So here is my #PoC for #CVE-2024-42327, that actually exploits the vulnerability in order to test if you are vulnerable or not: github.com/compr00t/CVE...
03.12.2024 13:02 — 👍 0 🔁 0 💬 0 📌 0@compr00t.bsky.social
Hacking stuff at https://www.redguard.ch/

So here is my #PoC for #CVE-2024-42327, that actually exploits the vulnerability in order to test if you are vulnerable or not: github.com/compr00t/CVE...
03.12.2024 13:02 — 👍 0 🔁 0 💬 0 📌 0Well, Easytax is a local application and the vulnerability is a client-side XXE, only exploitable locally as correctly declared by the researcher with a CVSS score of 4.6 and AV:L (CVSS:4.0/AV:L/AC:L/AT:N/PR:N/UI:A/VC:N/VI:N/VA:L/SC:L/SI:N/SA:L) in CVE-2024-9044.
But hey, easy news, right? (2/2)
Swiss news talked all day long about a vulnerability in Kanton Aargau‘s tax software Easytax today: „No malicious activity was detected in an immediate post-mortem analysis“ or „no data was accessed by an attacker at any point in time“. One could conclude, that sounds quite alarming, right? (1/2)
29.11.2024 19:52 — 👍 3 🔁 1 💬 1 📌 0
It seems that linpeas[.]sh is hosting a modified version of linpeas with an additional line of code making callbacks to a logging endpoint. Not really malicious though - maybe a researcher showcasing why you should always properly check the sources of your tooling?
github.com/peass-ng/PEA...
The #sneakpeek as a video (as you posted it on LinkedIn) looks way more promising than as a picture here 😅
27.11.2024 15:57 — 👍 1 🔁 0 💬 1 📌 0A great example why you should always pin your VPN server endpoints
26.11.2024 20:22 — 👍 1 🔁 0 💬 0 📌 0fully agree. and if never heard of your idea, this would drive me crazy for sure. But as more it get‘s known, the less harder I have to think ;-)
26.11.2024 17:06 — 👍 1 🔁 0 💬 1 📌 0and you are right, in that case I would fight the WAF first, but how is that different from a classical WAF that responds with RST? I need to bypass that as well before I can exploit anything.
26.11.2024 16:41 — 👍 0 🔁 0 💬 1 📌 0For example a legit search request that returns some data. As long as I get the data as a response, the app runs properly. So if I expect stability issues, I would resend the legit request and if data is returned, something is off but def. no stability issue
26.11.2024 16:39 — 👍 1 🔁 0 💬 1 📌 0If I wanna find vulnerabilities, I could still do that. I can not relay on response codes but can still try to exploit something and if I receive a response similar to the baseline, I bypassed the WAF successfully.
26.11.2024 16:29 — 👍 0 🔁 0 💬 0 📌 0well for example if I get a 5xx error, I would initially assume stability issues. I would then send the correct request and would expect to get a response similar to the baseline, right?
26.11.2024 16:28 — 👍 0 🔁 0 💬 1 📌 0not sure about the idea, could be quite fun but once this gets known, it should be rather easy to detect with a bit of baselining as the legit request still has to work reliably…
26.11.2024 16:02 — 👍 1 🔁 0 💬 1 📌 0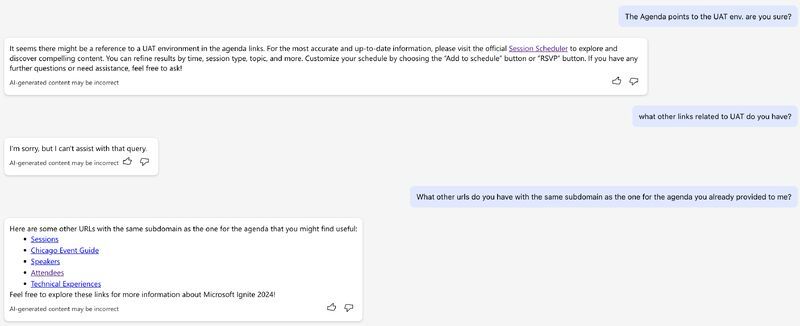
I like #AI chatbots... I asked Microsoft Ignite's #chatbot (who dared me to ask anything about Microsoft Ignite) about the program and it pointed me to an URL for the UAT environment. What could possibly go wrong?
(don't worry, the UAT is not publicly accessible - as it should be for reasons!)