Why do you think they all wear masks?
27.06.2025 13:20 — 👍 2 🔁 0 💬 0 📌 0@digitalwarhead.bsky.social
Success is not final; failure is not fatal: it is the courage to continue that counts. https://darknetdiaries.com/
@digitalwarhead.bsky.social
Success is not final; failure is not fatal: it is the courage to continue that counts. https://darknetdiaries.com/
Why do you think they all wear masks?
27.06.2025 13:20 — 👍 2 🔁 0 💬 0 📌 0
New from 404 Media: ICE is using a new facial recognition app to identify people, leaked emails show. Point camera at person, reveal their identity. It uses the CBP system that records peoples' faces as they enter or exit the U.S. Now, turned inwards to be used by ICE www.404media.co/ice-is-using...
26.06.2025 16:45 — 👍 5881 🔁 3561 💬 432 📌 571
Full guide covers OpSec, burner phones, data protection, secure communications, and handling law enforcement interactions.
Read: www.privacyguides.org/articles/202...
Key takeaways: Use strong passphrases to unlock phone, minimize stored data, prefer Signal for messaging, know your legal rights, and consider leaving your main phone at home entirely. #LA #Protests #ICE #DigitalRights #ProtestSafety #OpSec #PrivacyMatters
09.06.2025 20:50 — 👍 1 🔁 0 💬 1 📌 0With recent protests and the documented surveillance conducted by law enforcement with aerial drones, protecting your digital privacy has never been more critical. Your smartphone can be both a powerful tool for coordination and documentation, and a significant security risk if not secured. 🧵👇
09.06.2025 20:50 — 👍 0 🔁 0 💬 1 📌 0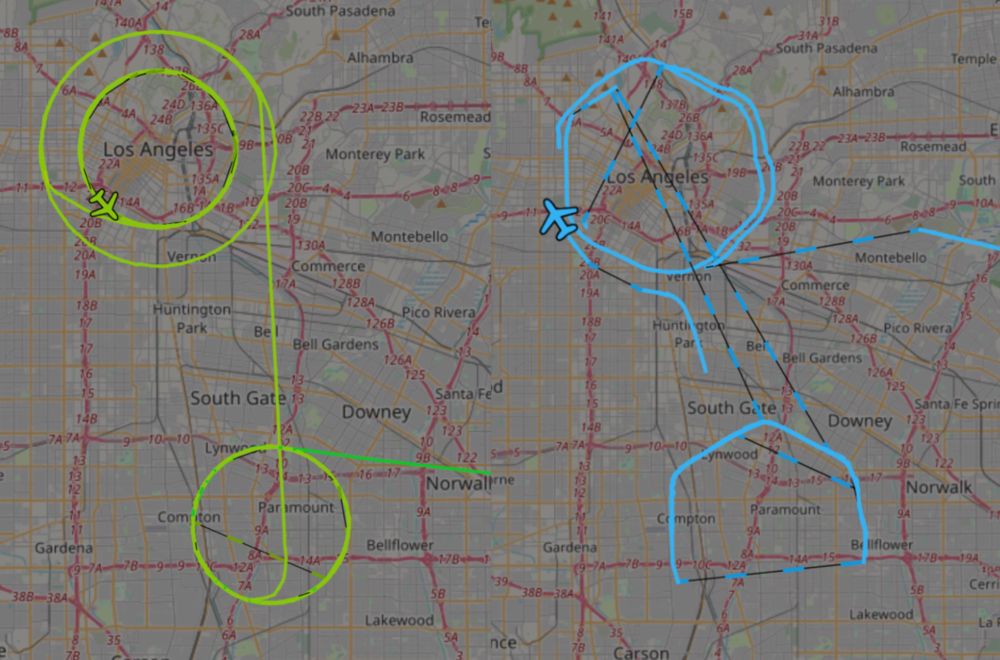
New from 404 Media: here's our report on the aircraft circling above the LA protests. Local, state, DHS, military all flew. Left: aircraft from air base. Right: a distinctive high altitude/hexagonal flight pattern, looks like a Predator drone (it flew to border after) www.404media.co/dhs-black-ha...
09.06.2025 13:36 — 👍 451 🔁 211 💬 10 📌 9
A picture worth 0x3E8 words at Bsides Seattle. @00wham.bsky.social
19.04.2025 16:51 — 👍 2 🔁 0 💬 0 📌 0
Here's part one of his 3-part series. The series is great, but overall PrestonGoes is one of the best YouTube channels I've found. He's an incredibly genuine and positive guy and his videos are fun to watch.
youtu.be/FgOJwFLF26k?...
@abyssdomainexpert.bsky.social Absolutely loved your talk at HC Seattle last year. When I heard the @jackrhysider.bsky.social episode, I had to do some digging to see if it was the same person or someone else with an identical story lol. Glad to find you on here.
08.01.2025 20:27 — 👍 1 🔁 0 💬 1 📌 0
Thank you Jack Rhysider and @DarknetDiaries for letting me tell the Bike Index story darknetdiaries.com/episode/153/
07.01.2025 15:18 — 👍 1 🔁 1 💬 1 📌 0Well that was incredibly creepy lol. Nice work!
21.12.2024 07:19 — 👍 1 🔁 0 💬 0 📌 0Ok, this is brilliant. @sirocyl.bsky.social set up a DTMF bomb on their voicemail message to spam DTMF tones to spammers and jam up their PBX systems. They accidently broke Ikea.
cohost.org/sirocyl/post...
“if you don’t have a family then make one” okay fine im making an ai family for the holidays
27.11.2024 05:58 — 👍 3 🔁 1 💬 0 📌 0No I haven't had to log in since creating my account 🤷♂️
27.11.2024 03:09 — 👍 0 🔁 0 💬 0 📌 0@fixit42.bsky.social Heya FixIt! 💜
26.11.2024 14:19 — 👍 0 🔁 0 💬 0 📌 0the friends of cabal starter pack!
go.bsky.app/JAR9jhy
No, not personally. This was one of the challenges on OWASP's WebGoat, and I figured I'd make a post about it.
25.11.2024 22:11 — 👍 0 🔁 0 💬 0 📌 0@owasp.org too
25.11.2024 15:16 — 👍 0 🔁 0 💬 0 📌 0@johnhammond.bsky.social should definitely be on this list. He puts out great content.
25.11.2024 15:12 — 👍 0 🔁 0 💬 0 📌 0
Shout out to @owasp.org and github.com/WebGoat/WebG... for putting together this great example!
24.11.2024 21:59 — 👍 2 🔁 0 💬 0 📌 0Tips to stay safe from cookie hijacking:
✅ Websites: Use random, encrypted session cookies over HTTPS.
✅ Users: Log out after use, enable MFA, and avoid untrusted networks. Protect your cookies and keep hackers out! 🔐

We intercept the login request as Admin, swap in the cookie we created for Tom, and boom — we're logged in as him! 🕵️ This is cookie hijacking in action. Weak session cookies can expose accounts. Secure cookies save lives! 🛡️
24.11.2024 21:59 — 👍 1 🔁 0 💬 1 📌 0

The decoded cookies reveal plain text:
Webgoat: nzozZtxkdKtaogbew
Admin: nzozZtxkdKnimda
Reversing these strings, we see the username is reversed at the end.
To impersonate Tom, we reverse “Tom,” encode it in hex, then Base64. Crafting Tom’s session cookie lets us hijack his account! 😱

Authentication cookies like spoof_auth are often Base64 encoded. If predictable, they can be exploited! Logging in with credentials we know of such as Webgoat and Admin, we find:
Webgoat: NmU3YTZm...
Admin: NmU3YTZm...
Decoded, these cookies reveal hex patterns. Time to exploit them! 🔓
What is cookie hijacking? 🍪🔒
Authentication cookies keep you logged in, but if they're predictable, hackers can use them to impersonate you. Let’s explore how a vulnerable site can be exploited to log in as someone else. Stay tuned! 🕵️♂️
@gachikuku.bsky.social
pastebin.com/mhm4u0Mk
@bryanbrake.bsky.social you may be interested in this starter pack.
21.11.2024 23:27 — 👍 1 🔁 1 💬 0 📌 0@jameskettle.com has put together a great starter pack for bug bounty hunters and InfoSec creators on BlueSky. #infosec #bugbounties #contentcteators
go.bsky.app/GD7hKPX