So, by EU CRA, incidents that happen to a product, like a device, affect its capability to protect its data and functions.
10.09.2025 15:41 — 👍 0 🔁 0 💬 0 📌 0
‘incident having an impact on the security of the product with digital elements’ means an incident that negatively
affects or is capable of negatively affecting the ability of a product with digital elements to protect the availability,
authenticity, integrity or confidentiality of data or functions
10.09.2025 15:38 — 👍 0 🔁 0 💬 1 📌 0
What about incidents related to products with digital elements (by EU CRA)?
10.09.2025 15:38 — 👍 0 🔁 0 💬 1 📌 0
In other words, 'incident' of EU CRA is defined in NIS2 Directive:
‘incident’ means an event compromising the availability, authenticity, integrity or confidentiality of stored, transmitted or processed data or of the services offered by, or accessible via, network and information systems;
10.09.2025 15:36 — 👍 0 🔁 0 💬 1 📌 0
By EU CRA, ‘incident’ means an incident as defined in Article 6, point (6), of Directive (EU) 2022/2555;
10.09.2025 15:34 — 👍 0 🔁 0 💬 1 📌 0
An incident is a security problem that requires action because it affects business operations or security objectives.
10.09.2025 15:32 — 👍 0 🔁 0 💬 0 📌 0
Difference between events and incidents:
Event - Any observable occurrence (e.g, a login attempt, a server restart, an email received)
Incident - An event (or series of events) that causes harm or poses a significant threat (e.g, repeated failed logins → brute-force attack → confirmed compromise)
10.09.2025 15:31 — 👍 0 🔁 0 💬 0 📌 0
Saying In more formal way: An incident is a confirmed occurrence of a security event that negatively impacts (or poses a credible threat to) an organization’s information systems, data, or services.
10.09.2025 15:27 — 👍 0 🔁 0 💬 0 📌 0
An incident meaning - In cybersecurity and IT operations, an incident means any event that:
a) Disrupts or has the potential to disrupt normal operations,
b) Threatens confidentiality, integrity, or availability of information, or
c) Violates security policies or acceptable use.
10.09.2025 15:26 — 👍 0 🔁 0 💬 4 📌 0
Gateways: Can be considered "products with digital elements" or components of "digital infrastructure".
Network servers: May be covered under NIS2 if offered as a critical service (e.g., in utility or smart city settings).
21.05.2025 16:56 — 👍 0 🔁 0 💬 0 📌 0
The LoRaWAN gateway and network server (e.g. ChirpStack, Actility) are also covered by EU CRA.
21.05.2025 16:47 — 👍 0 🔁 0 💬 0 📌 0
But what about the LoRaWan Gateway or Network Server?
21.05.2025 16:46 — 👍 0 🔁 0 💬 0 📌 0
For example: A LoRaWAN temperature sensor that transmits data via a LoRa gateway to a cloud dashboard is "a product with digital elements" under EU CRA.
21.05.2025 16:46 — 👍 0 🔁 0 💬 0 📌 0
From EU CRA-2-1: "This Regulation applies to products with digital elements made available on the market, the intended purpose or reasonably foreseeable use of which includes a direct or indirect logical or physical data connection to a device or network."
21.05.2025 16:45 — 👍 0 🔁 0 💬 0 📌 0
Under Article 2, paragraph 1 of the EU CRA, such devices are considered products with digital elements, even if they do not directly connect to the internet, and communicate only through gateways (as is common in LoRaWAN networks)
21.05.2025 16:44 — 👍 0 🔁 0 💬 0 📌 0
Yes, LoRaWAN End-Nodes — devices such as sensors, actuators, or embedded controllers that use LoRaWAN to transmit or receive data — are subject to the EU Cyber Resilience Act (EU CRA) if they meet the definition of a “product with digital elements”
21.05.2025 16:36 — 👍 0 🔁 0 💬 0 📌 0
How EU CRA affects LoRaWan End-Nodes? The ones that are beyond gateway. Are they subject to EU-CRA?
21.05.2025 16:34 — 👍 0 🔁 0 💬 7 📌 0
EUR-Lex - 32003H0361 - EN - EUR-LexLog inEnglish
Definitions under Recommendation 2003/361/EC:
* Micro enterprise: <10 employees & ≤ €2M turnover/balance sheet
* Small enterprise: <50 employees & ≤ €10M turnover/balance sheet
* Medium enterprise: <250 employees & ≤ €50M turnover or ≤ €43M balance sheet
Source: eur-lex.europa.eu/legal-conten...
14.05.2025 10:59 — 👍 1 🔁 0 💬 0 📌 0
In other words. Recommendation 2003/361/EC is a European Commission recommendation that defines the categories of micro, small, and medium-sized enterprises (SMEs).
14.05.2025 10:56 — 👍 0 🔁 0 💬 0 📌 0
‘microenterprises’, ‘small enterprises’ and ‘medium-sized enterprises’ mean, respectively, microenterprises, small
enterprises and medium-sized enterprises as defined in the Annex to Recommendation 2003/361/EC;
14.05.2025 10:55 — 👍 0 🔁 0 💬 0 📌 0
What is the "Recommendation 2003/361/EC" mentioned in the EU CRA?
It is defined in paragraph 19 of Article 3 "Definitions" of CHAPTER I "GENERAL PROVISIONS"
14.05.2025 10:55 — 👍 1 🔁 0 💬 3 📌 0
We can expect here that "the same specifications" must be available as a proper documentation by the company who provide and distribute the spare parts.
14.05.2025 10:51 — 👍 0 🔁 0 💬 0 📌 0
The EU CRA does not apply to spare parts that are made available on the market to replace identical components
in products with digital elements and that are manufactured according to the same specifications as the components that
they are intended to replace.
14.05.2025 10:49 — 👍 0 🔁 0 💬 1 📌 0
In this case, a heat pump makers are a device manufacturer offering a cloud-enabled service (sometimes called productized SaaS), not a dedicated SaaS provider like Microsoft or Salesforce. But their SaaS component still falls under CRA requirements for cybersecurity and secure development practices.
14.05.2025 10:34 — 👍 0 🔁 0 💬 0 📌 0
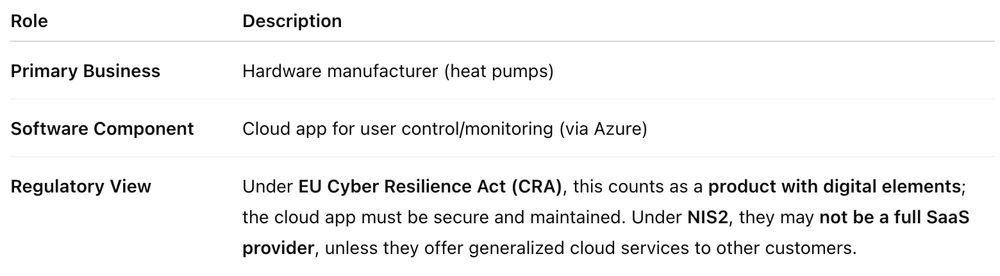
Here's the breakdown:
14.05.2025 10:32 — 👍 0 🔁 0 💬 0 📌 0
An example: If a heat pump manufacturer offers an Azure-based cloud application for users to remotely monitor or adjust heating, they are not strictly a SaaS company in the traditional sense — but they are offering a SaaS component as part of their connected product ecosystem.
14.05.2025 10:31 — 👍 0 🔁 0 💬 0 📌 0
But what does the EU CRA says about cloud services provided by a device manufacturer?
14.05.2025 10:31 — 👍 0 🔁 0 💬 0 📌 0
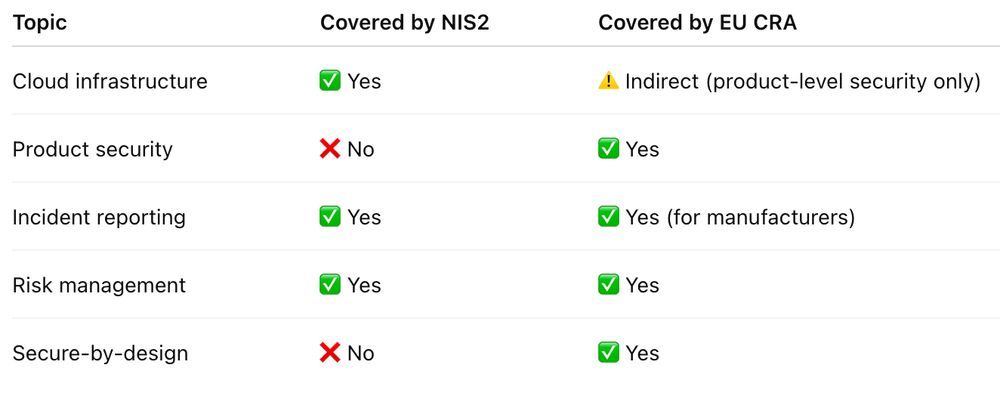
Directive (EU) 2022/2555 (NIS2) does apply to cloud computing services, regardless of whether they operate under IaaS, PaaS, or SaaS models.
While NIS2 focuses on service providers, the EU CRA complements it by regulating the security of digital products used in those services.
14.05.2025 10:14 — 👍 0 🔁 0 💬 0 📌 0
 14.05.2025 10:13 — 👍 0 🔁 0 💬 0 📌 0
14.05.2025 10:13 — 👍 0 🔁 0 💬 0 📌 0
While NIS2 focuses on the operational security of essential and important entities, the EU CRA targets the cybersecurity of products with digital elements (hardware & software). But they overlap.
14.05.2025 10:12 — 👍 0 🔁 0 💬 0 📌 0
Cpaphil.com : Vintage postcards shop, Cartes Postales, Ansichtskarten. More than 1.2 million items online. Enjoy !
Cpaphil.com:ヴィンテージポストカードショップ、カルト・ポスト・カルテ、アンスシュトカード
オンラインで120万点以上の商品を取り扱い中。お楽しみください!
In English, Francais, und Deutsch
www.cpaphil.com
The Self-Pub Hub (Indie Book Review Site)
Accepting book submissions now!
https://book-shelfie.com/submit-book/
Author, composer, keyboards. Author of the THE HIDDEN FACE
https://www.thriftbooks.com/w/the-hidden-face_m-i-verras/39420061/#edition=67723160&idiq=59042592
https://bookshop.org/p/books/the-hidden-face-m-i-verras/219927e81d5af327?ean=9798822921320&next=t
Cyber defender with an offensive name.
Deputy CTO at @onyphe.io | http://onyphe.io
Managing your attack surface... from Europe 👀
Opinions : all mine
Special skill : machine empathy
Master of (Keeping/Stealing) your Secrets | Security Advisor & Intel Analyst | Civil Servant @ BE | Klopjacht-speurder | IT Eng. + Pol. Sci. | Posts my own
Cybersecurity Analyst looking to network and expand my knowledge.
#cybersecurity #cyber #IT #WomeninTech
Real time comments about UK politics, media & news.
https://politicsintheuk.substack.com
Tory Hater, Reform Hater, Trump hater and Labour Supporter, Democrat supporter. #FBPE #Socialist #VoteBlue #BlewCrew #VoteLabour
Summarizes the hottest content on r/cybersecurity once per hour. Warning, the summaries are generated by an LLM and are not guaranteed to be 100% correct. Operated by @tweedge.net, open source @ https://github.com/r-cybersecurity/best-of-bot
👩💻 Talks and drinks among ladies to discuss all things InfoSec 🔑🇳🇱
womenofwicca.nl #WICCA_NL
Conference with an all-women speaker line-up designed to highlight women’s technical achievements in the cybersecurity field. -> wiccon.nl
🦑 The world’s first platform dedicated to comprehensive analysis of every New hacking technique.
Hackers Post Monitored by Undercode
Latest in Bug Bounty Tactics | Cybersecurity Tools Updates | AI & Courses
Critical Software + CNI Law | PhD Candidate at the University of Sydney | Fellow @ASPI-org.bsky.social | Associate Fellow at the Social Cyber Institute | Blogging @atechnolegalupdate.substack.com | Cricket, #Bloods | #KalikaMataKiJai
UK in a Changing Europe is an academic think tank providing impartial, research-based analysis of the critical issues facing the UK.
https://ukandeu.ac.uk/
Trade policy. Partner @ Flint Global. Senior visiting research fellow @ Kings College London.
I have a Substack: https://mostfavourednation.substack.com
Fixing the problems Britain faces after Brexit.
Change Minds → Change Politics
CEO @pimlicat.bsky.social
GUEST ~AA @SturdyAlex.bsky.social
CEO @bestforbritain.org
Podcaster @quietriotpod.bsky.social
NED @RoSPA
🇪🇺
European.
Views my own; RT = interest, not endorsement.
🇪🇺 Pro Europe and Scottish Independence
'𝑻𝒐 𝒔𝒕𝒓𝒊𝒗𝒆, 𝒕𝒐 𝒔𝒆𝒆𝒌, 𝒕𝒐 𝒇𝒊𝒏𝒅 𝒂𝒏𝒅 𝒏𝒐𝒕 𝒕𝒐 𝒚𝒊𝒆𝒍𝒅..', Ulysses, Tennyson.

 14.05.2025 10:13 — 👍 0 🔁 0 💬 0 📌 0
14.05.2025 10:13 — 👍 0 🔁 0 💬 0 📌 0