One is the same as the other, plus IOCs.
14.12.2024 16:50 — 👍 1 🔁 0 💬 0 📌 0Mark Lechtik
@marklech.bsky.social
Senior TI Analyst @ MSTIC. Former Senior RE @ FLARE.
@marklech.bsky.social
Senior TI Analyst @ MSTIC. Former Senior RE @ FLARE.
One is the same as the other, plus IOCs.
14.12.2024 16:50 — 👍 1 🔁 0 💬 0 📌 0
BinaryDefense has published a technical analysis of the payload (Java webshell) dropped on hacked Cleo file transfer servers
www.binarydefense.com/resources/bl...
That smells like a Typhoon.
12.12.2024 23:55 — 👍 4 🔁 0 💬 1 📌 0Developing story - attack against #BGP peers of a European telco. The malicious emails impersonated that same telco and included the ASN of each recipient in the subject line.
The emails contained a password-protected RAR attachment with the malicious payload.
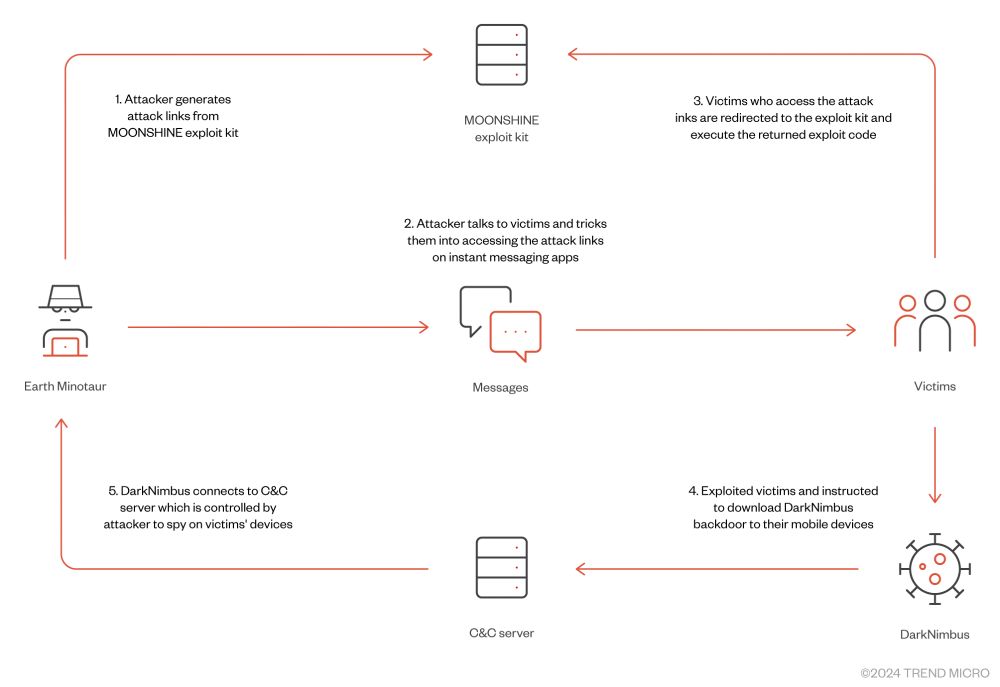
Attack chain showing attacker generating link on Moonshine, then sending it through targeted application to the victim, which after clicking the links gets compromised and delivered the DarkNimbus backdoor
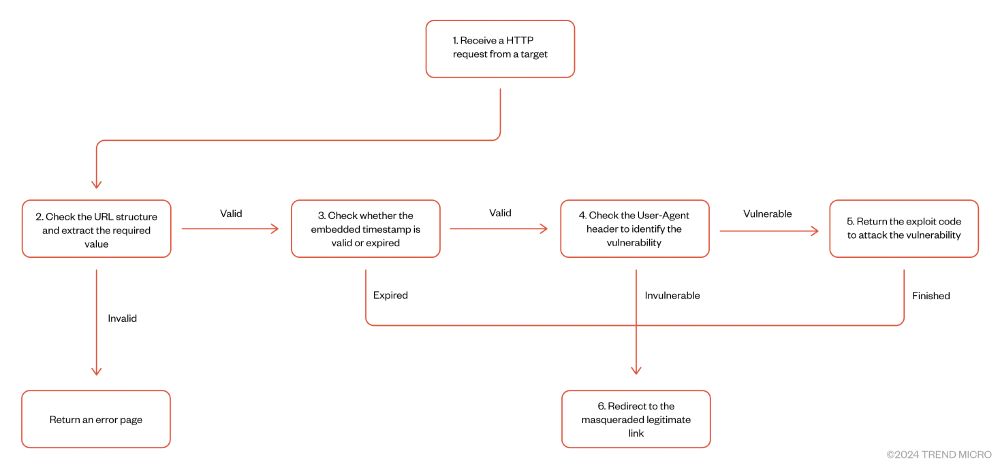
Validation flow that fingerprints the target by looking at user agent and delivering the proper exploit
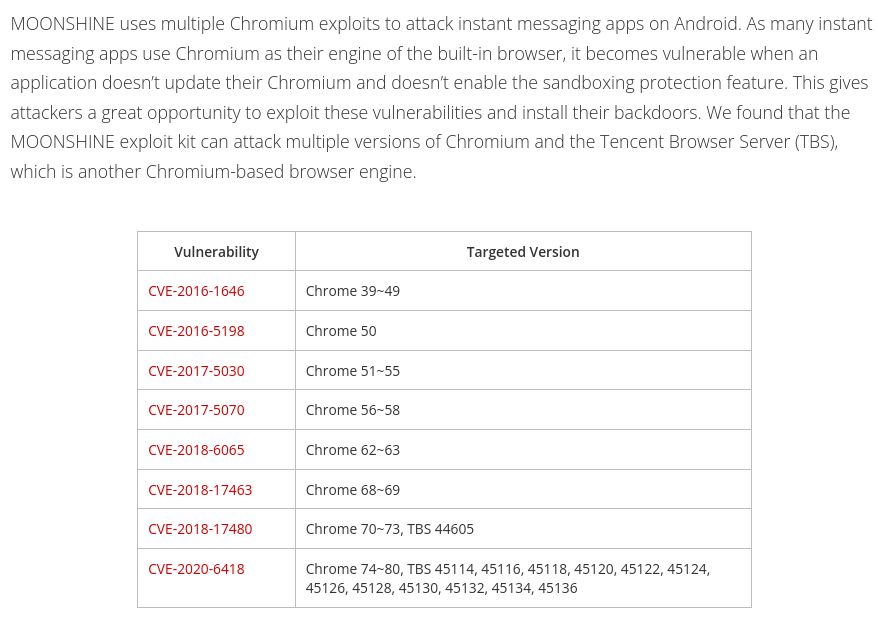
multiple Chrome vulnerabilities exploited in the third-party applications
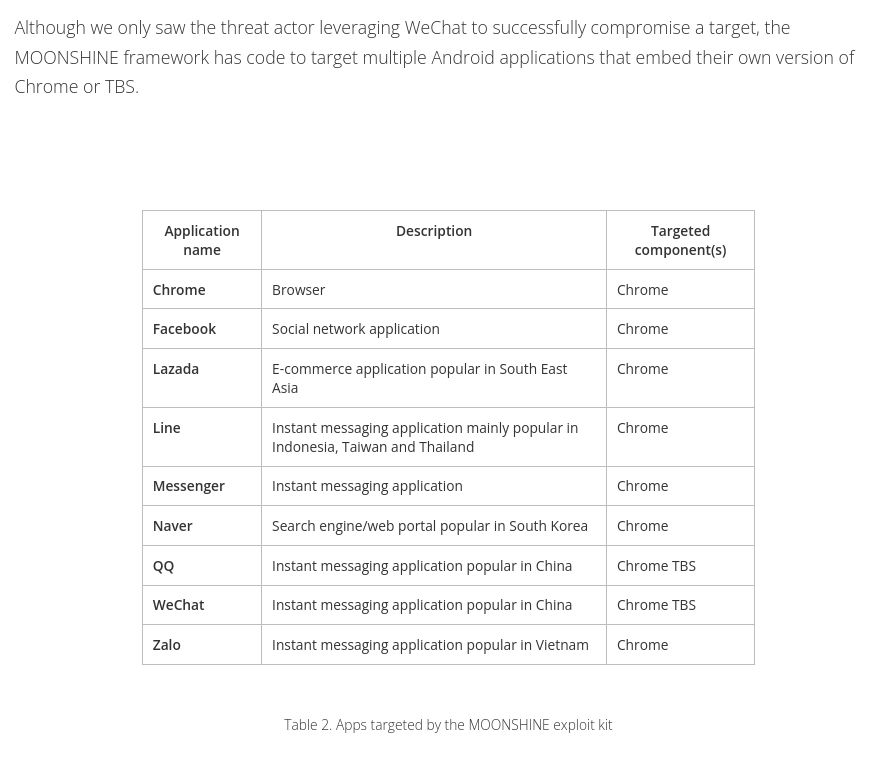
List of Android applications being targeted Most are very popular in South East Asia
Our latest report presents Earth Minotaur, a threat actor targeting Tibetans and Uyghurs using Moonshine, an exploitation framework for Android apps described in 2019 by
@citizenlab.ca
leveraging vulnerabilities in applications embedding old versions of Chromium trendmicro.com/en_us/resear...

@volexity.com’s latest blog post describes in detail how a Russian APT used a new attack technique, the “Nearest Neighbor Attack”, to leverage Wi-Fi networks in close proximity to the intended target while the attacker was halfway around the world.
Read more here: www.volexity.com/blog/2024/11...
#ESETresearch reveals the first Linux UEFI bootkit, Bootkitty. It disables kernel signature verification and preloads two ELFs unknown during our analysis. Also discovered, a possibly related unsigned LKM – both were uploaded to VT early this month. www.welivesecurity.com/en/eset-rese... 🧵
27.11.2024 08:34 — 👍 29 🔁 17 💬 1 📌 1