Please ask me to explain:
2-factor authentication fails to protect consumers.
It asks you to give your credentials without knowing who is on the other side.
That's what happens in help desk scams.
We must have *mutual* authentication in order to be truly secure.
You deserve it. We all do.
01.10.2025 19:42 — 👍 2 🔁 0 💬 0 📌 0
I remember that use case! Smart choice, discerning customers.
So nice to meet you!
19.09.2025 22:16 — 👍 2 🔁 0 💬 1 📌 0
Hi!
Yes! NFC technology! Much better than QR codes. Was that your invention? That's excellent.
Supply chain is a natural for blockchains, I agree. We're applying that concept to the information supply chain. We have mints without smart contracts (more secure) and global state awareness. 🥂
19.09.2025 21:16 — 👍 1 🔁 0 💬 0 📌 0
I'm glad to boost your public service announcements.
There's always something, please keep them coming!
Happy Friday.
19.09.2025 21:03 — 👍 1 🔁 0 💬 2 📌 0

✈️ Your Luggage Tag Could Be a Security Risk: Here's What Travelers Need to Know
That crumpled paper tag on your suitcase? It might be a golden ticket for scammers.
✈️ That crumpled luggage tag on your suitcase? It could be a scammer’s golden ticket. Learn how baggage tag fraud works and the simple steps to protect yourself when you fly.
👉 Read more: open.substack.com/pub/cyberlif...
#TravelSafety #Cybersecurity #AirTravel #FraudPrevention #Privacy
19.09.2025 19:44 — 👍 2 🔁 1 💬 1 📌 0
I retweeted this article, thank you!
I have a fix for this. Now I need to figure out how to sell it to an airline!
19.09.2025 20:43 — 👍 1 🔁 0 💬 2 📌 0
Very happy to answer!!
08.09.2025 13:50 — 👍 0 🔁 0 💬 0 📌 0
Awful.
Yet each phase sounds like the same problem. A spoof.
That's why I'd like our local public key infrastructure to be adopted.
Check the blockchain ledger for the public key of whoever is requesting contact with you. If it's not there, don't reply.
Lookup and challenge can be automated
01.09.2025 13:39 — 👍 0 🔁 0 💬 0 📌 0
Cool, yet another attack surface.
I'm working on a secure communications layer where the sender of the message must use a public key.
The recipient is able to identify the sender's signature and need only pay attention to those secret messages.
Do that first, then enjoy steganography.
01.09.2025 13:35 — 👍 0 🔁 0 💬 0 📌 0
Right!
I'm with Hank.
#cybersecurity
28.07.2025 18:06 — 👍 0 🔁 0 💬 0 📌 0
Glad to meet you, @1obit.bsky.social. Thank you for saying you're on the same wavelength. I hope others are too - it's hard to know when people stay quiet ... But I believe.
26.07.2025 13:16 — 👍 0 🔁 0 💬 0 📌 0
Should be required reading. Thanks for sharing it.
12.07.2025 03:25 — 👍 1 🔁 0 💬 0 📌 0
This is what we do. We're on a mission. geeq.io
08.07.2025 17:03 — 👍 0 🔁 0 💬 0 📌 0
Thank you very much, @at1c.bsky.social.
That's very helpful and encouraging. I will take your advice. 🙏
08.07.2025 17:02 — 👍 0 🔁 0 💬 0 📌 0
YouTube video by UCLA
Sara Bareilles: 2025 UCLA Commencement Speech
I adore her.
youtu.be/oHwb1MavsxE?...
28.06.2025 17:14 — 👍 0 🔁 0 💬 0 📌 0
Thanks for the warning.
14.06.2025 13:45 — 👍 0 🔁 0 💬 0 📌 0
Who is able to copy and preserve these kinds of records elsewhere?
I assume there's the actual data that was released, which is public fair use, but what about the other files and records derived from those?
Were releases signed that would allow reproduction elsewhere?
Or is that a pipedream?
07.06.2025 14:37 — 👍 2 🔁 0 💬 0 📌 0
Sometimes it goes the other way
07.06.2025 14:12 — 👍 0 🔁 0 💬 0 📌 0
It's a coordination issue.
I think we could re coordinate if there's a Blockchain equivalent where you could leave a forwarding address.
I could provide the back end at least as a pilot.
Would anyone write the app to get to an API and start the publicity?
05.06.2025 17:49 — 👍 0 🔁 0 💬 0 📌 0
intend to get into a debate about necessary or sufficient.
Of course that's all true. Nothing is guaranteed and I'd also like some luck:
"It's better to be lucky and stupid than unlucky and smart."
Overall, though, we've collected nearly all the pieces.
Nearly.
31.05.2025 22:23 — 👍 2 🔁 0 💬 1 📌 0
needed to find that last, simple, relatable pain that we can solve that people might understand.
I started out with an appreciation of what you said: that despite doing everything wrong, startups have a chance when they have something so excellent, they can focus on getting that right.
I didn't
31.05.2025 22:21 — 👍 0 🔁 0 💬 1 📌 0
Yes, except we have a business model because we know what infrastructure-as-a-service looks like.
We have a go-to-market but admittedly it hasn't been thoroughly tested. I've been patient, though, because I know we do cryptographic security so well, it's disruptive exactly as in ID, and I needed
31.05.2025 22:17 — 👍 0 🔁 0 💬 1 📌 0
Um, no thanks.
I don't like betting on anything that can make me high. ;)
31.05.2025 22:12 — 👍 2 🔁 0 💬 0 📌 0
A more charitable explanation might be there's no data. 😬
31.05.2025 21:49 — 👍 13 🔁 0 💬 2 📌 0
Thanks.
If you don't think 2-FA is a pain point, we obviously don't share the same world view!
What's going to happen when we need to authenticate AI agents - and differentiate them from one another?
Fingerprints? Or cryptographic keys?
Just a thought.
31.05.2025 21:38 — 👍 1 🔁 0 💬 1 📌 0
This is true.
31.05.2025 21:36 — 👍 0 🔁 0 💬 0 📌 0
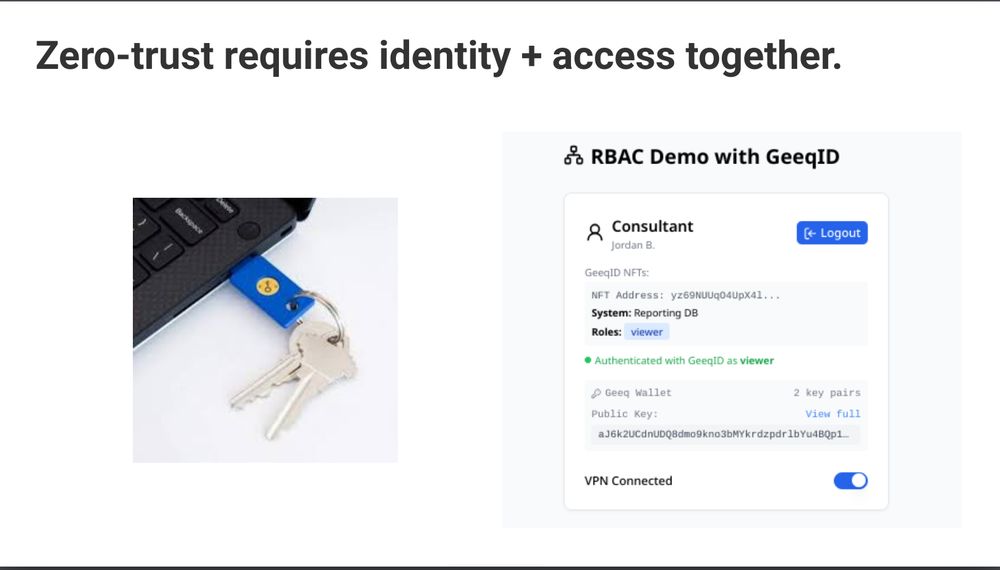
I am 100% ready for people to batter down my door now and give me money.
Please spread the word to anyone who invests in cybersecurity, Web3, and infrastructure-as-a-service, if you would.
I'm an economist, I understand gains from trade. This will be a very healthy one.
31.05.2025 21:12 — 👍 1 🔁 0 💬 1 📌 0
Because I hadn't asked them for it yet.
I've been listening and testing.
We have testnets out and it's taken me time to figure out first product and wedge.
First product is an easy to use, maximally secure replacement for 2-factor authentication that reduces friction for everyone who hates 2FA.
31.05.2025 21:07 — 👍 1 🔁 0 💬 2 📌 0
I was about to say .
31.05.2025 21:00 — 👍 4 🔁 0 💬 1 📌 0
Daily nuggets of software wisdom.
Follower of Jesus, Techie, Defender of the "least of these".
AI-Powered Full Spectrum Threat Intelligence
HackNotice empowers organizations to identify hidden dark web threats, supply chain risks, and emerging trends with real-time threat intelligence so they can drive faster, more effective incident response.
I draw.
hello@3daysmarch.net
https://www.3daysmarch.net
https://twitter.com/loika / https://andatsea.tumblr.com
https://shop.3daysmarch.net / https://patreon.com/loika
UALawSchool |MSNBC & NBCNews |Podcasts #SistersInLaw & Cafe Insider|Obama US Atty |25 year fed'l prosecutor|Wife & Mom of 4|Knits a lot|Civil Discourse newsletter: joycevance.substack.com
Bot highlighting changes to the New York Times "Top Stories" feed.
original by @j-e-d.bsky.social
Bluesky version by @unchi.org
Source: https://github.com/j-e-d/NYTdiff
I write about tech + humans + philosophy
https://www.joanwestenberg.com/
FORTRAN, Perl, and dotfile de-spaghettifier
she/they bi 🏳️⚧️ autist 📄 '89
GOP delenda est
Cofounder of https://indicator.media, your essential guide to understanding and investigating digital deception. Sign up for free! Investigative journalist and OSINT trainer.
https://craigsilverman.ca
Social Media Enthusiast 🦋
Exploring the world through trends, culture, science and technology.
Keyword, buzzword, half-truth, adjective, hey look at me! (founder of two unicorns: http://WPEngine.com, http://SmartBear.com).
Writing for 18 years at: https://longform.asmartbear.com
Recently: NYT, Polygon, The Stranger, Game Developer, Games Radar. Previously: Ars, American Airlines, The Atlantic. Clips + contact info: https://samred.com. He/him, from Seattle.
Aka @c_c_krebs over there
past: circus performer; historian of science; librarian; chief data officer at NEH.
present: dad; resident scholar at dartmouth; chief technology officer at the library of virginia.
personal account; views solely my own.
https://scottbot.github.io
Professional genealogist, former investigative journalist, living descendent of Revolutionary Patriots. Trump and his GOP thugs are not what they fought for. They are what they fought against. https://acolvingeo.wixsite.com/the-colvin-study
Recovering Lawyer. President, @chkbal.bsky.social. Host of the "George Conway Explains It All to Sarah Longwell" podcast on @thebulwark.com.
Econ professor at Michigan ● Senior fellow, Brookings and PIIE ● Intro econ textbook author ● Think Like An Economist podcast ● An economist willing to admit that the glass really is half full.
Activism Director at EFF, co-host of How to Fix the Internet podcast, quitter of Sekiro. An it harm none, regulate what thou wilt.
https://www.eff.org/about/staff/jason-kelley
THE Decentralized General Strike Network ✊ Uniting 3.5% (11 million Americans!) to actively participate in a STRIKE for economic & political reconstruction.
JOIN US: www.GeneralStrikeUS.com
LEARN MORE: https://linktr.ee/generalstrikeus
Yelling the truth about Tennessee.



