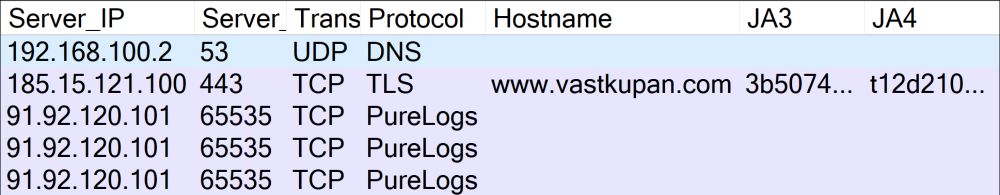
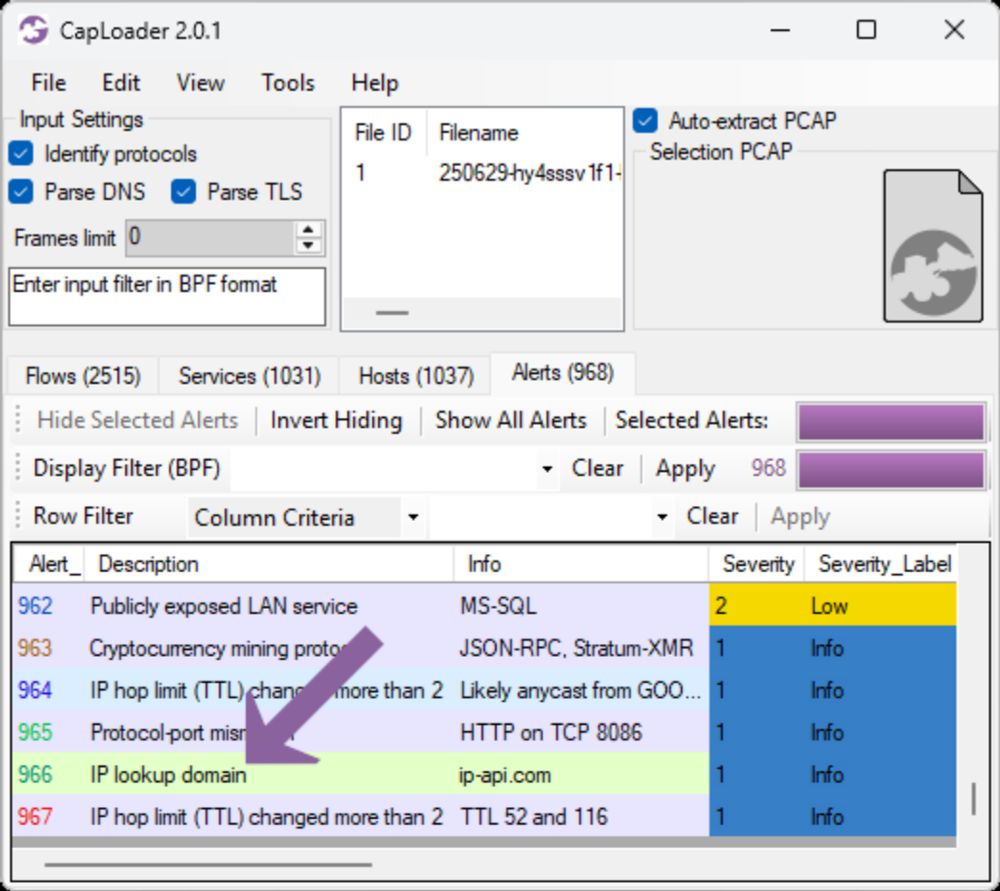
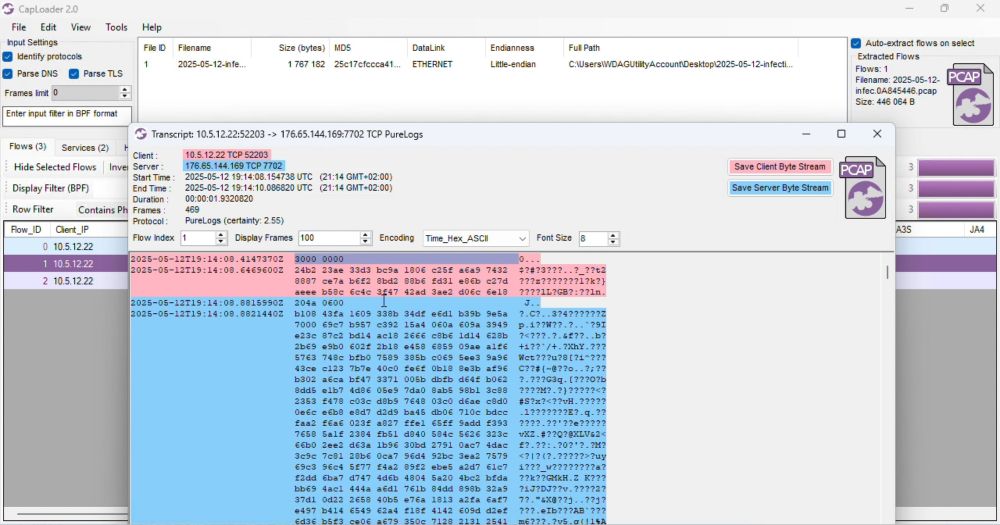
PureLogs Forensics
I analyzed some PureLogs malware infections this morning and found some interesting behavior and artifacts that I want to share. PureLogs infections sometimes start with a dropper/downloader that retr...
💧 Dropper connects to legitimate website
📄 Fake PDF is downloaded over HTTPS
💾 Fake PDF is decrypted to a #PureLogs DLL
⚙️ InstallUtil.exe or RegAsm.exe is started
💉 PureLogs DLL is injected into the running process
👾 PureLogs connects to C2 server
netresec.com?b=257eead
02.07.2025 12:15 — 👍 3 🔁 0 💬 0 📌 0
𝙽𝙴𝚃𝚁𝙴𝚂𝙴𝙲 (@netresec@infosec.exchange)
Attached: 1 image
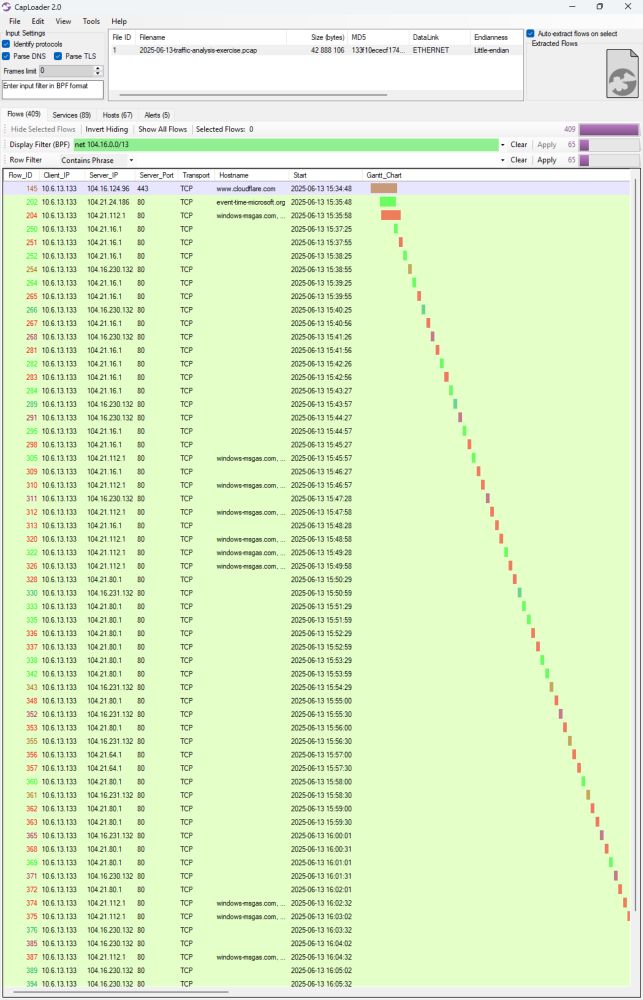
@malware_traffic There's some unknown but interesting C2 traffic going on to net 104.16.0.0/13 (on CloudFlare). An HTTP POST is sent every 30 seconds (see Gantt chart) with gz compr...
Does anyone know what malware this is? C2 is on 104.16.0.0/13 (CloudFlare).
C2 domains:
🔥 event-time-microsoft[.]org
🔥 windows-msgas[.]com
🔥 event-datamicrosoft[.]live
🔥 eventdata-microsoft[.]live
PCAP from @malware-traffic-analysis.net
infosec.exchange/@netresec/11...
24.06.2025 16:03 — 👍 2 🔁 0 💬 1 📌 0
![Many organizations may not need to allow outgoing traffic to hosting and API mocking services, which are frequently used by GRU unit 26165. Organizations should consider alerting on or blocking the following services, with exceptions allowlisted for legitimate activity [D3-DNSDL].
*.000[.]pe
*.1cooldns[.]com
*.42web[.]io
*.4cloud[.]click
*.accesscan[.]org
*.bumbleshrimp[.]com
*.camdvr[.]org
*.casacam[.]net
*.ddnsfree[.]com
*.ddnsgeek[.]com
*.ddnsguru[.]com
*.dynuddns[.]com
*.dynuddns[.]net
*.free[.]nf
*.freeddns[.]org
*.frge[.]io
*.glize[.]com
*.great-site[.]net
*.infinityfreeapp[.]com
*.kesug[.]com
*.loseyourip[.]com
*.lovestoblog[.]com
*.mockbin[.]io
*.mockbin[.]org
*.mocky[.]io
*.mybiolink[.]io
*.mysynology[.]net
*.mywire[.]org
*.ngrok[.]io
*.ooguy[.]com
*.pipedream[.]net
*.rf[.]gd
*.urlbae[.]com
*.webhook[.]site
*.webhookapp[.]com
*.webredirect[.]org
*.wuaze[.]com
Heuristic detections for web requests to new subdomains, including of the above providers, may uncover malicious phishing activity [D3-DNRA]. Logging the requests for each sub-domain requested by users on a network, such as in DNS or firewall logs, may enable system administrators to identify new targeting and victims.](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:2qrgzoyfwkguclususquvdz2/bafkreidsg3ldjaxglxhetka5xmbm2gc7xlthvuyoek2vmeo6ny5tsdi3di@jpeg)
Many organizations may not need to allow outgoing traffic to hosting and API mocking services, which are frequently used by GRU unit 26165. Organizations should consider alerting on or blocking the following services, with exceptions allowlisted for legitimate activity [D3-DNSDL].
*.000[.]pe
*.1cooldns[.]com
*.42web[.]io
*.4cloud[.]click
*.accesscan[.]org
*.bumbleshrimp[.]com
*.camdvr[.]org
*.casacam[.]net
*.ddnsfree[.]com
*.ddnsgeek[.]com
*.ddnsguru[.]com
*.dynuddns[.]com
*.dynuddns[.]net
*.free[.]nf
*.freeddns[.]org
*.frge[.]io
*.glize[.]com
*.great-site[.]net
*.infinityfreeapp[.]com
*.kesug[.]com
*.loseyourip[.]com
*.lovestoblog[.]com
*.mockbin[.]io
*.mockbin[.]org
*.mocky[.]io
*.mybiolink[.]io
*.mysynology[.]net
*.mywire[.]org
*.ngrok[.]io
*.ooguy[.]com
*.pipedream[.]net
*.rf[.]gd
*.urlbae[.]com
*.webhook[.]site
*.webhookapp[.]com
*.webredirect[.]org
*.wuaze[.]com
Heuristic detections for web requests to new subdomains, including of the above providers, may uncover malicious phishing activity [D3-DNRA]. Logging the requests for each sub-domain requested by users on a network, such as in DNS or firewall logs, may enable system administrators to identify new targeting and victims.
Thank you CISA, @ncsc.gov.uk, @bsi.bund.de et al. for publishing the advisory on Russian GRU Targeting Western Logistics Entities and Technology Companies. This list of mocking services is great for threat hunting!
www.cisa.gov/news-events/...
22.05.2025 17:16 — 👍 2 🔁 2 💬 0 📌 0
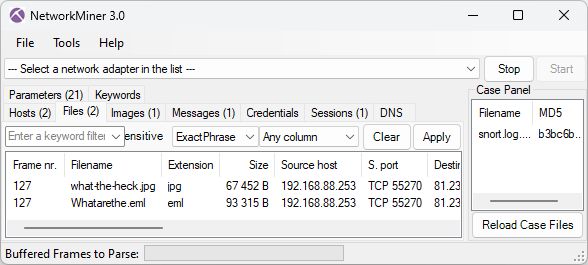
JPG and EML files extracted from SMTP traffic by NetworkMiner 3.0
NetworkMiner automatically extracts EML files as well as attachments (here a jpg image) to disk when it parses emails in SMTP, POP3 or IMAP traffic.
06.05.2025 06:25 — 👍 1 🔁 0 💬 0 📌 0
Yes! Wireshark's "Export Packet Bytes" feature can also be used to extract files inside of other data structures, such as attachments in emails.
06.05.2025 06:15 — 👍 0 🔁 0 💬 1 📌 0

Decoding njRAT traffic with NetworkMiner
I investigate network traffic from a Triage sandbox execution of njRAT in this video. The analysis is performed using NetworkMiner in Linux (REMnux to be specific). About njRAT / Bladabindi njRAT is a...
Did you know that NetworkMiner parses the #njRAT protocol? The following artefacts are extracted from njRAT C2 traffic:
🖥️ Screenshots of victim computer
📁 Transferred files
👾 Commands from C2 server
🤖 Replies from bot
🔑 Stolen credentials/passwords
⌨️ Keylog data
netresec.com?b=2541a39
28.04.2025 06:28 — 👍 6 🔁 2 💬 0 📌 0
LOL, Greenland has been a part of the Kingdom of Denmark since before USA even existed as a country!
10.04.2025 09:11 — 👍 1 🔁 0 💬 1 📌 0
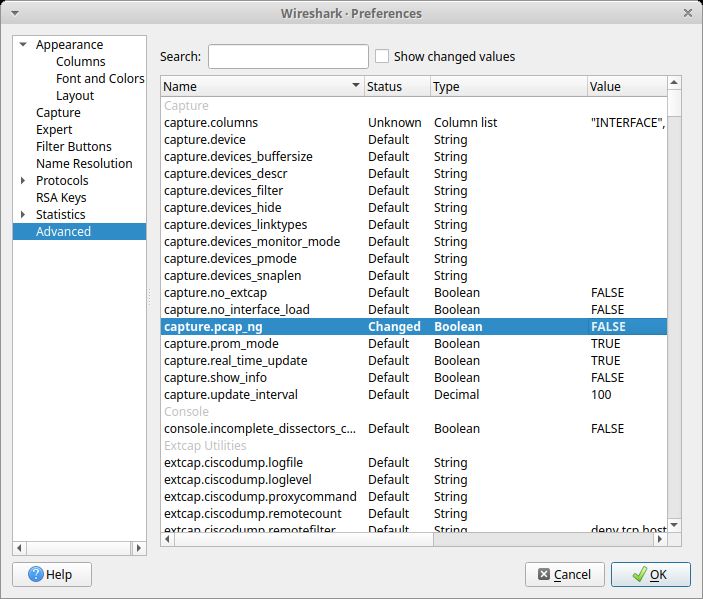
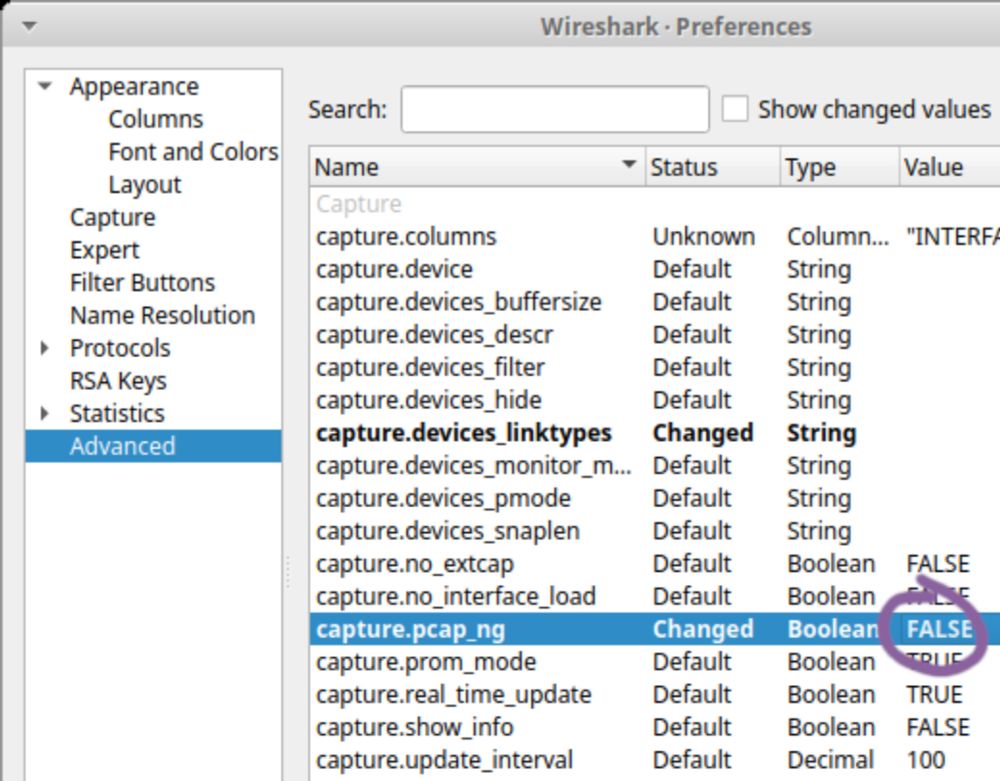
Setting capture.pcap_ng to FALSE in Wireshark's Edit, Preferences, Advanced let's you save capture files as .pcap instead of .pcapng as default.
That's a very useful feature! Thanks for sharing 🙏
24.02.2025 10:20 — 👍 2 🔁 0 💬 0 📌 0
Neat, just found out that @synacktiv.com are on Bluesky as well! Linking their original bsky post here.
29.01.2025 15:20 — 👍 1 🔁 0 💬 0 📌 0
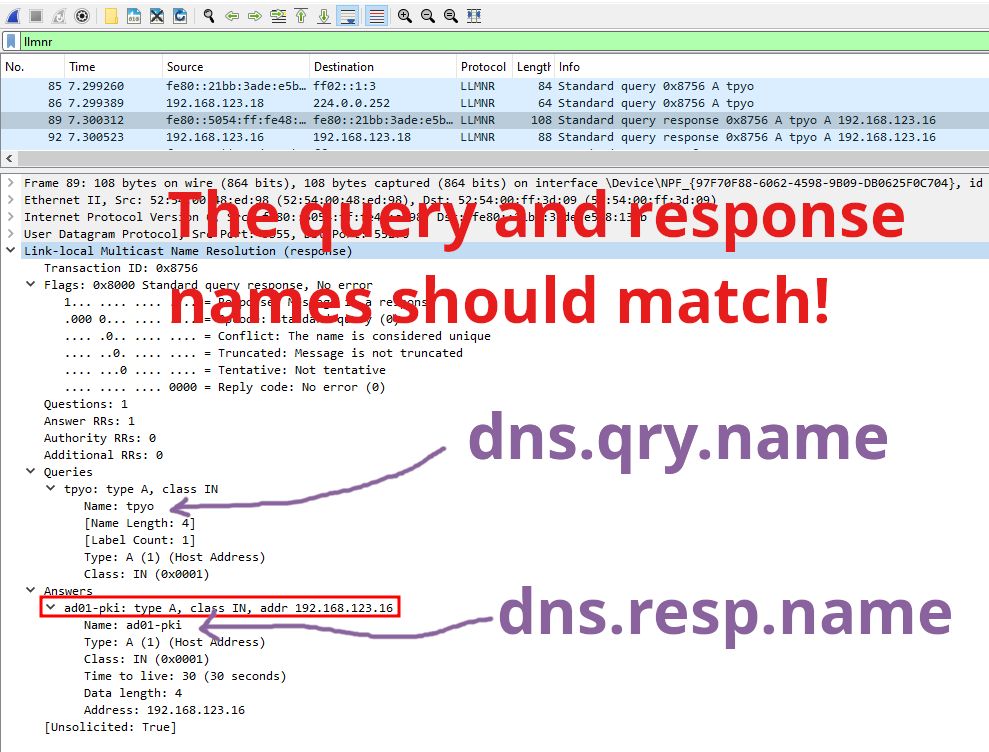
dns.qry.name should have the same value as dns.resp.name
Here's a Wireshark display filter for you:
dns.count.answers > 0 and lower(dns.qry.name) == lower(dns.resp.name)
Here's a Wireshark display filter that detects this type of LLMNR (multicast name resolution) spoofing:
dns.count.answers > 0 and lower(dns.qry.name) != lower(dns.resp.name)
29.01.2025 15:09 — 👍 6 🔁 3 💬 1 📌 0
This is an interesting Kerberos relay attack! It leverages LLMNR spoofing/poisoning to trick victims to connect to the attacker's machine and authenticate using Kerberos.
29.01.2025 15:09 — 👍 3 🔁 1 💬 1 📌 0
Filtering on the domain name is quicker since only the client request is needed to extract the hostname from the SNI extension.
27.01.2025 11:50 — 👍 0 🔁 0 💬 0 📌 0
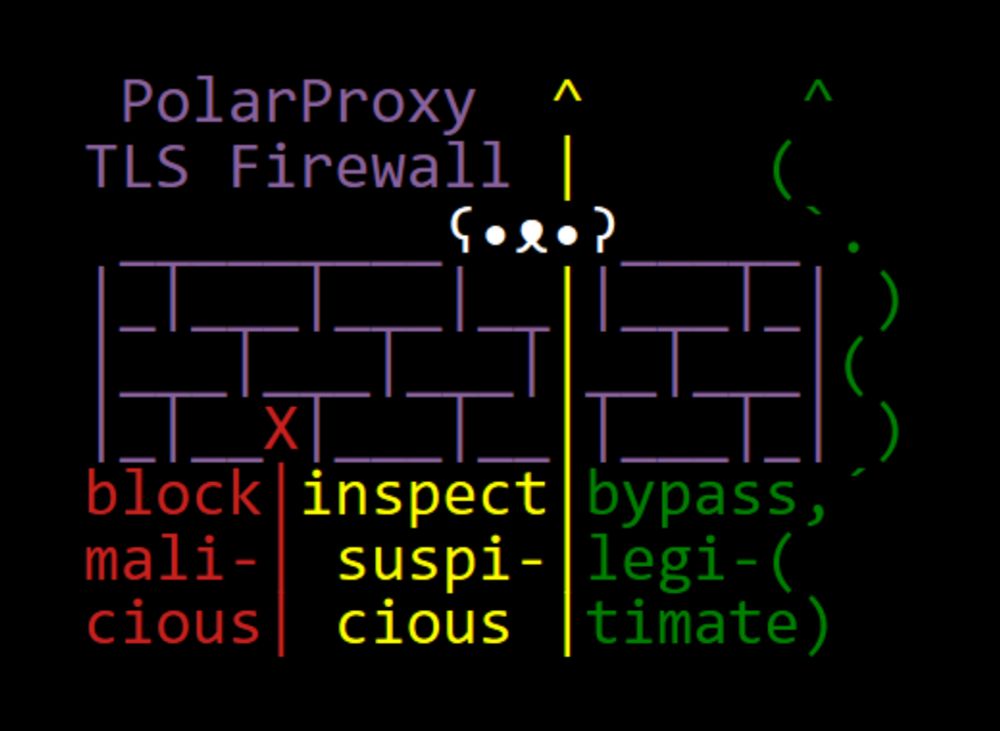
Interesting idea 🤔 That would technically be doable. One drawback is that the TLS firewall will have to wait for the server certificate before deciding whether to block it or not.
27.01.2025 11:50 — 👍 1 🔁 0 💬 1 📌 0
Covered Topics:
👾 C2 traffic analysis
🔓 Analyzing decrypted HTTPS traffic
↔️ Lateral movement
🎯 Threat Hunting
🔍 JA3 and JA4
🌐 Passive DNS
#DFIR #PCAP
20.12.2024 12:03 — 👍 1 🔁 0 💬 0 📌 0

Network Forensics Training
Upcoming Network Forensics Trainings and Classes from Netresec
We’ve now scheduled our next Network Forensics for Incident Response training
📅 Dates: May 12-15, 2025
🕑 Duration: Four half-days
🌐 Type: Live Online Network Forensics Training
💵 Price: € 960 EUR
www.netresec.com?page=Training
20.12.2024 12:03 — 👍 4 🔁 1 💬 1 📌 0
bsky.app/profile/Goss...
18.12.2024 18:27 — 👍 0 🔁 0 💬 0 📌 0

Original source: https://infosec.exchange/@cR0w/113239726857971779
#DirectoryTraversalMemes
18.12.2024 18:14 — 👍 5 🔁 0 💬 1 📌 0
CTI @wizsecurity.bsky.social
Previously NSC44, Mandiant, Google
Go Mammoths
Log enthusiast / espresso enthusiast / pizza maker / detection+observability engineering
We are the National Cyber Security Centre – part of the UK’s intelligence & cyber agency GCHQ. We help to make the UK the safest place to live and work online.
🛡️ Bundesamt für Sicherheit in der Informationstechnik
💻️ Cyber-Sicherheitsbehörde des Bundes
🤝 Wir sind das #TeamBSI
bsi.bund.de/Impressum | bsi.bund.de/dok/social-datenschutz
Principal analyst @vtxproject / #Synapse
#APT1 report / former Mandiant
Doing #threatintel before it was a thing
Fighting malware and botnets
Cybersecurity Specialist, Public Speaker, Ex-Hacker.
https://marcushutchins.com
Chief of DIFR at SoteriaSec | SANS Institute Principal Instructor | SANS FOR509 co-author | Director MDR Uptycs | Digital Forensics & Incident Response geek.
Experts in Network Forensics and Network Security Monitoring. Creators of #NetworkMiner, #CapLoader, #PolarProxy and #RawCap.
#PCAP or it didn't happen!
🌉 bridged from https://infosec.exchange/@netresec on the fediverse by https://fed.brid.gy/
https://strikeready.com/blog.html
Download live malware samples mentioned here: https://github.com/StrikeReady-Inc/samples
If you prefer marketing (our product is great!) subscribe to our main page @strikeready.com
Cybersecurity reporter at Bloomberg News in DC. Signal: @howelloneill.01, email: patoneill1@bloomberg.net
Information security practitioner.
All things cti collection.
Suricata IDS. An Open Source intrusion detection, intrusion prevention, and network security monitoring engine developed by the OISF (https://oisf.net).
Development by OISF team and our awesome community.
https://suricata.io
CEO and founder of runZero.com, previously the founder and lead developer of Metasploit, a CSO, a consultant, and the head of various security research teams. Contact info, presentations, and more at https://hdm.io/
Former USAF intel officer. Early info war practitioner. Created GE-CIRT. Mandiant's first CISO. #NetworkSecurityMonitoring for @corelight-inc. Author. Latest books #ad amzn.to/3B2AcMc
Zeek is an open source network security monitor. Visit www.zeek.org for more information.
Open Source Developer #Suricata #Vuurmuur #OSS #opensource
I'm also at:
https://mastodon.social/@inliniac
https://github.com/victorjulien
https://inliniac.net/
Founder of The Vertex Project (@vtxproject)
Father of the #APT1 Report @Mandiant.
Inventor of #synapse, #vivisect, UNCs, imphash, ...
DEFCON CTF Champion, Founder of Kenshoto



![Many organizations may not need to allow outgoing traffic to hosting and API mocking services, which are frequently used by GRU unit 26165. Organizations should consider alerting on or blocking the following services, with exceptions allowlisted for legitimate activity [D3-DNSDL].
*.000[.]pe
*.1cooldns[.]com
*.42web[.]io
*.4cloud[.]click
*.accesscan[.]org
*.bumbleshrimp[.]com
*.camdvr[.]org
*.casacam[.]net
*.ddnsfree[.]com
*.ddnsgeek[.]com
*.ddnsguru[.]com
*.dynuddns[.]com
*.dynuddns[.]net
*.free[.]nf
*.freeddns[.]org
*.frge[.]io
*.glize[.]com
*.great-site[.]net
*.infinityfreeapp[.]com
*.kesug[.]com
*.loseyourip[.]com
*.lovestoblog[.]com
*.mockbin[.]io
*.mockbin[.]org
*.mocky[.]io
*.mybiolink[.]io
*.mysynology[.]net
*.mywire[.]org
*.ngrok[.]io
*.ooguy[.]com
*.pipedream[.]net
*.rf[.]gd
*.urlbae[.]com
*.webhook[.]site
*.webhookapp[.]com
*.webredirect[.]org
*.wuaze[.]com
Heuristic detections for web requests to new subdomains, including of the above providers, may uncover malicious phishing activity [D3-DNRA]. Logging the requests for each sub-domain requested by users on a network, such as in DNS or firewall logs, may enable system administrators to identify new targeting and victims.](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:2qrgzoyfwkguclususquvdz2/bafkreidsg3ldjaxglxhetka5xmbm2gc7xlthvuyoek2vmeo6ny5tsdi3di@jpeg)