I did a fun thing and gave every Belgian access to my AWS Account (or: playing around with IAM Roles Anywhere)
cloudar.be/awsblog/sign...
@vladionescu.me.bsky.social
sugarbaby cosplaying as a tech consultant • mean eastern european with unrealistically high expectations and unreasonable quality standards 🏳️🌈he/him🏳️🌈

I did a fun thing and gave every Belgian access to my AWS Account (or: playing around with IAM Roles Anywhere)
cloudar.be/awsblog/sign...
Wooo welcome to Bucharest 🎉👋🎉
19.06.2025 12:09 — 👍 2 🔁 0 💬 0 📌 0(I felt that I had to reply to this since I was a big fan of AVP's potential aaaaaand then I totally dissapeared from social media)
14.06.2025 09:41 — 👍 1 🔁 0 💬 0 📌 0AVP isn't a product that AWS takes seriously so I'd suggest also taking a look at Oso 😅
14.06.2025 09:37 — 👍 0 🔁 0 💬 1 📌 0Woooo 🎉🤗🎉
03.05.2025 19:42 — 👍 5 🔁 0 💬 0 📌 0
"To further cement the nexus between Microsoft and Europe, going forward our European datacenter operations and their boards will be overseen by a European board of directors that consists exclusively of European nationals and operates under European law."
blogs.microsoft.com/on-the-issue...
*hugs*
This was also (one of the reasons) I was driven away from social media / dramatically reduced my public web presence too. The tech community is wildly toxic but the open-source fanatics are... a particular level of abhorrent
Lol, I would argue that before moats they need an actual product first (you know, something that's not a short-lived feature arbitrage)
13.03.2025 13:25 — 👍 1 🔁 0 💬 0 📌 0Hey @rmondello.com, if I remember correctly you were collecting feedback for Passwords. Is that still a thing?
If yes, I have 1.5 feature requests targeting power-users.
If no, no worries! Passwords is still a heck of a lot more awesome than I expected and I will still fully migrate to it ❣️
It was all custom — some using GitHub Actions, some using custom tools.
18.11.2024 17:35 — 👍 7 🔁 0 💬 0 📌 0Still, this is not trivial to implement and, worse, this requires a serious company and serious developers (not only software engineers but product, testing, sales, support, etc).
That's surprisingly rare so... yeah, it'll remain a super-high-performing thing that few people talk about :(
A few teams measured this and the metrics after 6 months were *mindblowingly* better!
One exception: on-boarding slowed a bit :lolsob: It was so hard getting new devs in and having them get used to "no, seriously, if checks are green we ship whatever to prod and it's fine! We have intense checks!"
My answer: not enough tooling.
I worked with a bunch of teams that did post-PR code reviews (if the code is under a feature flag => PR is automatically approved, merged, and deployed to prod) but the setup required was non-trivial 😞
Everybody (including compliance) was super-happy with it tho!
🙋
22.10.2024 06:01 — 👍 1 🔁 0 💬 0 📌 0They fixed it, with impressive speed: the docs are now a lot clearer and even the changelog has been updated with additional details ❣️
AWS received feedback and they took super-prompt action to address it — awesome job AWS!
I was annoyed I was missing it but now I am properly devastated I won't be there 😭
16.09.2024 07:10 — 👍 1 🔁 0 💬 0 📌 0They have everything: from high-scale stuff (how delivery works at Tazz) to fast prototyping (prototype to prod in ~6 months with both tech and non-tech drama) to executive strategy, and so much more.
There's even a preview for re:Invent 2024!
Holy heck does the the agenda for AWS Community Day Romania look awesome 🤯
I mean I was expecting it to be *good* but I wan't expecting it to be *this good*. It's amazing!
aws-community.ro#agenda
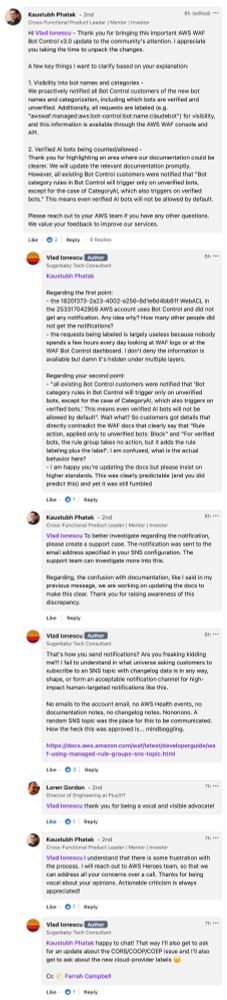
Fix is coming, as per the attached conversation with an AWS WAF PM.
15.09.2024 06:55 — 👍 2 🔁 0 💬 1 📌 0AWS WAF Bot Control moving bots from "un-verified" to "verified" means that bots that were previously blocked by default will now just get... counted.
Totally unexpected and not at all clear, right?
Don't you think this deserved a warning in the docs/announcement?
14/14
Folks can of course change the default actions but we all know the power of defaults.
See Internet Explorer, Apple, Google, Chrome, and all the new cases on this topic 🫠
13/14
By default, un-verified bots are a BLOCK.
If AWS WAF Bot Control doesn't know how to check the bot is indeed who it's saying it is, that means that it could be an attacker pretending to be a bot, so it is blocked by default.
12/14
By default, verified bots are a COUNT.
AWS WAF Bot Control is able to guarantee this is indeed the bot it's saying it is, so the request is neither blocked nor allowed.
11/14
Each AWS WAF rule/check can take one of 3 actions:
- BLOCK = immediately block this request
- ALLOW = immediately allow this request, do not run any of the next checks on the list
- COUNT = mark this request, and continue with the next checks in the list
10/14
AWS WAFs are, roughly, a list of rules/checks that are applied to every request that comes in.
The AWS WAF Bot Control is a list of these checks made specifically to check bots.
9/14
(Anthropic does not publish those IP addresses publicly but let's not get into that)
If both 1️⃣ and 2️⃣ check out, then it means the request is indeed from ClaudeBot and this is marked as a verified bot request.
8/14
When AWS WAF gets a request from something saying is Anthropic's ClaudeBot, AWS will check that:
1️⃣ the bot request looks like Anthropic told AWS it would look like
2️⃣ the bot request does indeed come from an IP address that Anthropic told AWS it uses to send bot requests
7/14
Side-note: bot verification means AWS does some checking to see that it's not some random person sending requests from their laptop pretending they're GoogleBot or Anthropic's ClaudeBot, for example.
6/14
It's unclear what bots exactly (you can ask and AWS might or might not tell you), but some AWS employees publicly hinted that Anthropic's ClaudeBot is included in the list 🤷
5/14
Do they make it clear what changed in the docs? No.
What actually changed was that AWS WAF Bot Control now supports bot verification for some bots in the following categories:
- CategoryAI
- SignalAutomatedBrowser
- SignalKnownBotDataCenter
- SignalNonBrowserUserAgent
4/14