
My colleague @rame has written a Burp extension that analyses HTTP header configurations. He introduces the extension in a blog post: https://www.scip.ch/en/?labs.20250911
11.09.2025 07:02 — 👍 0 🔁 1 💬 0 📌 0@0x6d69636b.bsky.social
infosec, working at scip AG, #RedTeam, classic car rally driver for teampaddymurphy.ie

My colleague @rame has written a Burp extension that analyses HTTP header configurations. He introduces the extension in a blog post: https://www.scip.ch/en/?labs.20250911
11.09.2025 07:02 — 👍 0 🔁 1 💬 0 📌 0Paddy wins the AvD-Histo-Tour 2025
After two second places and a third place, Paddy won the AvD-Histo-Tour 2025 in the Sanduhr category! He raced at the legendary Nordschleife, the Nürburgring Grand Prix Sprint race track, Circuit de Spa-Francorchamps, and Circuit Zolder. Good things come to […]
It's been almost a year since my last blog... So, here is a new one: Extending AD CS attack surface to the cloud with Intune certificates.
Also includes ESC1 over Intune (in some cases).
dirkjanm.io/extending-ad...
Oh, and a new tool for SCEP: github.com/dirkjanm/sce...
This is an article by my team colleague @m8r1us.bsky.social
12.06.2025 05:42 — 👍 0 🔁 0 💬 0 📌 0HardeningKitty updates:
* Support for Intune is a work in progress. I have implemented the first checks and updated a lot of findings
* Added CIS Benchmark lists for Windows 11 and Windows Server 2025
* The Windows 11 24H4 CIS list is the first to include Intune recommendations (though not yet […]

Only 2.4% of all CVEs have a CVSSv4 score and half of those is from one company
Another failed standard?
www.linkedin.com/feed/update/...
MATCH (c1:Computer)-[:MemberOf*1..]->(g:Group) WHERE g.objectsid ENDS WITH '-516' WITH COLLECT(c1[.]name) AS dcs MATCH (c2:Computer) WHERE c2.enabled = true AND (c2.operatingsystem contains '2025') AND (c2[.]name IN dcs) RETURN c2[.]name
If this query hits, you're DA: www.akamai.com/blog/securit...
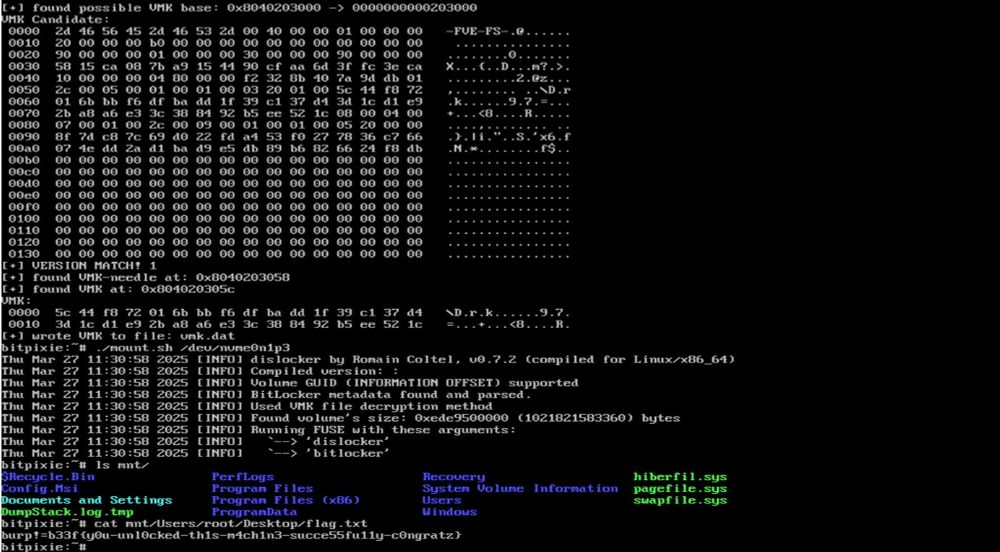
In his latest blog post, Marc Tanner @brain-dump.org shows how to bypass BitLocker using BitPixie (CVE-2023-21563) and signed Microsoft components only. Check out the blog post for a PoC and a demo. #BitLocker #RedTeam
blog.compass-security.com/2025/05/bypa...
Last weekend, Paddy was at the ACS Auto-Renntage 2025 in Frauenfeld: https://teampaddymurphy.ie/index.php?id=2025050101 #Volvo1800E #RaceDay #Racing
01.05.2025 09:48 — 👍 0 🔁 1 💬 0 📌 0Link to the article: teampaddymurphy.ie/index.php?id...
17.04.2025 05:40 — 👍 2 🔁 0 💬 0 📌 0Normally you can't auth to Entra ID connected webapps with bearer tokens. But if Teams can open SharePoint/OneDrive with an access token, I guess so can we. roadtx now supports opening SharePoint with access tokens in the embedded browser 😀
18.02.2025 13:12 — 👍 19 🔁 8 💬 1 📌 0
You need to run Rubeus, Seatbelt, or other .NET tool on an EDR protected machine?
Well with the new version, MacroPack Pro is now also a powerful assembly obfuscation/weaponization tool ! 😎
We wrote a tutorial about that here:
blog.balliskit.com/obfuscation-...

New HardeningKitty Version 🥳
https://github.com/0x6d69636b/windows_hardening/releases/tag/v.0.9.3
From the fediverse...
03.12.2024 13:09 — 👍 0 🔁 0 💬 0 📌 0Swiss news talked all day long about a vulnerability in Kanton Aargau‘s tax software Easytax today: „No malicious activity was detected in an immediate post-mortem analysis“ or „no data was accessed by an attacker at any point in time“. One could conclude, that sounds quite alarming, right? (1/2)
29.11.2024 19:52 — 👍 3 🔁 1 💬 1 📌 0New platform, who dis? It me, and @johnnyspandex.bsky.social dropping some VPN client exploit freshness! 🌮🔒
Today, we're releasing NachoVPN, our VPN client exploitation tool, as presented at SANS HackFest Hollywood. Get it on the @amberwolfsec.bsky.social blog:
blog.amberwolf.com/blog/2024/no...


Excited to share a tool I've been working on - ShadowHound.
ShadowHound is a PowerShell alternative to SharpHound for Active Directory enumeration, using native PowerShell or ADModule (ADWS). As a bonus I also talk about some MDI detections and how to avoid them.
blog.fndsec.net/2024/11/25/s...
RIP "Within this assessment, the red team (also referred to as ‘the team’) gained initial access through a web shell left from a third party’s previous security assessment."
www.cisa.gov/news-events/...

🥲
21.11.2024 13:47 — 👍 54 🔁 6 💬 2 📌 0Owning your own DNS and web and - gasp - even email - is a huge responsibility and more than ever a proving ground of learning how the world works. I encounter so many without this foundation and it costs them dearly. But it is a risk I can't recommend blindly.
19.11.2024 20:53 — 👍 71 🔁 5 💬 5 📌 1My Mastodon profile is now available on BlueSky: bsky.app/profile/misc...
Please follow that profile, I will mostly post there and do not cross post to keep your timeline clean ;-)
I want “red teaming”, why terminology matters and why not every client needs a red team assessment. My new article shows how we at scip AG define red teaming and our different approaches depending on an organisation's defence maturity level: www.scip.ch/en/?labs.202...
14.11.2024 06:01 — 👍 1 🔁 1 💬 0 📌 0I wrote a new article about an "unpopular" topic: Reporting and Documentation - Unpopular and yet so important
www.scip.ch/en/?labs.202...