If you’re passionate about broadening who gets seen, heard, and valued in this field, attend and lets continue the conversation in person. www.mincybsec.org/an...
12.02.2026 12:46 — 👍 0 🔁 0 💬 0 📌 0
(beyond job titles, traditional career paths, and gatekeeping checklists)
12.02.2026 12:46 — 👍 0 🔁 0 💬 1 📌 0
Excited to share that I've been asked to speak at the Minorities in Cybersecurity Conference this March!
I’ll be on a panel “How Do You Define Cybersecurity Experience? A Change in Perspective” where we’ll dig into what really counts as cybersecurity experience
12.02.2026 12:45 — 👍 0 🔁 0 💬 1 📌 0
My latest pet project, an RSS feed to alert you to the silent KEV knownRansomwareCampaignUse flips!
(Did you know there were four CVEs flipped last week?) #threatintel
02.02.2026 19:54 — 👍 2 🔁 0 💬 0 📌 0

🍩 & #threatintel - 95% of exploitation attempts targeting CVE-2026-20045, a critical vulnerability in Cisco Unified Communications Manager, have used a distinctive user-agent: Mozilla/5.0 (compatible; CiscoExploit/1.0) and are heavily targeting our Cisco Unified Communications Manager sensors.
1/2
31.01.2026 16:52 — 👍 0 🔁 0 💬 2 📌 0
CISA's KEV hit 1,500 yesterday. I'm working on a cool #threatintel blog (yes, I'm biased) about additional hidden intel in KEV that should be published soon, along with a helpful tool hosted by GreyNoise! :)
28.01.2026 17:33 — 👍 1 🔁 0 💬 0 📌 0
If I recall correctly, this is the first time the due date has been modified.
In all honesty, if you haven't already patched this vulnerability, it's likely too late. As a reminder, patching does not boot attackers, so you should check for indicators of compromise.
2/2
10.12.2025 14:04 — 👍 0 🔁 0 💬 0 📌 0

☕ & #threatintel: CISA has moved the due date for mitigating CVE-2025-55182 (Meta React Server Components Remote Code Execution Vulnerability) up by two weeks. It was initially set for December 26, but it is now due on December 12.
1/2
10.12.2025 14:04 — 👍 3 🔁 1 💬 1 📌 0
Presented at SuriCon 2025 by Ron Bowes and Glenn Thorpe
Network protocols are messy! Sure, there are standards — RFCs, IEEEs, you name it — but there are also multiple ways to do basically everything. If you’re relying on network IDS/IPS tools like Suricata, I have bad news — a sufficiently cl
SuriCon 2025 | Abusing HTTP Quirks to Evade Detection
Ron & my talk from SuriCon 2025 | Abusing HTTP Quirks to Evade Detection
I think it turned out pretty well; pardon the disco effect where a stage light was failing :)
www.youtube.com/watc...
CC: @iagox86.bsky.social @greynoise.io
09.12.2025 22:41 — 👍 6 🔁 3 💬 0 📌 0

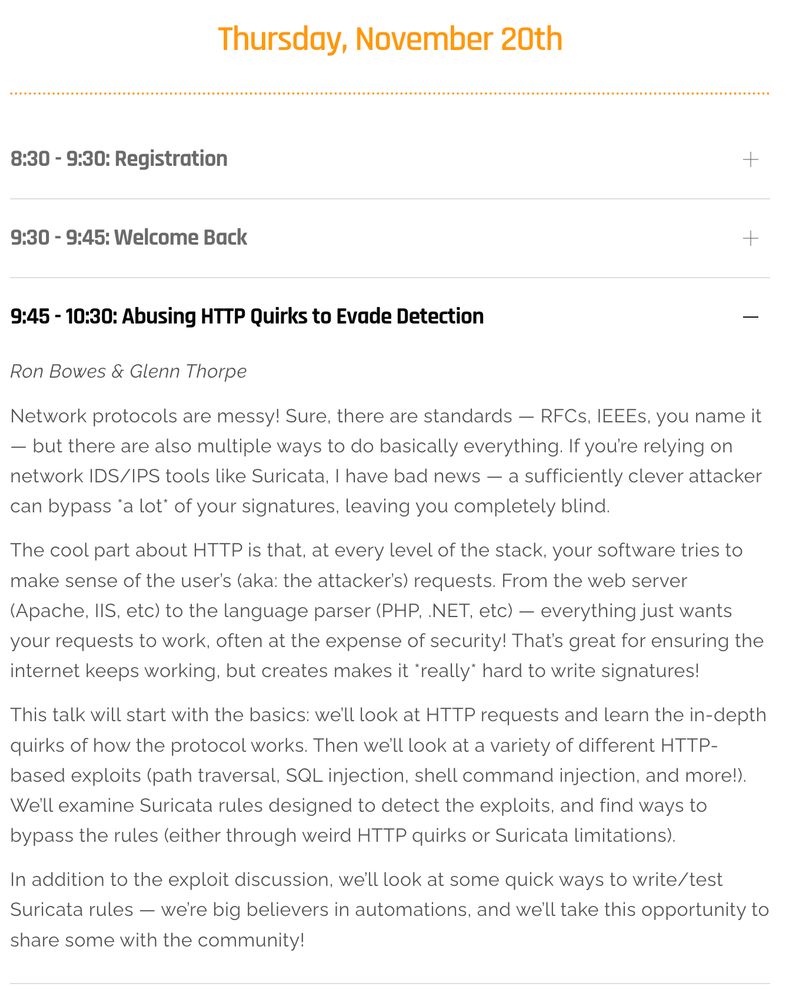
Network protocols are messy! Sure, there are standards — RFCs, IEEEs, you name it — but there are also multiple ways to do basically everything. If you’re relying on network IDS/IPS tools like Suricata, I have bad news — a sufficiently clever attacker can bypass *a lot* of your signatures, leaving you completely blind.
The cool part about HTTP is that, at every level of the stack, your software tries to make sense of the user’s (aka: the attacker’s) requests. From the web server (Apache, IIS, etc) to the language parser (PHP, .NET, etc) — everything just wants your requests to work, often at the expense of security! That’s great for ensuring the internet keeps working, but creates makes it *really* hard to write signatures!
This talk will start with the basics: we’ll look at HTTP requests and learn the in-depth quirks of how the protocol works. Then we’ll look at a variety of different HTTP-based exploits (path traversal, SQL injection, shell command injection, and more!). We’ll exam
Ron (@iagox86.bsky.social) and I are presenting at #Suricon (Montreal) next month! If you're around, you'll definitely want to find us for some sweet swag (oh, and our talk is pretty cool too!).
suricon.net/agenda-m...
21.10.2025 14:37 — 👍 3 🔁 1 💬 0 📌 0


It’s time for many folks’ annual cultural learning session. 🤣
03.10.2025 12:22 — 👍 1 🔁 0 💬 0 📌 0
We all know that @hrbrmstr.dev is a mad scientist, and when you give him the amazing telemetry our new fleet has been collecting lately, you get knowledge drops like this! Super proud of our @greynoise.io team’s work on the deception capabilities we now have! hashtag#threatintel
01.08.2025 15:24 — 👍 1 🔁 2 💬 0 📌 0
🫖 & #threatintel - noticing a few other spikes orgs should be mindful of:
🔥 CVE-2025-49132 (Pterodactyl Panel RCE) (10/10 RCE)
⚡ CVE-2024-20439 (Cisco Smart Licensing Utility) (9.8/10, KEV)
📝 CVE-2017-18370 (Zyxel P660HN)
1/4
16.07.2025 21:45 — 👍 0 🔁 0 💬 1 📌 0
The main takeaway is we, first hand, observed exploitation almost two weeks before the POC was released, so ensure all retro threat hunting goes back at LEAST a month, but ideally further.
2/2
16.07.2025 21:05 — 👍 2 🔁 0 💬 0 📌 0
🥜 & #threatintel - Thanks to @horizon3ai.bsky.social, we pushed a tag out today for CitrixBleed 2 CVE-2025-5777 and are backfilling. Currently, we see 233 hits starting on July 1 from:
64.176.50[.]109
38.154.237[.]100
102.129.235[.]108
121.237.80[.]241
45.135.232[.]2
Follow along...
1/2
07.07.2025 21:56 — 👍 2 🔁 0 💬 1 📌 0
Just a totally normal trip home from the airport last night… passing the national guard rolling down the highway as they prepare for NO KINGS DAY protests. F this administration. About 3 more months before they start trying to censor social media via tech controls.
12.06.2025 14:37 — 👍 3 🔁 0 💬 0 📌 0
It's hard to beat good deception. :)
28.05.2025 15:38 — 👍 7 🔁 0 💬 0 📌 0
If you're ever feeling lonely, just close Zoom.
This works because a funny thing always happens: a random last-minute Zoom will appear if you close it completely.
27.05.2025 21:21 — 👍 1 🔁 0 💬 0 📌 0

🥤& #threat-intel: CISA added Langflow Code Injection CVE-2025-3248 to the KEV on May 5. Recently, it has garnered considerable attention, with South Korea leading the pack. This vuln enables unauthenticated attackers to execute arbitrary code via /api/v1/validate/code
viz.greynoise.io/tag...
15.05.2025 22:06 — 👍 5 🔁 2 💬 0 📌 0
threat hunturrrr | staff @vxunderground || PTC
Improve your security posture and reduce risk with the NodeZero™ platform.
A new DC hacker conference: Bringing together builders, breakers, and fixers to do cool shit.
Jan. 24-25, 2026
districtcon.org
Senior Digital Editor for MeidasTouch.com
Clips made with SnapStream
Internet Hooligan...
Always fighting for the people.
Wife, Momala, Auntie. She/her.
107 Days, my behind-the-scenes account of the shortest campaign in history, is available now at https://kamalaharris.link/107Days.
Principal analyst @vtxproject / #Synapse
#APT1 report / former Mandiant
Doing #threatintel before it was a thing
Full-Time Campaigns Director @NRDC.org 🌎. Part-Time Westie belly scratcher 🐶. Breast cancer thriver. 🫶🏻 Denver based 🏔️ World bound. ✈️
Alum of:
✔️Kamala Harris
✔️First Descents
✔️Hillary
✔️Planned Parenthood
✔️Wellesley College
U.S. Senator, Massachusetts. She/her/hers. Official Senate account.
https://substack.com/@senatorwarren
No longer Bluesky’s only resident finance bro | Macro Strategist | Even the blind squirrel get a nut sometime. | QCR: Non Culto, For The Crown. | 🇺🇸 via 🇨🇦. Not 🏴. | Normal man, one of the Normal Men
*ALL CAPS HEADLINES LIKE THIS ARE FROM BLOOMBERG
📍 CLT
ALT gov account. ALT. Not an official DHS account (if they even have one on BlueSky). ALT
Retired Gov employee. I swear a lot. #Altgov
Discl: Not an official account for DHS. All opinions my own. Again, ALT. ALT. ALT.
hurt a cop’s feelings & he paid my legal bills. police accountability advocate, former food writer (Gannett, NPR, Scripps) & tech marketer (Cisco, Zebra). Now: 3L, event pro, consultant & biz owner. formerly winemedineme.
journalist / founder @ thehandbasket.co
email: marisa@thehandbasket.co
signal: https://signal.me/#eu/VssgH88q6WQu7MtH5wF-08JdgWh4iAPWD13eXiOcXQNGdZUXijJBZInD-UtLJKFG
venmo: venmo.com/u/Marisa-Kabas
ko-fi: https://ko-fi.com/marisakabas
Real-time updates on the latest filings in cases challenging Trump administration executive actions. Sponsored by @lawfare.bsky.social
Curated by @annahickey.bsky.social and @tylermcbrien.bsky.social
https://bots.law/little-cases/trump-litigation-bot
Cyber Intelligence Analyst at RANE
Available for media inquiries 🙂↔️🙂↕️
Cartoonist and creator of The Oatmeal and Exploding Kittens https://linktr.ee/theoatmeal
Award-winning fitness app for moving consistently, not constantly.
2024 Design Award Winner • 2022 ⌚App Of The Year
If you prefer longer threads: r/GentlerStreakApp
a.k.a. boB Rudis • 🇺🇦 Pampa • Don't look at me…I do what he does—just slower. #rstats #js #duckdb #goavuncular•👨🍳•✝️• 💤• Varaforseti í Gögn Vísindi @ GreyNoise • 47-watch.com • https://stormwatch.ing • https://dailydrop.hrbrmstr.dev • Maine🦞













