I would definitely prefer to get a comprehensible spec out of gnupg before merging any changes, just in case we guess wrong. 🙃
04.01.2026 23:05 — 👍 1 🔁 0 💬 0 📌 0
Did you (or claude?) find a source for the offending format change btw?
04.01.2026 22:50 — 👍 0 🔁 0 💬 2 📌 0
Thanks! I think it would be more reliable to detect the novel format by length rather than the prefix byte, because of the risk of accidental collision. But otherwise the idea is reasonable. I’m going to raise this with gnupg because it’s yet another example of underdocumented novelty… 🫠
04.01.2026 22:50 — 👍 2 🔁 0 💬 1 📌 0
The two main missing pieces IMO are HKPv2 and key replacement. HKPv2 allows us to safely serve certificate bundles that include v4 and v6 certs, and key replacement formalises a directed graph between the individual certs.
04.01.2026 22:42 — 👍 1 🔁 1 💬 2 📌 0
Yes, the whole thing is a mess, and there are bits everywhere. But also, the context has been fluid for a couple of years. But maybe the time has come for an opinionated summary.
04.01.2026 22:18 — 👍 1 🔁 0 💬 0 📌 0
The creation of the signed repo is configurable IIRC, but I’m not sure what ubuntu uses currently on launchpad. Probably best to stick with v4 keys until it’s clear that all the component parts of the pipeline have been updated…
04.01.2026 20:00 — 👍 1 🔁 0 💬 1 📌 0
Beware that Ubuntu PPAs can’t use v5 keys, because as of apt 2.9.19 they rely on sq rather than gnupg for openpgp. You would need to generate a v6 key instead (which can’t be done with gnupg). 😬
04.01.2026 14:20 — 👍 2 🔁 0 💬 1 📌 0
Did you consider talking to the maintainer first? 😇
04.01.2026 10:23 — 👍 1 🔁 0 💬 1 📌 0
Very clever. Now calculate it as a percentage of all transactions.
20.12.2025 16:56 — 👍 0 🔁 0 💬 0 📌 0
It's really important to note that not only was Watson a racist and misogynist but his contribution to the double helix was listening to a Rosalind Franklin lecture and getting mad because Francis Crick wouldn't invite him to his sex parties.
07.11.2025 19:59 — 👍 276 🔁 104 💬 10 📌 7

Gender in English - Wikipedia
It *mostly* doesn’t, but the corpse of its earlier life as a gendered language is still present. see e.g. en.wikipedia.org/wiki/Gender_...
06.11.2025 23:52 — 👍 0 🔁 0 💬 0 📌 0
@expresbro.bsky.social 👋
31.03.2025 21:18 — 👍 0 🔁 0 💬 1 📌 0
@donnachab.bsky.social how do
26.03.2025 15:50 — 👍 0 🔁 0 💬 0 📌 0

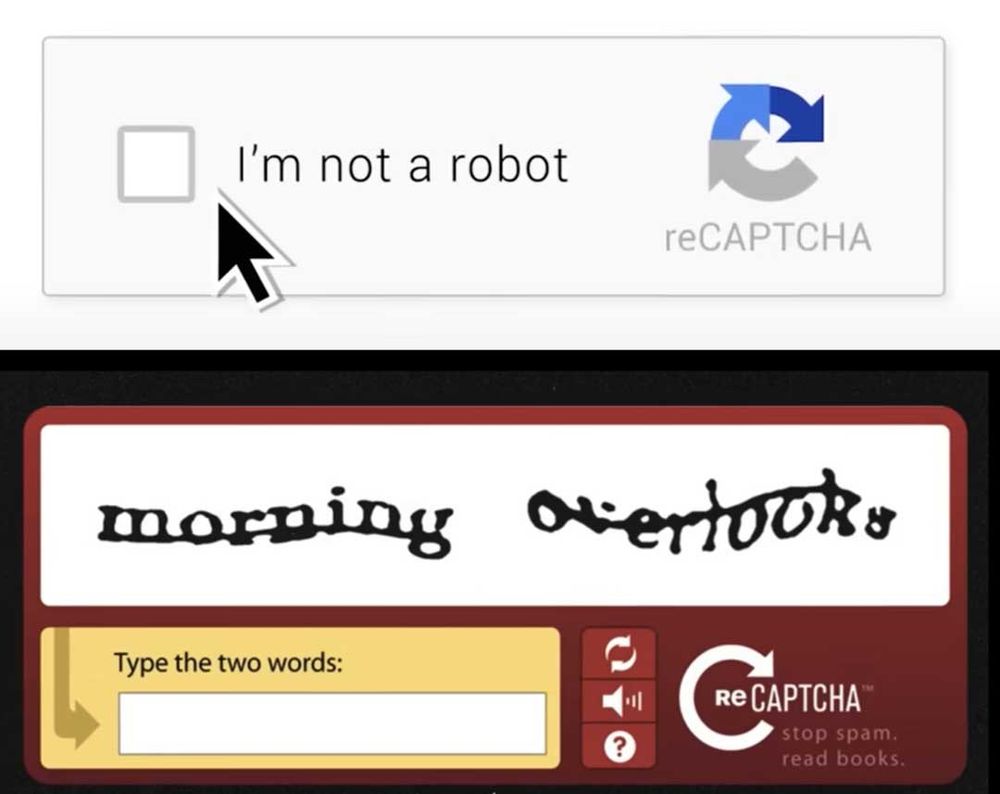
Searle's paper, titled "Dazed & Confused: A Large-Scale Real-World User Study of reCAPTCHAv2," found that Google's widely-used CAPTCHA system is primarily a mechanism for tracking user behavior and collecting data while providing little actual security against bots. The study revealed that reCAPTCHA extensively monitors users' cookies, browsing history, and browser environment (including canvas rendering, screen resolution, mouse movements, and user-agent data) — all of which can be used for advertising and tracking purposes. Through analyzing over 3,600 users, the researchers found that solving image-based challenges takes 557% longer than checkbox challenges and concluded that reCAPTCHA has cost society an estimated 819 million hours of human time valued at $6.1 billion in wages while generating massive profits for Google through its tracking capabilities and data collection, with the value of tracking cookies alone estimated at $888 billion.
Oh.
07.02.2025 15:36 — 👍 1247 🔁 500 💬 23 📌 66


Wonderful story. Deservedly on the front page.
24.01.2025 09:18 — 👍 1506 🔁 305 💬 30 📌 25
I've shared this quote before but I'll share it again, as it's one I've been thinking about a lot as I've watched how our oligarchs have been behaving over the past few months.
27.12.2024 23:07 — 👍 6682 🔁 2177 💬 129 📌 95
someone on tiktok said, “we’ve got 7 lex luthors and no superman,” and i can’t stop thinking about it
18.01.2025 22:57 — 👍 3038 🔁 734 💬 42 📌 33
Being a person with deadly, incurable cancer who is nonetheless still alive for an indefinite timeframe gives me an interesting metaphor that helps me deal with things like large-scale corruption in government or commerce.
Bear with me for a second while I try to explain.
21.01.2025 02:26 — 👍 14422 🔁 4521 💬 503 📌 1295
not Lynch's movie, I know, but god, what a sendoff
16.01.2025 18:34 — 👍 12620 🔁 3127 💬 150 📌 225

A Potential Modern Keyserver Network - Design Outline
A Potential Modern Keyserver Network - Design Outline - modern_keyservers.md
What started with me trying to teach myself OpenPGP and GnuPG led to a spiral of research piecing together what on Earth happened to keyservers, and has now resulted in my attempt to propose a new design outline for a keyserver network. Feel free to provide feedback!
gist.github.com/McDaMastR/d4...
13.01.2025 02:53 — 👍 2 🔁 1 💬 1 📌 0
Another wrinkle is that email challenge/response only works for email userids. While this is by far the most common form of userid it’s not a strict requirement. It may be possible to still tie them to an email address to prevent spamming - but the question is how. 🤯
18.01.2025 18:39 — 👍 1 🔁 0 💬 0 📌 0
(Aside: if you’re using a random number in a challenge-response protocol you have to store the random number in order to verify the response - in which case you can just use the random number alone as the challenge, no need for hashing the other data)
18.01.2025 18:35 — 👍 1 🔁 0 💬 1 📌 0
I think your ideas about email verification are useful. keys.openpgp.org already verifies emails, the real trick has been designing a way of doing this robustly in the sks network, in particular how do you prevent *every* keyserver from trying to email-verify the same key… 😵💫
18.01.2025 18:30 — 👍 1 🔁 0 💬 1 📌 0
Also, abusive keys can be blocked by adding their fingerprint to a list; there’s no need to revoke them.
18.01.2025 18:27 — 👍 1 🔁 0 💬 1 📌 0
Since hockeypuck 2.2, hard-revoked keys have their userids automatically deleted, as you suggest (this is not yet implemented on keys.openpgp.org).
18.01.2025 18:22 — 👍 1 🔁 0 💬 1 📌 0
Re your four responsibilities of a keyserver, we believe both keys.openpgp.org and the sks/hockeypuck network are compliant: image attributes are banned, and legal deletion requests are obeyed (and in the case of sks, forwarded to other operators).
18.01.2025 18:21 — 👍 1 🔁 0 💬 1 📌 0
🇺🇸🏳️🌈🏳️⚧️🥄❄️🐆👩🏽💻 in 🇦🇺🇨🇦 working on 🍯⬢🔭
Photographer of people and things.
British, But In Las Vegas and NYC
ezitron.76 Sig
Newsletter - wheresyoured.at
https://linktr.ee/betteroffline - podcast w/ iheartradio
Chosen by god, perfected by science
CEO at EZPR.com - Award-Winning Tech PR
Unvetted male Funkateer. Elevated neutrino readings. Talky stuff on
@newstalkFM @IrishTimesMag columnist. He/Him. 🇮🇪
Playwright & Actor
Reps. Writing: Curtis Brown. Acting: United UK & Lisa Richards IRL
https://linktr.ee/Emmetkirwan?fbclid=PAAaat-_vsdAnFapXO9hCuc6FR70ksrDJw7l-m7w4
19, Australian 🇦🇺 (he/him), AEST (UTC+10:00).
An autistic anti-fascist who appreciates the beauty of mathematics. Also loves Omori (especially Sunburn). And trans rights.
Part of the swarm 🐢
Pfp by Omocat.
#1 Sunday Times bestselling author, because apparently that matters. New Statesman, New World, Oh God What Now, The Newsletter of (Not Quite) Everything, Paper Cuts (RIP). Londoner. *Not* an American.
Communications. Space. Privacy. Black lives matter #BLM. Abortion is healthcare #freesafelegal. Abolish adoption #adopteerights. #FreePalestine. #BurnPatriarchy. Ireland is #NotFull. #MS is rubbish.
Berkeley professor, former Secretary of Labor. Co-founder of @inequalitymedia.bsky.social and @imcivicaction.bsky.social.
Substack: http://robertreich.substack.com
Buy my new book: https://sites.prh.com/reich
Visit my website: https://rbreich.com/
Lecturer for European Politics and History at King's College London. Opinions my own. RT not always endorsement.
Also to be found at @APHClarkson
https://www.ullstein.de/werke/die-macht-der-diaspora/hardcover/978354910
Psychologist, author, speaker. ADHD, autism, trauma. #ActuallyADHD, #ActuallyAutistic. Also cats. I like to think I'm funny. She/her
Best friend of @cmiriam.bsky.social
www.resiliencymentalhealth.com
https://linktr.ee/dramypsyd
SFF author (Planetfall sequence, Split Worlds series, The Vengeance), audiobook narrator, podcaster, tea drinker. Loves LARP, dressmaking and nerdery. Co-host of the Starship Alexandria podcast. www.linktr.ee/emma_newman
Author of award-winning bestseller An Irish Atlantic Rainforest. Almost 17 years living with 73 acres of wildland in Beara, West Cork. #Rewilding
Subscribe to my tech and online culture newsletter UserMag.co
Listen/watch Power User podcast on all platforms!!
Support my work on Patreon: https://www.patreon.com/cw/taylorlorenz
The Detail is an award winning investigative news and analysis website
https://thedetailni.substack.com/
Staff writer for the Atlantic. Host of the David Frum Show webcast. Formerly ... quite a lot of things.
Washington DC and Wellington, Ontario.
Reach me via Producer@TheDavidFrumShow.com
DMs open to followers
EU High Representative for Foreign Affairs and Security Policy
Vice-President of the European Commission
https://buymeacoffee.com/jayinkyiv