/05 11:30 - 12:30 – Q&A, optional (Room A218) Wednesday 28/05 11:30 - 12:30 – Q&A, optional (Room A218)
Next week @lucianomaino.bsky.social and I will teach a week-long course on SQIsign at the University of Trento.
The course will be both in-person and online: if you're interested, you can tune in Monday morning at 10:30 at unitn.zoom.us/j/88902079708
(details and full schedule in the image below)
CECC 2025 will accept posters, submission deadline is the 23rd May (more details can be found at cecc2025.inf.elte.hu). Also we have great invited speakers (Carla Rafols, Thomas Decru, Stefan Dziembowski), so hope to see you in Budapest!
10.05.2025 19:04 — 👍 3 🔁 1 💬 0 📌 0This is cool heimberger.xyz/oprfs.html
08.05.2025 07:52 — 👍 14 🔁 6 💬 0 📌 0The SQIparty starts on Monday, but it's still time to register!
We prepared an exciting program for you with a balanced mix of talks, coding sprints, skillshares and other activities!
www.cig.udl.cat/SQIparty2025...
See you in Lleida!
New work: we explain cubical arithmetic in simple terms to show you how easy it is to compute pairings. Essentially, you only need to know the Montgomery ladder!
As a bonus, pairings from cubical arithmetic are faster than those from Miller's loop for applications in isogeny-based cryptography.
Really excited to share the Decrypting Diversity Summit happening in Montpellier, France from 17-20 June! The goal of the summit is to promote diversity, inclusivity, and gender equality within the cryptography community. For more info: decryptingdiversity.com
03.04.2025 12:11 — 👍 9 🔁 6 💬 1 📌 0Deadline to submit to this conference is today!
31.03.2025 09:49 — 👍 2 🔁 1 💬 0 📌 0The second Levchin Prize goes to the CADO-NFS team: Emmanuel Thomé, Pierrick Gaudry, and Paul Zimmerman! Congratulations!
#realworldcrypto
Registration is now open! www.cig.udl.cat/SQIparty2025...
24.03.2025 09:14 — 👍 3 🔁 4 💬 0 📌 0
Cathedral of La Seu Vella in Lleida
Fancy some isogeny crypto?
Join us for a 3-day workshop on isogeny-based cryptography in Lleida, Catalonia, April 28-30
www.cig.udl.cat/icrypto2025_...
Brought to you by ULleida's Cryptography+Graphs group, the SQIsign team and friends!
Registration and program coming soon
Registration is free!
Next week (Tuesday 5pm CET) at The Isogeny Club we'll have Laurane Marco (EPFL) who will talk to us about computing modular polynomials modulo a generic prime! More details at isogeny.club
06.03.2025 12:58 — 👍 10 🔁 4 💬 0 📌 0
Abstract. We study recent algebraic attacks (Briaud-Øygarden EC’23) on the Regular Syndrome Decoding (RSD) problem and the assumptions underlying the correctness of their attacks’ complexity estimates. By relating these assumptions to interesting algebraic-combinatorial problems, we prove that they do not hold in full generality. However, we show that they are (asymptotically) true for most parameter sets, supporting the soundness of algebraic attacks on RSD. Further, we prove—without any heuristics or assumptions—that RSD can be broken in polynomial time whenever the number of error blocks times the square of the size of error blocks is larger than 2 times the square of the dimension of the code. Additionally, we use our methodology to attack a variant of the Learning With Errors problem where each error term lies in a fixed set of constant size. We prove that this problem can be broken in polynomial time, given a sufficient number of samples. This result improves on the seminal work by Arora and Ge (ICALP’11), as the attack’s time complexity is independent of the LWE modulus.

Image showing part 2 of abstract.
On the Soundness of Algebraic Attacks against Code-based Assumptions (Miguel Cueto Noval, Simon-Philipp Merz, Patrick Stählin, Akin Ünal) ia.cr/2025/415
05.03.2025 15:55 — 👍 2 🔁 1 💬 0 📌 0
16th International Conference on Cryptology AFRICACRYPT 2025
July 21-23, 2025 – Rabat, Morocco 🇲🇦
Extended submission deadline in 1 week:
africacrypt2025.sciencesconf.org
Submit your best results !
See you in Rabat 🇲🇦 in July 2025.
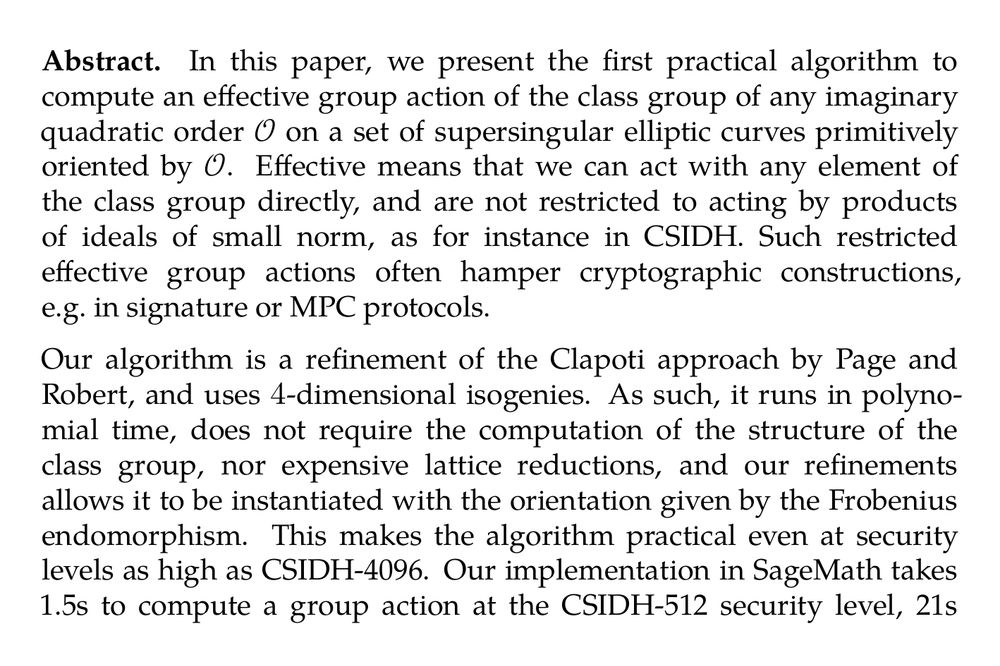
Abstract. In this paper, we present the first practical algorithm to compute an effective group action of the class group of any imaginary quadratic order 𝒪 on a set of supersingular elliptic curves primitively oriented by 𝒪. Effective means that we can act with any element of the class group directly, and are not restricted to acting by products of ideals of small norm, as for instance in CSIDH. Such restricted effective group actions often hamper cryptographic constructions, e.g. in signature or MPC protocols. Our algorithm is a refinement of the Clapoti approach by Page and Robert, and uses 4-dimensional isogenies. As such, it runs in polynomial time, does not require the computation of the structure of the class group, nor expensive lattice reductions, and our refinements allows it to be instantiated with the orientation given by the Frobenius endomorphism. This makes the algorithm practical even at security levels as high as CSIDH-4096. Our implementation in SageMath takes 1.5s to compute a group action at the CSIDH-512 security level, 21s at CSIDH-2048 level and around 2 minutes at the CSIDH-4096 level. This marks the first instantiation of an effective cryptographic group action at such high security levels. For comparison, the recent KLaPoTi approach requires around 200s at the CSIDH-512 level in SageMath and 2.5s in Rust.

Image showing part 2 of abstract.
PEGASIS: Practical Effective Class Group Action using 4-Dimensional Isogenies (Pierrick Dartois, Jonathan Komada Eriksen, Tako Boris Fouotsa, Arthur Herlédan Le Merdy, Riccardo Invernizzi, Damien Robert, Ryan Rueger, Frederik Vercauteren, Benjamin Wesolowski) ia.cr/2025/401
04.03.2025 08:20 — 👍 13 🔁 6 💬 0 📌 3As part of the round-2 NIST submission, we developed a complete proof of security of SQIsign!
04.03.2025 09:05 — 👍 11 🔁 5 💬 1 📌 0