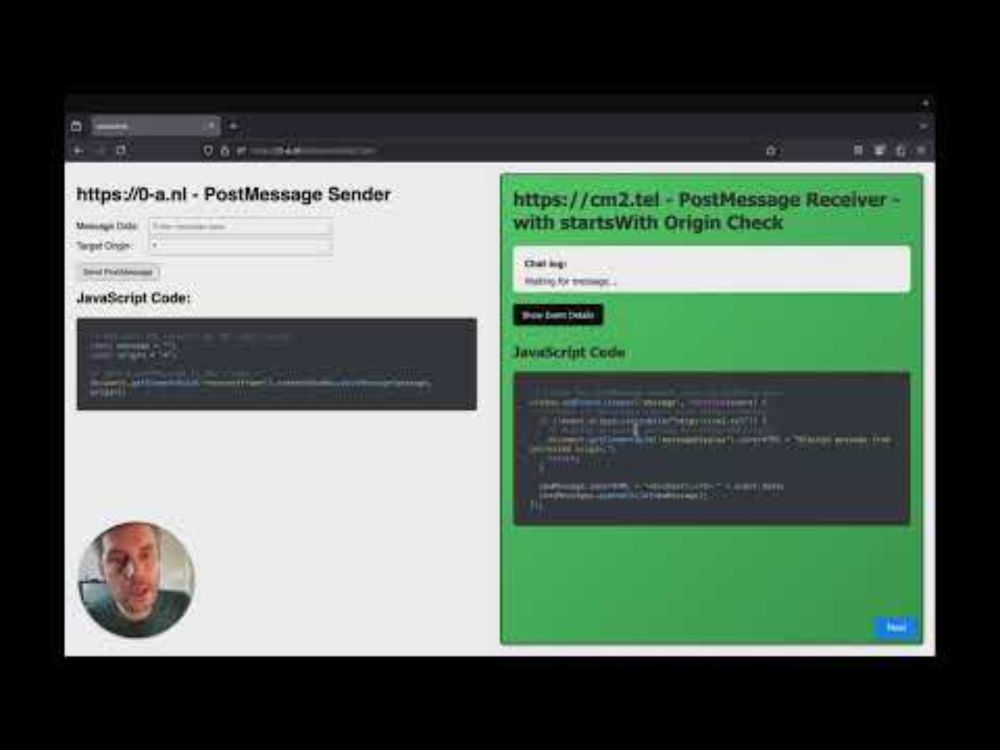
For those who missed it, check out my talk, “Widgets Gone Wild: Exploiting XSS through Flawed postMessage Origin Checks.”
📺 Watch here: www.youtube.com/watch?v=qgB0...
🖥️ Follow along with the slides: 0-a.nl/nahamcon/

For those who missed it, check out my talk, “Widgets Gone Wild: Exploiting XSS through Flawed postMessage Origin Checks.”
📺 Watch here: www.youtube.com/watch?v=qgB0...
🖥️ Follow along with the slides: 0-a.nl/nahamcon/
The slides and examples for my talk "Widgets Gone Wild: Exploiting XSS Through Flawed postMessage Origin Checks" at NahamCon can be found here: 0-a.nl/nahamcon/
24.05.2025 09:23 — 👍 8 🔁 4 💬 1 📌 0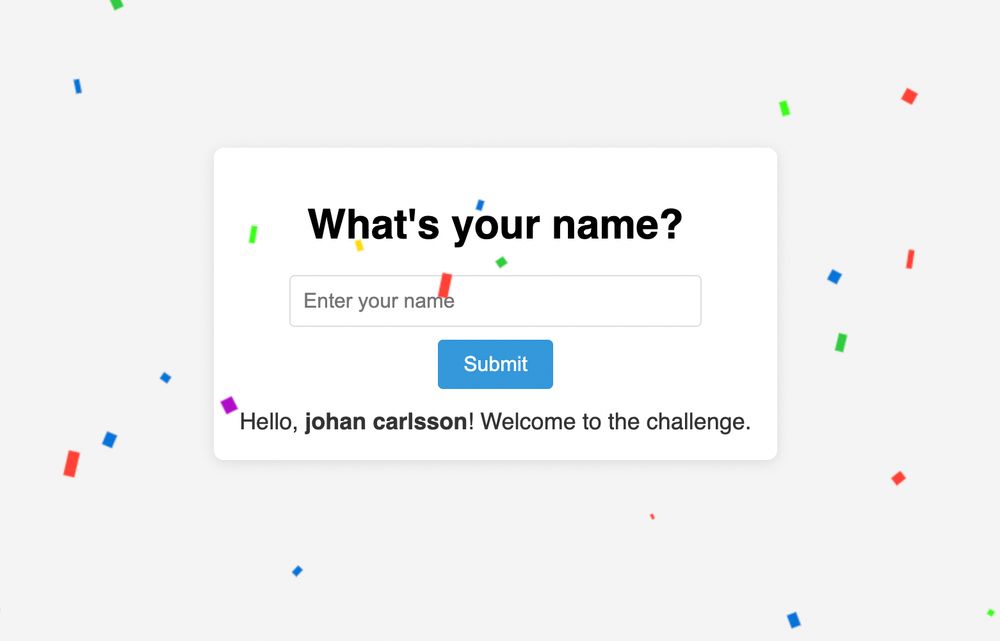
Here is the official writeup of my XSS challenge on Intigriti. I think it contains some fun browser trivia even for those who did not look at the chall
joaxcar.com/blog/2025/05...
I'm excited to be speaking at #NahamCon2025 on May 23rd!
I'm going to be talking about a bug class that I believe is very undervalued, and will outline a methodology for how to find and exploit it in the wild.
May the bounties rain down upon you!
Details here: www.nahamcon.com
I think with the race condition 11 is possible with: open(top.x)?
13.12.2024 15:50 — 👍 7 🔁 0 💬 1 📌 0
This is 13 without the race condition, using your cool build up method @terjanq.me:
www.tomanthony.co.uk/temp/joax1.h...
Within the rules of no framing / no window context, I think we can get down to 64 with:
fetch`/hack.js`.then(r=>r.text()).then(b=>open('javascript:'+b))
Or if you are 'cheating' and using the run() function on the page then you can do 16:
run(top[0].name)
If the real case was truly frameable, then you iframe another page on joaxcar.com, and then iframe this one with this 20 character payload:
location=top[0].name
If it isn't frameable, you can do 23 chars:
location=opener[0].name
I feel the same. I feel like years of Twitter made me much more cautious about what I shared. Trying to get out of that mindset now.
24.11.2024 08:27 — 👍 2 🔁 0 💬 0 📌 0I'm not sure that it is! But don't know for sure. I'll see if I can crack it this evening, but otherwise I'll ping your way. (Though you need to follow me so I can DM)
22.11.2024 12:48 — 👍 0 🔁 0 💬 1 📌 0Making lunch and already found one case partially working in the wild on a big target. Ping me a DM on X (@tomanthonyseo) if you want to collab on it! :)
22.11.2024 12:18 — 👍 0 🔁 0 💬 1 📌 0This is incredible research!
22.11.2024 10:48 — 👍 2 🔁 0 💬 1 📌 0
In case you missed it...the DEF CON video of my talk 'Splitting the Email Atom' is finally here! 🚀 Watch me demonstrate how to turn an email address into RCE on Joomla, bypass Zero Trust defences, and exploit parser discrepancies for misrouted emails. Don’t miss it:
youtu.be/JERBqoTllaE?...
I’m here! :)
21.11.2024 18:10 — 👍 3 🔁 0 💬 0 📌 0This is basically identical to how I hack! Look for the new thing and then see something that looks interesting. Hopefully get far enough that I have a ‘lead’ and take it from there.
20.11.2024 11:16 — 👍 2 🔁 0 💬 0 📌 0